The pricing of cybersecurity insurance is similar to pricing property and casualty (P&C) or liability insurance. For example, the pricing of home insurance is based on the house having fire detectors, re-enforced concrete in earthquake areas, location in flood or tornado zones, and so on.
Similarly, cybersecurity insurance is based on the network having intrusion detection and prevention tools, patching of software, secure data centers and more.
Insurance, in these cases, is based on an event not happening. The risk is divided over many houses to cover the one house that is hit by a tornado or flood.
Insurance companies, and their actuaries, do not plan for every house to be hit by a tornado or flood. This model may not work for cybersecurity. As John Chambers, CISCO’s CEO, stated, “There are two types of companies in the world, those that have been hacked and those that don’t know they have been hacked.”

The question changes from whether or not a company is hacked to how likely a company is going to be hacked in a certain time frame. To calculate this probability, the factors of a likely cybersecurity incident need to be considered in a similar way that behavior, such as smoker/nonsmoker, and other factors are considered in calculating likely mortality over a period of time.
Being hacked will be added to the list of death and taxes as outcomes that cannot be avoided. With that in mind, cybersecurity could be modeled after life insurance products.
The factors that lead to a cybersecurity incident are outlined by Lockheed Martin and are called the Intrusion Kill Chain or Cyber Kill Chain (CKC). The CKC defines seven stages of a cyberattack, where each stage requires a successful breach of the previous stage (see Cybersecurity Insurance Market Size).
The seven stages are reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objective. Because of the dependency of a stage in the CKC on failure of the previous stage, a cybersecurity incident can be modeled stochastically with a Markov analysis.
This paper discusses the application of a Markov analysis to the CKC as a method to quantify the probability of failure to a cybersecurity system over a period of time or a number of attacks.
What is cyber security failure?
A security breach is any incident that results in unauthorized access to computer data, applications, networks or devices. It results in information being accessed without authorization. Typically, it occurs when an intruder is able to bypass security mechanisms.
Technically, there’s a distinction between a security breach and a data breach. A security breach is effectively a break-in, whereas a data breach is defined as the cybercriminal getting away with information.
Imagine a burglar; the security breach is when he climbs through the window, and the data breach is when he grabs your pocketbook or laptop and takes it away.

Confidential information has immense value. It’s often sold on the dark web; for example, names and credit card numbers can be bought, and then used for the purposes of identity theft or fraud. It’s not surprising that security breaches can cost companies huge amounts of money. On average, the bill is nearly $4m for major corporations.
It’s also important to distinguish the security breach definition from the definition of a security incident. An incident might involve a malware infection, DDOS attack or an employee leaving a laptop in a taxi, but if they don’t result in access to the network or loss of data, they would not count as a security breach.
Types of security breaches
There are a number of types of security breaches depending on how access has been gained to the system:
- An exploit attacks a system vulnerability, such as an out of date operating system. Legacy systems which haven’t been updated, for instance, in businesses where outdated and versions of Microsoft Windows that are no longer supported are being used, are particularly vulnerable to exploits.
- Weak passwords can be cracked or guessed. Even now, some people are still using the password ‘password’, and ‘pa$$word’ is not much more secure.
- Malware attacks, such as phishing emails can be used to gain entry. It only takes one employee to click on a link in a phishing email to allow malicious software to start spreading throughout the network.
- Drive-by downloads use viruses or malware delivered through a compromised or spoofed website.
- Social engineering can also be used to gain access. For instance, an intruder phones an employee claiming to be from the company’s IT helpdesk and asks for the password in order to ‘fix’ the computer.
In the security breach examples we mentioned above, a number of different techniques were used to gain access to networks — Yahoo suffered a phishing attack, while Facebook was hacked by an exploit.
The Biggest Cyberattacks in History

