Cloud infrastructure has become an integral part of daily workloads for millions of organizations worldwide. After the sudden shift to remote work in 2020, cloud adoption is still in progress and, as this report proves, is expected to continue over the next 12-18 months (see How to Succeed Using the Power of the Cloud Technology?). Netwrix Research Lab has updated the Cloud Data Security Reports from 2020 and 2019 to reflect the evolution of cloud security. In 2022 Netwrix Research Lab surveyed 720 IT professionals all over the globe via an online questionnaire.
This report will help organizations concentrate their security efforts on what really matters and highlight the main obstacles on their way to safe cloud computing.

CLOUD ADOPTION
Organizations turned to the cloud mainly to reduce costs and to improve security. 80% of those who use the cloud store sensitive data there. The biggest challenge for cloud adoption, named by 41% of respondents, is in-tegration with their existing IT environment.
INCIDENT DETECTION
84% of respondents believe the time required to detect the incident either didn’t change or dropped. This is how they assessed their progress within the last year. A deeper dive reveals that the average detection time for most types of attacks has actually increased since 2020 (see What is Cloud Service?). The most sig-nificant slowdowns can be seen for discovery of supply chain compromise and ransomware attacks.
SECURITY INCIDENTS IN THE CLOUD
53% of survey respondents suffered a cyberattack within the last 12 months. Phishing was the most commonly expe-rienced incident – 73% of respondents confirmed that they had been victimized by this type of attack within the last year. Moreover, targeted attacks on cloud infrastructure increased significantly: 29% of respondents suffered this type of attack in 2022, compared to 16% in 2020.
DATA BREACH CONSEQUENCES
Data breaches are getting costlier. This year, 49% of re-spondents said that an attack led to unplanned expens-es to fix security gaps, up from 28% in 2020. The share who faced compliance fines more than doubled (from 11% to 25%), as did the number who watched as their company valuation dropped (from 7% to 17%).
CLOUD SECURITY MEASURES
More than half (55%) of respondents said that external actors are the main threat for their IT environment. Mul-tifactor authentication (MFA) and cloud backup topped the list of protection measures. Both saw increases since 2020: MFA adoption grew from 57% to 69% and backups increased, albeit marginally, from 58% to 63%.
BUDGETING
49% of our respondents stated that their budget for cloud security increased in 2022. Moreover, organizations are de-voting more of their larger cybersecurity budgets to cloud security: On average, 32% of the cybersecurity budget is now spent on cloud security, compared to 27% in 2020. This means a 23% increase of money being spent on cloud security in 2022 than in 2020.
Cloud adoption goals and challenges
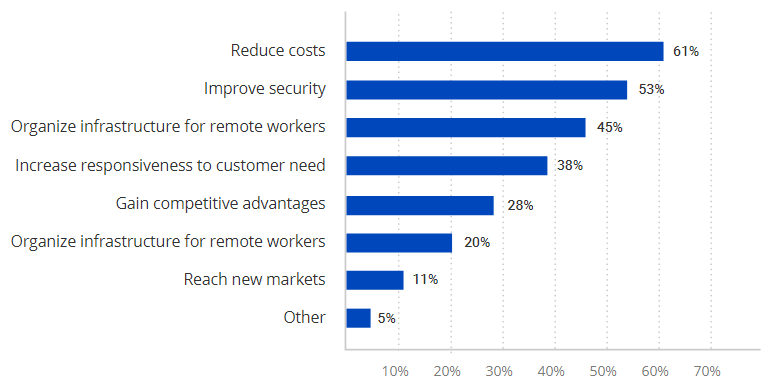
The survey found that the top two goals of cloud adoption are to reduce costs and improve security. Supporting remote workers ranked third, which indicates that the pandemic may have accelerated cloud adoption, but cost-ef-ficiency and security are the most significant drivers.
Primary cloud adoption goals
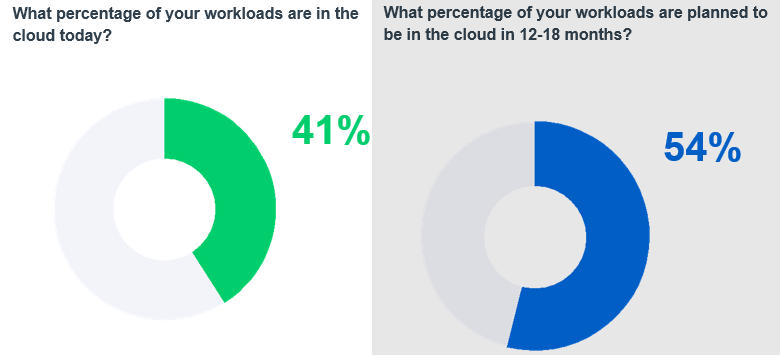
What’s in the cloud?
