Given that cyber risk is a major driver of operational risk and that businesses and individuals are looking to the insurance industry to provide coverage for the cyber risks they face, we asked authors to “share their thoughts and reflections on either how insurance companies should deal with cyber risk in an ERM context, or how insurance companies can respond to society’s call to action to expand cybersecurity insurance offerings.”
Cybersecurity is what keeps our clients awake at night. Recent high-profile breaches have made it a boardroom concern.
Whether reading industry headlines or meeting with clients, cybersecurity is a key risk discussed. Actuaries must collaborate with other insurance industry experts to develop innovative, sustainable solutions for key stakeholders.
Whether as an endorsement to an existing policy or standalone, companies will look to their existing general liability provider for coverage and will not look kindly on those that refuse (see Most Effective Insurance Solutions for Cyber Risk).

Part 1: Risk
Direct losses resulting from profit-motivated cybercrimes, such as ransoming data, are actually very low—approximately $2 billion to $3 billion per year— while direct and indirect costs of such crimes are very high. Defense costs for such crimes total approximately $19 billion per year, while indirect costs total an additional $40 billion per year.1 Costs of a breach can be in the billions.
High-Profile Data Breaches and Their Associated Costs
| Breach | Cause | Cost (Ground Up) | Cost (Insured) |
| Epsilon | Spear-phishing2 | Up to $4 billion3 | No coverage in place |
| Home Depot | Vendor cybersecurity failure | $ billions4 | $100 million |
| and Microsoft Windows | |||
| security failure | |||
| Wendy’s | Unknown | $ billions5 | Unknown |
| Veterans Administration | Computer/external hard | $500 million | No coverage in place |
| drive incidentally stolen | |||
| from employee’s house | |||
| during burglary | |||
| Target | Vendor cybersecurity failure | $252 million | $90 million |
| Hannaford Bros | Malware | $252 million; ID theft insur- | No coverage in place |
| ance and replacement card | |||
| costs held compensable | |||
| Sony PlayStation | Unknown | $171 million | Unknown; settlement when |
| appeal pending after bench | |||
| granted summary judgment | |||
| against Sony | |||
| TJ Maxx | Poorly secured wireless LAN | $256 million | $19 million |
| in two stores | |||
| Sony Pictures | North Korea | $151 million + reputation | $151 million |
| Entertainment | |||
| Heartland Payment | SQL injection attack | $140 million | $30 million |
| Systems | |||
| Anthem | Bogus domain name/phishing | Over $100 million | $100 million |
Many different costs are involved. Direct costs include the cost of ransomware, loss of data and lawsuits. Uninsured risk can lead to key people losing their jobs, and perhaps future cases will include boards being sued for negligence.
IT vulnerabilities that have led to this state of affairs have shown almost no signs of improvement over time. Many organizations are “living below the security poverty line.”
Cybersecurity budgets for many midsize and small companies are minimal. As a result, those companies often have little or no IT expertise, are unable to follow through on IT consultant recommendations and accordingly focus only on “putting out fires” rather than managing long-term cyber risk issues (see Global Cyber Insurance Claims Report).
Currently, there’s a general lack of objective proof that particular controls— policies, processes, technologies and otherwise—have measurable and positive risk management impacts. Singapore is among the most technologically advanced countries in the world, yet its government’s cybersecurity solution is eliminating employees’ internet access.
Limited technology solutions exist for addressing cyber risks. Most vendor options fall short of needed protection, and they don’t seem to be improving.
Technical controls are often too complicated and/ or costly for businesses to implement. The lack of available information about which cyber risks are most likely to materialize compounds these problems. Without more security intelligence, most organizations cannot make informed decisions about where to best spend their limited cybersecurity budgets.