Whether they’re financially or politically motivated, cyberattacks can have enormously far-reaching effects. In the 21st century, cybersecurity has become an increasingly vital geopolitical consideration. When breached, the results can be catastrophic.
In 2017, for example, the Russian cyber military unit Sandworm orchestrated a malware attack that cost global businesses an estimated $1 billion.
A few years later, on the other hand, in 2021, hackers breached the system of a water treatment facility in Florida, nearly poisoning a regional water supply by programming a dangerous increase in sodium hydroxide.
The 9 most impactful cyberattacks in history:
- Cyberattacks on Estonia (2007)
- SolarWinds cyberattack (2020)
- Ukraine power grid attack (2015)
- NotPetya malware attack (2017)
- WannaCry ransomware attack (2017)
- Florida water system attack (2021)
- Colonial Pipeline Company ransomware attack (2021)
- Kaseya supply chain ransomware attack (2021)
- RockYou2021 (2021)
Cybercrimes often have a tremendous impact on companies and individuals. It is expected that the cost of cybercrimes may reach $10.5 trillion by 2025.
Cyber attacks are on the rise. Whilst modern technology presents many conveniences and benefits, there are people who misuse it which can pose a threat to our privacy.
Cyber Kill Chain
Lockheed Martin’s CKC outlines the set of steps, or stages, an attacker takes to breach and exploit a computer network. Each stage in the process builds on or takes advantage of the success of the previous stage. Any break in the chain will stop the attacker.
The CKC is based on methodology developed by the Department of Defense to outline the structure of an attack.
Lockheed Martin’s Cyber Kill Chain
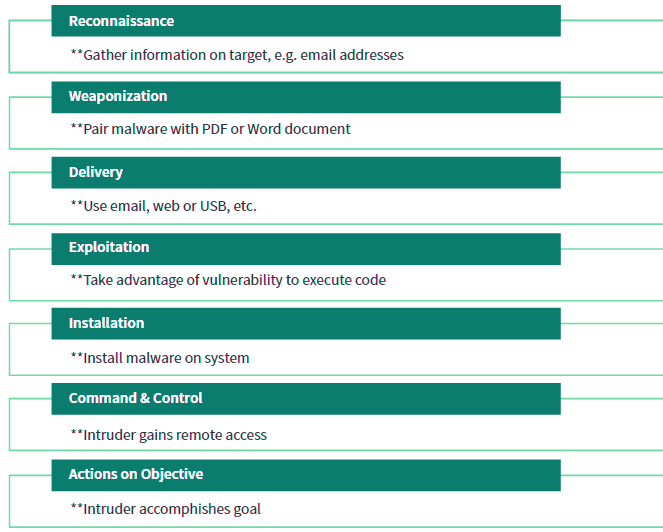
There are information security tools or processes to detect and/or prevent an intruder at each stage. The probability of success of the attacker or inversely the probability of failure by the security tools can be estimated (see Ransomware Attacks & Cyber Insurance).
While two of the stages, reconnaissance and weaponization, occur outside the targeted computer network, a likelihood of success/failure can be estimated.
For example, intrusion detection systems can watch for port scans during the reconnaissance stage or use web analytics to determine if a possible attacker is gathering information. Process controls, like removing Adobe Flash or removing local administrative rights, can also factor into the probability calculations for weaponization.
Markov Analysis
Markov analysis is used for many types of reliability calculations where a sequence of dependent events can cause system failures. This analysis is typically used to calculate meantime between failure for aviation components, computer networks and other systems (see Cyber Insurance and Cyber Risk).
One type of Markov analysis is called a Markov chain. It is a stochastic method of determining likely the state of a process based on the probability of events where each event is only dependent on the event immediately preceding it.
For example, in the CKC, the exploitation stage occurs only if the delivery stage was successful.
The interdependence of states can be represented using a state transition diagram. The states are noted by A and B. Probability of moving from state A to state B is l and the probability of moving back to state A from state B is m. The probability of remaining in a particular state is represented by 1 minus the probability of moving out of the current state. For state A, the probability of remaining in state A is 1- 1‐l.
Simple Markov Chain StateTransition Diagram
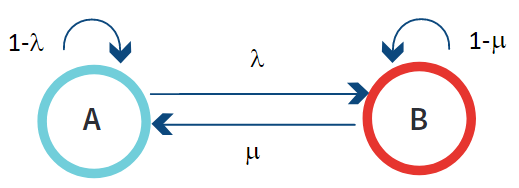
Applying the Markov Chain to the Cyber Kill Chain
The Markov chain can be applied to the CKC to quantify the probability of failure to a cybersecurity system. For this paper, a simple example with static probabilities for the individual components will be used (see Global Cyber Insurance Claims).
Information security defenses are built around preventive, detective and corrective controls.
The probability of remaining in CKC stage will be tied to the preventive controls. The detective and corrective controls will be combined to determine the probability of returning to a previous stage. For example, a corrective control would be the patching of a vulnerable operating system. To also simplify this example, only two stages will be examined.
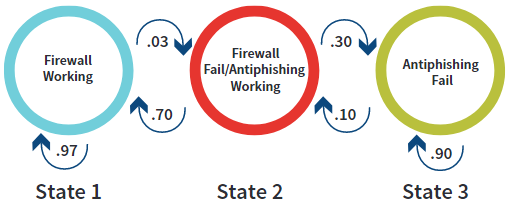
The CKC Markov chain will be defined from state 1 to state 3 using the following stages: delivery and exploitation.
- In state 1, delivery prevention is working (i.e., the firewall is blocking spam emails at a 97 percent rate).
- In state 2, the delivery prevention has failed and exploitation prevention is working (i.e., users are trained not to open .exe attachments at a 70 percent rate and report the email).
- In state 3, exploitation prevention has failed. For this example, there will be a small probability that the exploitation is detected by other tools (10 percent) and the chain returns to state 2.
Cyber Kill Chain Transition Diagram
Conclusions
The CKC model allows the various tools and processes used in cybersecurity to be grouped in a logical sequence. With this logical sequence established, stochastic reliability analysis can be used to determine the probability of failure.
In this example, a very simplistic model with static probabilities was used. More robust and complex probabilities, such as Weibull, would be used when the reliabilities of the individual security tools are better understood.
Additionally, companies have increased their sharing of threat information. Better sharing between companies will greatly improve the understanding of the reliability rates of these cyber protection tools (see Embedding Cyber Risk in Risk Management).
As demonstrated, applying reliability methodology to cybersecurity systems can help quantify the likelihood of a cyber protection failure. Once the likelihood of failure is estimated, actuarial analysis used for insurance products such as term life could be applied to cyber systems.
The views expressed herein are those of the author and do not necessarily represent those of the Federal Reserve Bank of Boston or the Federal Reserve System.
……………………….
AUTHOR: Steven Dionisi – commissioned IT examiner at the Federal Reserve Bank in Boston