On average, organizations report that 41% of their workloads are already in the cloud, and they expect that share to increase to 54% by the end of 2023.
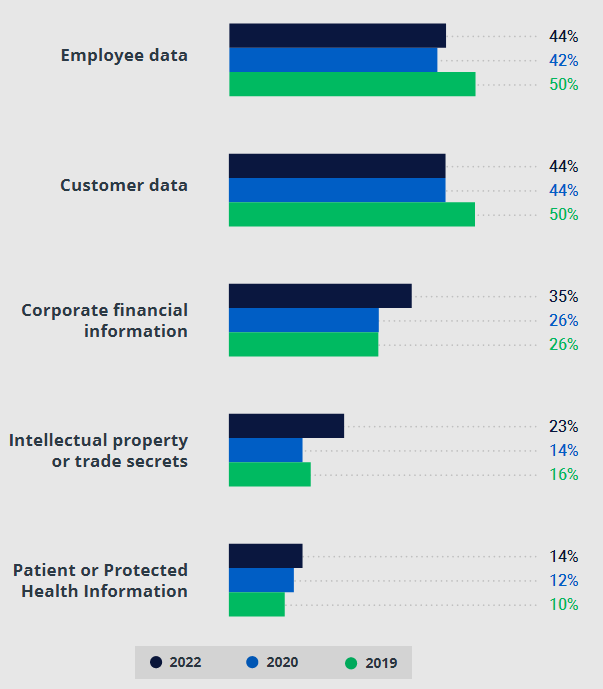
Storage of sensitive data in the cloud hasn’t changed much since the pandemic hit in 2020; however, the numbers for the two top categories are still lower than they were in 2019.
For example, the percentage of organizations storing customer data in the cloud dropped from 50% in 2019 to 44% in 2020 and then remained level in 2022; employee data dropped from 50% in 2019 to 42% in 2020, and then inched up to 44% in 2022.
On the other hand, the share of those who store corporate financial information in the cloud rose from 26% in 2019 and 2020 to 35% in 2022.
In 2019, cloud adoption seemed like a magic wand that would reduce costs, increase flexibility, and accelerate business processes. But with the abrupt shift to remote work in 2020, IT teams reassessed the risks and pulled some customer and employee PII back on premises, a trend that plateaued in 2022.
However, more organizations now store other types of sensitive data, such as corporate financial data and IP, in the cloud than before, which shows that IT teams believe that they have improved their cloud skills and learned how to use it effectively and securely.
80% of respondents store sensitive data in the cloud. The most common types are the PII of employees and the PII of customers.
Types of sensitive data organizations store in the cloud
Only 20% of organizations which use the cloud don’t store any sensitive data there
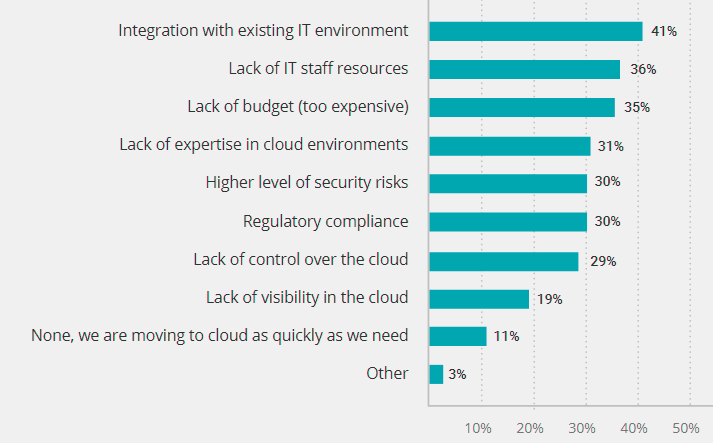
The biggest challenge for rapid cloud adoption, named by 41% of respondents, is integration with their exist-ing IT environment. The second factor impeding the process is lack of IT staff.
What are the biggest cloud challenges?
Reducing costs is the primary reason to move to the cloud for 61% of respondents, but 35% said that the expense of cloud adoption has slowed their move to the cloud.
This is a tricky thing about cloud infrastruc-ture: Cloud and on-premises infrastructures are too different to try and just move every workload as is; in-deed, a lift-and-shift approach can lead to significant extra expenses and even require costly architecture redesign if issues are found late in the process.
For example, if you have an application that relies on a SQL backend, it is possible to reproduce it exactly in the cloud with a virtual machine running Microsoft SQL Server.
However, this will likely be both the least efficient and the most expensive architecture you can think of. From this perspective, it seems that some of the respondents who say their cloud migra-tion was too expensive might lack sufficient expertise with cloud environments.