Google Trends
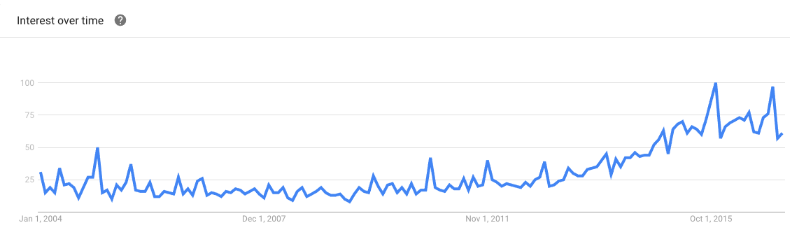
Given this landscape, some companies may be inclined to buy cybersecurity insurance rather than spend money on technology solutions and other cybersecurity controls. They may opt to transfer risk entirely rather than invest in expensive and largely unproven cyber risk mitigation efforts (see Cybersecurity Insurance Market Size Forcast).
Without minimum underwriting requirements by carriers, this phenomenon could give rise to a moral hazard situation that encourages companies to take further risks rather than improve their cyber risk cultures.
There are companies offering cybersecurity endorsements for their general liability insureds without a full understanding of expected cost or coverage, instead relying on low policy limits.
Would insureds not expect guidance on appropriate limits? When a loss occurs and the limits leave the insured with a large residual loss, will they keep any business with this company? Low loss limits are no substitute for actuarial diligence. Indeed, I argue below for generous limits.
Part 2: Adding Value
There are two reasons insurers are offering coverage for cyber risk. First, general liability is a large, profitable business for many insurers. Insureds will test the markets if their current carrier cannot provide necessary coverages.
Many of the risks that arise in cyberspace are not new (e.g., intellectual property theft, lost profits, privacy and reputational damages), and other professions are looking to actuaries to take the lead.
Regarding a cyber incident data repository, a broker, two underwriters and a reinsurer suggested that actuaries are uniquely qualified to process this data to develop new, and enhance existing, cybersecurity insurance products (see Underwriting Strategies & Available Cybercapacity).
It is precisely this absence of data where actuaries can demonstrate their value. We can itemize data items that should be collected for a meaningful analysis, comb through available data for frequency and severity benchmarks, determine what data are credible and appropriately weight differing indications.
Furthermore, technologists are at a loss as to what protections work best. For example, how beneficial is encryption? What level should be adopted? Actuaries are uniquely skilled in finding answers to such questions in the data.
By synthesizing available data, actuaries can guide insurers’ efforts to work with insureds to reduce losses and increase profitability.
Cybersecurity policies generally consist of multiple subcoverages (e.g., Beazley’s Breach Response has eight). Actuaries can determine the relative exposure from each of these subcoverages and tailor the policy specifications to the insured’s concern.
One major issue in cyber insurance is what level of cybersecurity carriers should demand from the insured. If these levels are made too onerous, the marketability of the product will suffer.
However, standards that are too lax will encourage insureds to skimp on expensive cyber protection solutions. Some have expressed the opinion that demanding the latest software patch updates from all employees is unreasonably onerous. In my opinion, it is not.
Top Discovered CVE-2014 Examples
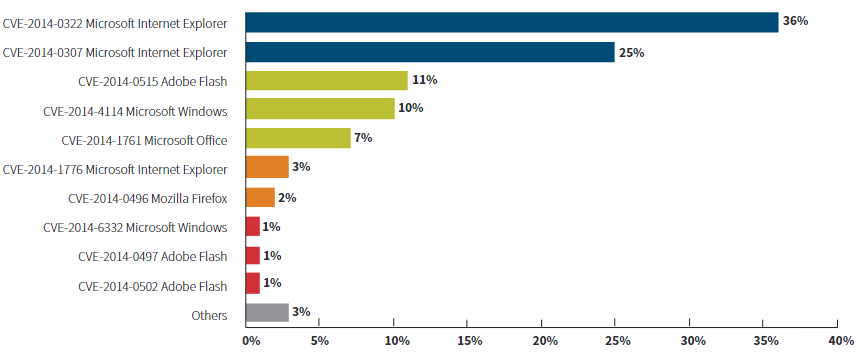
The insured is in a position to ensure all employees are on a given patch at a given point in time through centralized updates. Insureds are also in a position to require administrator rights for all downloads, encryption for external drives, natural language processing and so on.
Many companies demand their employees take sexual harassment awareness training annually, to avoid lawsuits and the loss of key personnel. Insurers are justified in mandating annual cybersecurity training.