Still, the expense of a cloud infrastructure can be harder to predict than those in an on-premises envi-ronment.
When you need a server, the cost calculation is rather easy: Add together the price of the server itself, the electricity, the IT team salary. When it comes to the cloud, you receive a bill for the amount of resources used for actual workload.
Without controls in place, consumption and the bill will increase every month. That is why it’s crucial to keep an eye on what the organization currently needs and maintain a flexible architecture so you can turn off and on the relevant cloud options.
Factors that slow down cloud adoption
The biggest issues for CIOs are lack of expertise in cloud and integration with existing IT environment – these reasons topped the list for 33% of CIOs asked. 25% of CISOs are unsatisfied with their organization’s cloud security.
Security incidents in the cloud
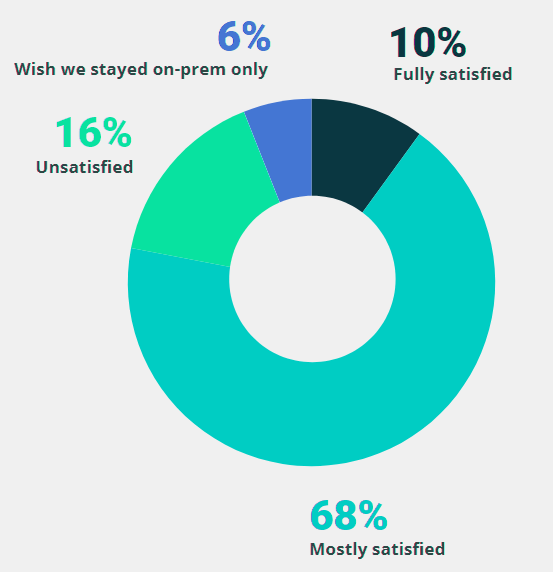
More than half (53%) of respondents picked security improvement as their main goal for the cloud adoption. And it looks like they achieved that objective: 78% of respondents say they are satisfied with their organization’s cloud secu-rity.
Satisfaction with cloud security
Attacks in the cloud
53% of survey respondents suffered a cyberattack within the last 12 months. Security professionals know that it’s impossible to achieve full cybersecurity, which means that the remaining 47% had a very lucky year — or just haven’t discovered the incident yet.
We asked those who experienced cyberattacks to pro-vide details on what happened and compared these answers with the results from 2020.
Most common cloud security incidents
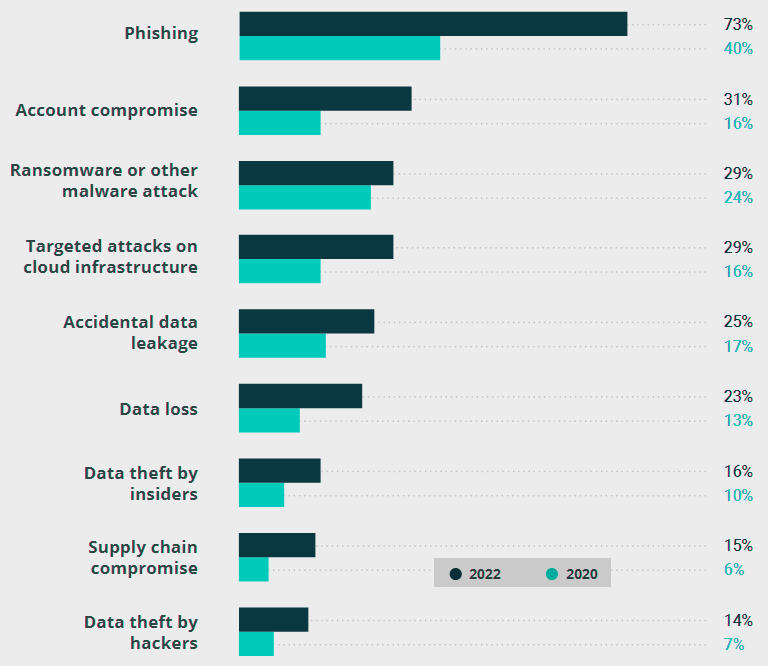
Phishing was the most commonly experienced incident. Although it was also the leader in 2020, the percentage of organizations that suffered this type of attack nearly doubled, from 40% to 73%. Moreover, 63% of respon-dents said they experienced this type of an attack mul-tiple times (see Using AI, Analytics & Cloud to Reimagine the Insurance Value Chain).
Targeted attacks on cloud infrastructure also increased significantly: 29% of respondents suffered this type of attack in 2022, compared to 16% in 2020.
This stands to reason since the more workloads that are moved to the cloud, the more targeted attacks on cloud environ-ments we will see.
In 2022, 31% of respondents said they experienced a compromised account, up from only 16% in 2020. This could be the result of negligence by remote workers (e.g., logging in through public Wi-Fi) and a wider attack surface due to necessity of granting remote access to many people.
Moreover, people often use the same — and not always strong — password for several resources and resist multifactor authentication because they find it annoying.
In 2022, the third most common type of attack was ransomware or other malware. The share of respondents who experienced such incidents increased slightly since 2020, from 24% to 29%, and is in Top-3.
The number of attacks increased globally in part because cryptocurrency gave threat actors a far less traceable way of receiving ransom money. Moreover, ransomware-as-a-service now makes it easy to scale this ‘business’.
Detection time
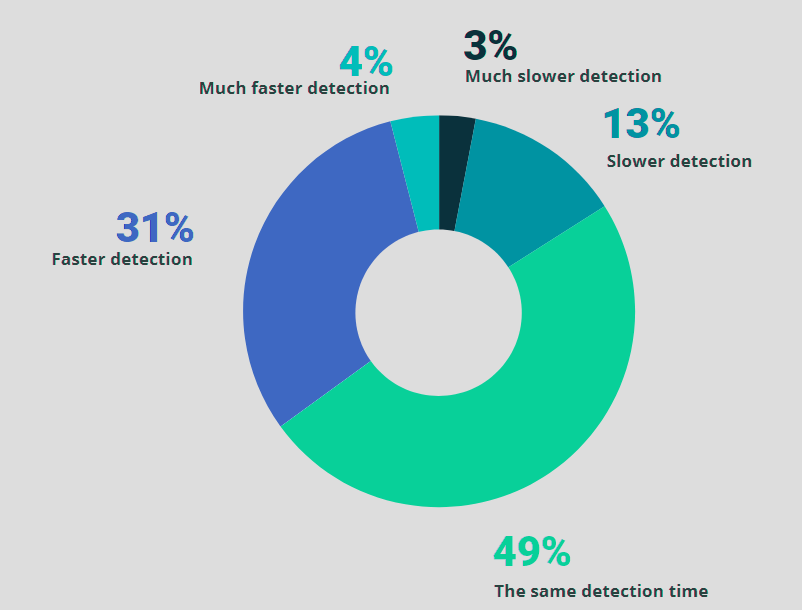
Next, we asked whether the time required to detect an incident in the cloud changed compared to 12 months ago. More than a third of the respondents (35%) said that detection is now faster, while 49% said detection time hasn’t changed.
Change in incident detection time
To dive deeper, we asked respondents how much time it took to discover and respond to the cloud security incidents they suffered in the past 12 months. The chart below compares those results with the data from 2020 to show which types of attacks have become easier to discover.
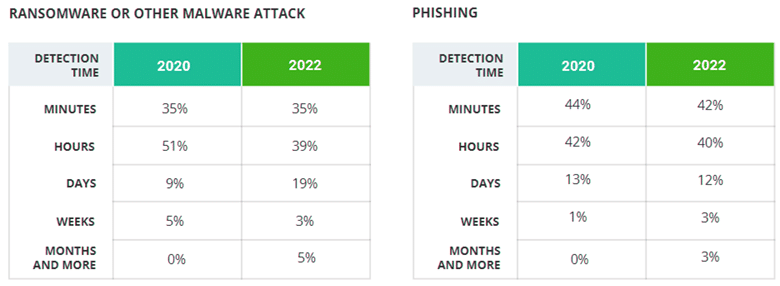
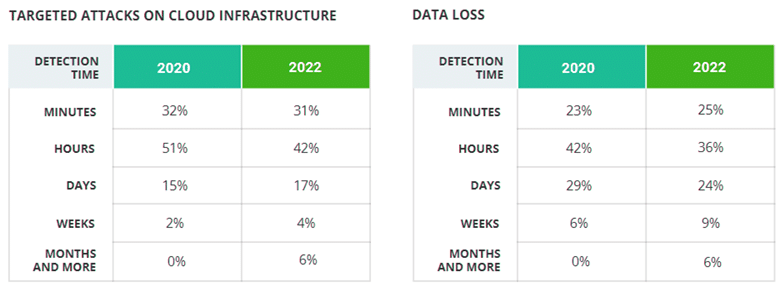
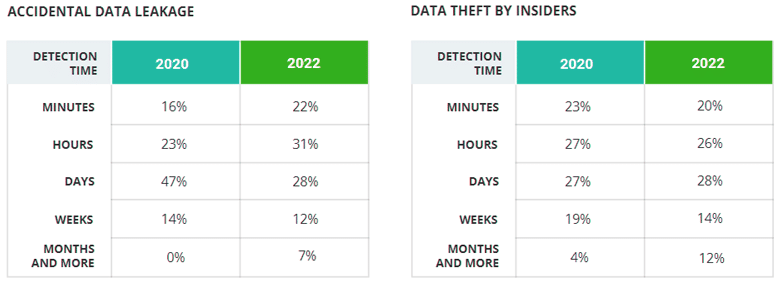
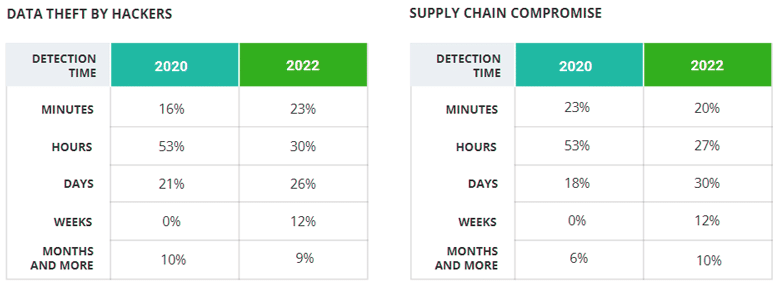
In response to the previous question, 84% of respon-dents said the time required to detect the incident ei-ther didn’t change or was reduced — but this deeper dive reveals that the average detection time for most types of the attacks has actually increased since 2020. The most significant slowdowns can be seen for dis-covery of supply chain compromise and ransomware attacks.