There are many causes of loss, and a data breach may be caused by several. While not all of these causes can be controlled by insureds, Verizon’s 2013 Data Breach Investigations Report found that 90 percent ofcyberattacks over the previous year were preventable with simple or intermediate systems in place (see Cyber Insurer Perspectives on Ransomware).
There’s clearly room for improvement in most organizations when it comes to cyber risk management. Insurance should not cover those breaches in the insured’s control; it exists to cover those things outside the insured’s control. Carriers should motivate insureds to do what they can, through both compulsory precautions and policy terms, as discussed herein.
Frequency and severity of events are the “holy grail” of cybersecurity risk management. While companies can analyze the frequency of cyber incidents based on some available data, estimating severity is more difficult.
Different industries are held to different standards. For example, the medical industry has higher cyber claims frequency because of the rigorous information security and privacy standards of the Health Insurance Portability and Accountability Act (HIPAA).
Insurers assess insureds on geography and sector. Judgment is used to identify which companies are most likely to be attacked.
Frequency is short tailed and companies generally find out quickly if they have been breached. This has two implications: First, it makes it easier to price, and therefore a more insurable risk. Second, it is rare more than one policy will be triggered with one event, and those rare events, generally related to cloud providers, can be specifically excluded from contracts. Some have suggested a federal backstop, like the Terrorism Risk Insurance Act, would be required to cover such events.
Insurers should not cover frequency risk. This burden should be placed on the insured. Insurance companies add value to companies by assuming volatile risk so management can concentrate capital in other areas.
The company itself is best placed to manage predictable losses through cash-flow management, perhaps through a single-parent captive. High per-occurrence deductibles keep frequency risk with the insured and transfer only the volatile severity risk to the carrier.
Following this logic, high aggregate deductibles would not be required. I suggest a per-occurrence limit across the policy.
High per-occurrence deductibles prevent insurance from being seen as a replacement for proper cybersecurity. As mentioned above, some argue cyber insurance is currently cheaper than cybersecurity, and therefore moral and morale risk is the biggest impediment to insurance companies wishing to expand in this area. To be sustainable in the long term, insurers must make their policies unattractive to companies that choose insurance as a replacement for investing in cyber risk management.

The carrier will normally be more able to assume the risk of high-severity losses than the insured. Carriers can spread the risk among many policies, so they are more able to absorb low-frequency events.
To maximize value, carriers should therefore offer high policy limits. Low policy limits are used to keep premiums down when the insured is willing to risk high-severity losses, implicitly choosing to use their resources and capital to protect against other risks.
Inadequate limits can lead to bankruptcy in the most severe cases. My experience is that insureds are not willing to accept the risk of high-severity losses from cybersecurity where the risks are not fully known. Carriers are in a much better place to accept this risk through the normal insurance risk-pooling mechanisms.
Another reason for policy limits is to keep the insured’s skin in the game. As outlined above, severity risk is significantly higher than frequency risk, so per-occurrence deductibles will be much more effective. Insureds are more able to retain the risk from high deductibles than low limits.
Part 3: Cyber Risk is Opportunity
I conclude that insurance companies can expand cybersecurity insurance offerings as follows. Policies must contain austere per-occurrence deductibles and rigorous demands on insureds’ cybersecurity protection.
This will keep premiums affordable while encouraging insureds to mitigate their risks.
- Limits should be generous on both per-occurrence and aggregate bases, since carriers are more able to assume the risk of high-severity losses than insureds, and there is limited opportunity for insureds to minimize these low-frequency events.
- Coverages should be flexible to address insureds’ particular concerns.
While cyber risk is associated with some stunning losses, a lack of data and lack of consensus in the technology world as to how to treat it, this is precisely why actuaries’ specific skill set and experience can add value. As I write, the largest insurance companies are expanding their cyber liability teams, recognizing this coverage’s tremendous potential. Those who can solve the puzzles of cyber coverage and address their clients’ problems will be rewarded.
…………………….
AUTHOR: Michael Solomon, FCAS, CERA, MAAA – Principal at The Actuarial Practice of Oliver Wyman, consulting actuary at The Actuarial Advantage