Moreover, in 2020, only three types of attacks took months or more to be discovered; in 2022, every type of attack has a share of respondents who needed months or more to detect.
We do see progress for several attack types. 53% of respondents needed minutes or hours to detect ac-cidental data leakage, versus just 39% in 2020. And the number of respondents who discovered account compromise in minutes increased from 20% in 2020 to 30% in 2022.
One way to solve this problem is to reduce the number of vendors and build the security architecture with a select group of trusted vendors, whose extensive portfolio of products do complement each other, and that are committed to collaboration across portfolio boundaries.
These results mean that attacks have become more sophisticated and harder to spot. Despite all the new tools that provide more visibility to security teams, it is still a challenge to detect signs of a threat actor in the IT environment. Point solutions leave security gaps as they operate separately.
Data breach consequences

Not every attack is catastrophic. The truth is that in 32% of cases, the attack has no impact on business. However, that is a significant drop from 49% in 2020.
Data breach consequences
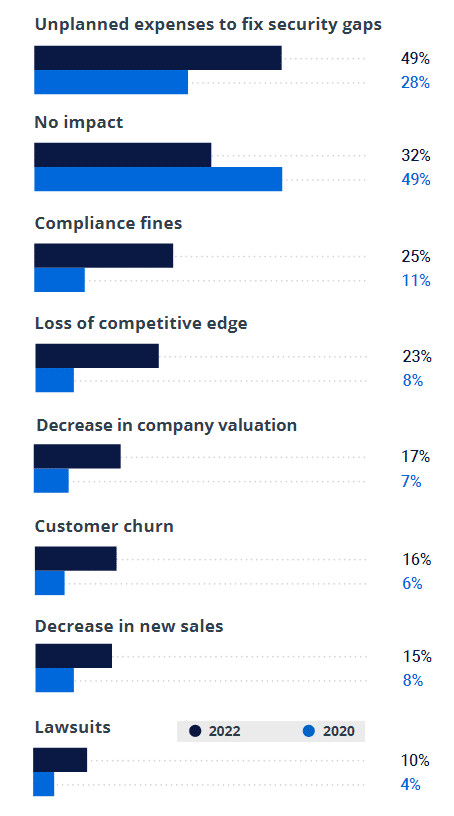
Data breaches are getting costlier. This year, 49% of respondents said that an attack led to unplanned expenses to fix security gaps, up from 28% in 2020. Similarly, those who faced compliance fines more than doubled (from 11% to 25%), as did the number who saw their company valuation drop (from 7% to 17%).
Organizations shifting their value-generating processes to the cloud should be conscious of such statistics.
These results should help CIOs and CISOs prove the necessity of additional budget to keep their organization safe. A resilient cybersecurity costs less than consequences of data breaches.
Our respondents take their responsibilities very serious, so we added in a bit of levity to this year’s survey just to ease the pressure for a moment. We asked how devastating would the breach be if happened in their cloud data storage.
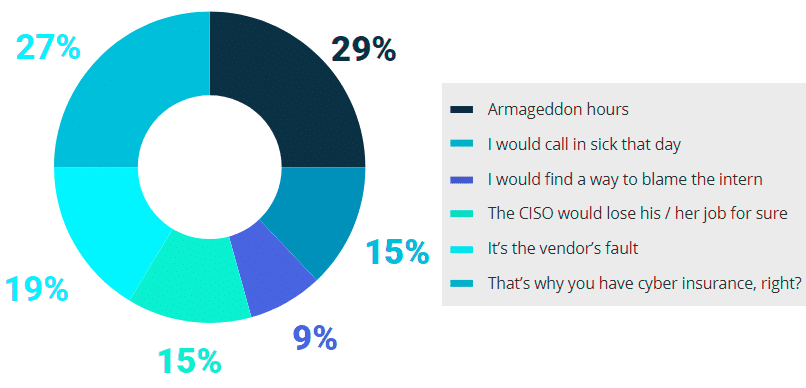
IT pros are no strangers to a good laugh. One respondent commented: “Data breach consequences? Some ser-vices do not work, so I will go to the beach.” We admire the ability of security professionals to keep their calm (and a sense of humor) under any circumstances.
How much did the breach cost?
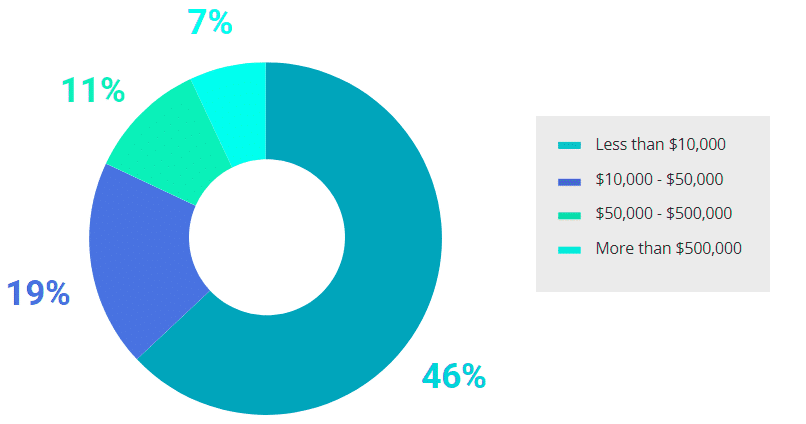
Considering that 32% didn’t see any impact on their business from the incidents they suffered, it is no surprise that most respondents (63%) estimated the harm from a data breach at less than $10,000.
Estimated financial damage due to cyber threats
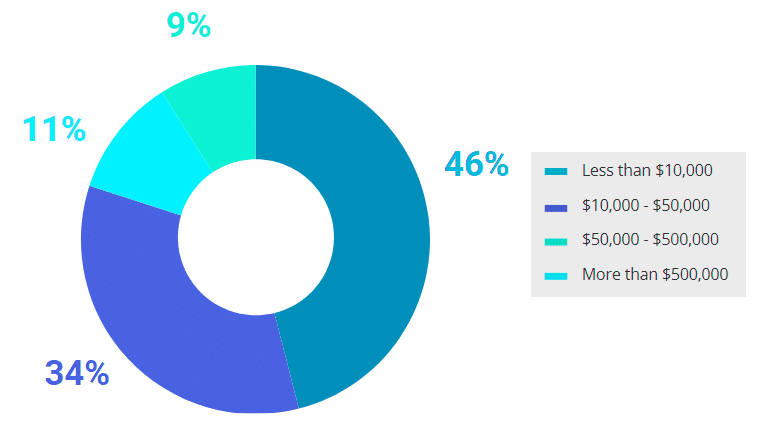
However, in large organizations (over 1,000 employ-ees), data breaches are more likely to have expensive consequences. While most of those respondents in this group (46%) still estimate the damage at less than $10,000, 34% said it cost them $50,000–$500,000. Among the overall pool of respondents, only 19% esti-mated the damage to be that high.
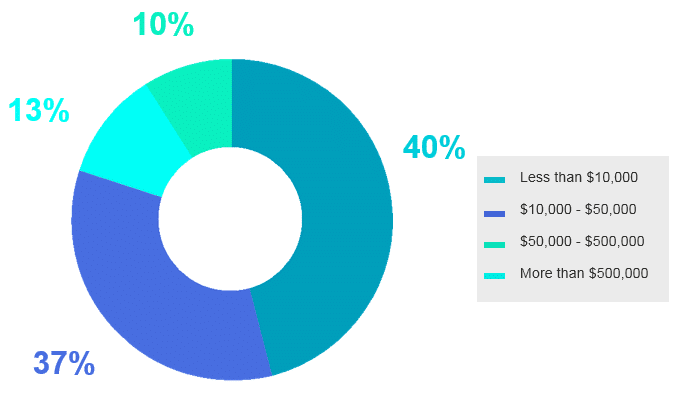
Similarly, the share estimating the damage at more than $500,000 is the biggest in very large enterpris-es (over 10,000 employees) — 13% versus 7% overall.
In short, the bigger an organization is, the more likely that the consequences of data breach will be expen-sive.
Large (1,000+ employees)
Very large (10,000+ employees)
Cloud security measures
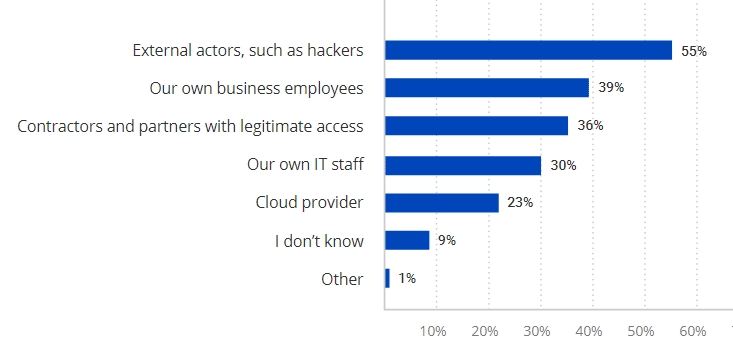
Before diving into the security measures organizations implement to keep their data safe, we asked about whom they are most concerned. More than half (55%) of respondents said that external actors are the main threat for their IT environment, followed by their own employees (39%) who might be creating security gaps inadvertently as well as contractors and partners requiring legitimate access (36%).
Who poses the biggest risk to data security in the cloud?
Then we asked what measures our respondents take to protect their data in the cloud and compared their answers with the data from our previous report.
In 2020, the most common cloud security controls or-ganizations reported were encryption (62%), auditing of user activity (58%) and employee training (58%). In 2022, the share of respondents using those measures is exactly the same.
In the current survey, multifactor authentication and cloud backup topped the list of protection measures. Both saw increases since 2020: MFA adoption grew from 57% to 69% and backups increased from 58% to 63%.
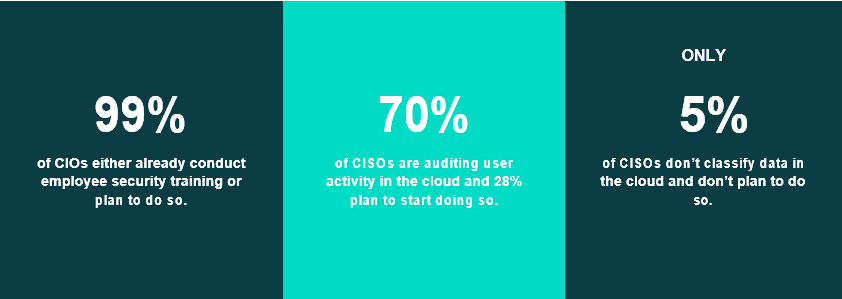
The least common security measure remains use of a cloud access security broker. Although CASBs are still not very popular, the share who plan to implement this option increased from 33% in 2020 to 46% now.
Meanwhile, the number who said they would not use this approach dropped from 40% to 30%. One reason for the lack of interest in this control is that it has the vaguest ROI of all the choices on the list.
Use of MFA is increasing because compromising user passwords remains a simple and effective attack tactic. Adversaries often have success using lists of the most common passwords, and they can also leverage databases of leaked passwords from other websites because people often reuse the same password across sites.
Plus, with more employees working remotely, bad actors can more easily log into corporate systems without raising suspicion. MFA is the cheapest and most effective way to reduce the risk of account compromise. The increased implementation of regular cloud backups can be linked to the rising number of ransomware attacks.
95% of large enterprises are auditing user activity in the cloud or plan to do so. Cloud backup is the most commonly used protection measure among large organizations; only 5% of them do not already use or plan to use this option.
It should be kept in mind though that while data may be easily restored from backups, bad actors can still blackmail organisations and individuals alike by threatening to publish the data.
Unclouding
The most resolute way of securing data in the cloud is to remove it from the cloud. In 2019, 48% of respon-dents had moved or were planning to move sensitive data back on premises. In 2020, despite the surge in cloud adoption due to the need to support remote work, this figure increased to 62%. This year, it grew to 66%.
Paradoxically, 78% of respondents are satisfied with their organization’s cloud security— but 66% have already moved sensitive data back on premises or plan to do so. Plus, 20% of organizations simply don’t store any sensitive information in the cloud.
This indicates that organizations believe their data is safer when it’s on premises. One reason is that cloud solutions are newer and therefore less mature, and many security concerns are out of cloud provider’s scope of responsibilities, which makes cloud expertise within the internal IT team crucial.
Of course, on-premises servers are not invulnerable, so organizations need to find the right balance between security and the business need for having data available in the cloud.
Impact of security
Data classification enables organizations to tag sensitive files so they can improve their control over where data is stored and who can access it. This technology significantly improved the speed of discovery for all types of incidents: The majority of respondents who classify their data were able to detect an attack within minutes, while those who don’t classify data usually needed hours or even days.
Impact of data classification on speed of incident detection
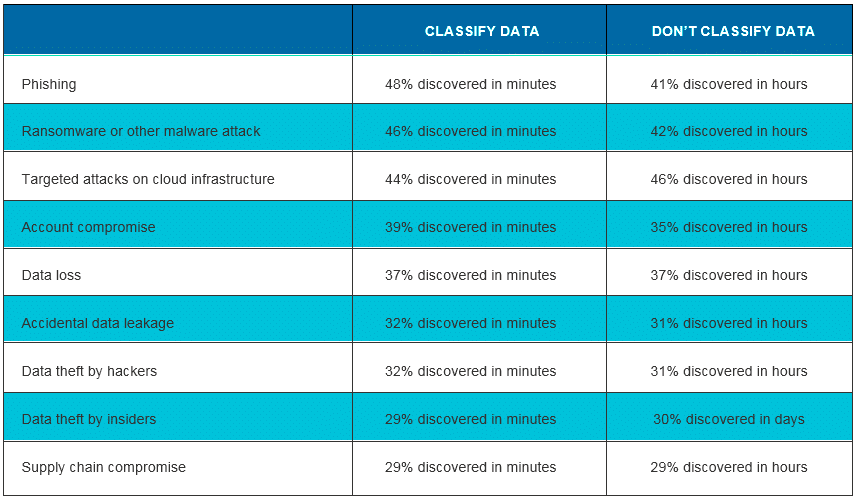
Auditing of user activity turned out to be a great way to improve the speed of incident detection. It was particularly effective for phishing, ransomware attacks and account compromise, where it reduced detection time from hours to minutes.
Cloud security challenges
The top 3 data security challenges named by survey respondents stayed the same from 2020: lack of IT staff, lack of expertise in cloud environments and lack of budget.
Most organizations accepted the new reality of remote work and adjusted their business processes to pandemic conditions. As a result, 33% of respondents now name IT staffing issues and lack of cloud expertise as the biggest cloud security challenges.
While lack of budget is still in the top 3, the share of those who struggle with this problem dropped from 47% in 2020 to 34% in 2022 — budgets are increasing, and IT teams are learning how to allocate the money effectively. Employee negligence is challenging for 22% of respondents, down from 38% in 2020.
Cybersecurity awareness is rising thanks to increased training and constant reminders about not opening suspicious links in emails allegedly from company’s CEO.
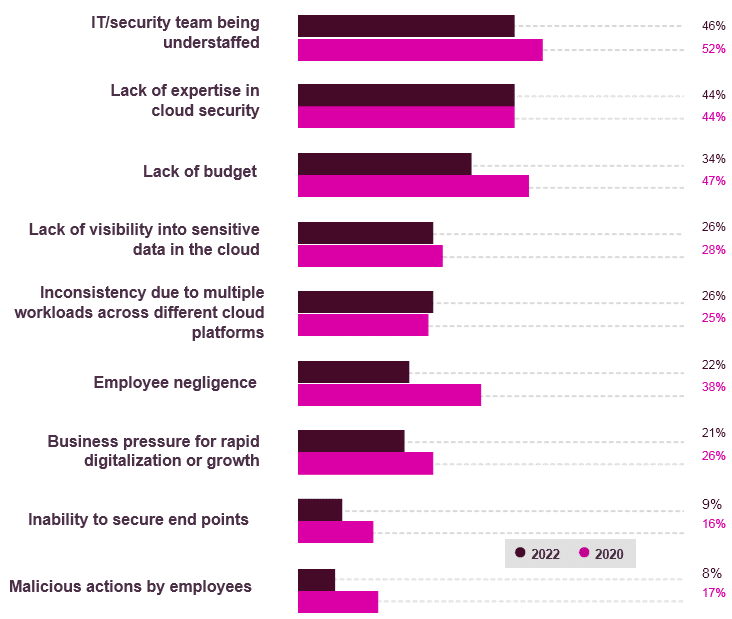
In 2020, 48% of CISOs noted that the business’s desire for growth hinders efforts to ensure data security in the cloud. Now, this problem was named by only 20% of CIOs and 23% of CISOs.
Budgeting
IT teams have also had to adjust their budgets to meet the needs of their remote or hybrid workforce. In 2020, organizations allocated 27% of their total cybersecurity budget to cloud security. In 2022, this share rose to 32% overall, and to 36% among large companies (1,000+ employees).
With 54% of workloads expected to be in the cloud by 2023, security budgets are growing. 49% of our respondents say their budget for cloud security increased in 2022.
………………….
AUTHOR: Dirk Schrader – VP of Security Research at Netwrix








