Technology is the most significant driving force of change in today’s digital economy. Especially since the pandemic began, businesses have adapted to the changing nature of work and an economy powered by digital technology.
Today, employees work from digital home offices, intelligent software is available to assist with everything from exercise to shipping, and business can thrive with nothing but a digital presence. The transformation of our world has allowed organizations and employees to weather the COVID-19 pandemic, but it has also accelerated a new type of risk: digital risks.
By the end of 2022, nearly 65% of the global GDP will be digitized — reliant on a digital system of some kind.
This shift to digital has made it possible to create, run and scale businesses faster and easier than ever before, but the shift to digital technology has also created a new class of digital risks that are constantly evolving and strike faster and often with more severity than traditional risks. The events of the past two years have made this shift clear: from ransomware attacks to the challenges of managing distributed workforces during the pandemic, digital risk is different (see Cybersecurity Insurance Market Size).
While traditional insurance has served mainly as a hedge against loss only after an incident, insurance designed for the digital economy needs to be active — providing value before, during, and after an incident that could lead to a loss.
The following report provides a detailed look into the incidents that led to claims from our policyholders over the second half of 2021. In addition to the data, we share a thoughtful analysis of the current trends and predictions for 2022.

Analysis of claims data reveals a number of evolving trends:
- Ransom demands continue to increase, though claims severity has started to plateau.The ransomware business model has begun to mature, though attackers are showing no signs of slowing down. The average ransomware demand made against our policyholders increased 20% in the latter half of 2021 and the claims severity increased 10%.
- The frequency of other attack techniques also rose as hackers expanded to new tactics. This heralds an era of omnidirectional threat-equality — cyber threats are ever-present from all angles. While ransomware may be the most newsworthy, no attack vector can be trivialized or ignored.
- Small businesses are disproportionately impacted. As attacks become increasingly automated, it has become easier and more profitable for criminals to target small organizations. Overall claims severity rose 56% for small organizations under $25M in revenue. A dramatic increase in claims frequency, with a 40% increase in ransomware attacks and 54% increase in funds transfer fraud attacks.
- Active Insurance works. We’ve processed more claims across more organizations in the past year than in any other period, and there wasn’t a single organization that we weren’t able to help successfully recover. Through our active protection and response capabilities, we were able to solve 46% of reported incidents at no cost to the policyholder.
Key Findings
The impacts of the past two years — from the rapid transition to remote work and new technologies to evolving digital threats — continue to transform all facets of life and business. The COVID-19 pandemic continued to disrupt daily routines, companies large and small continued to support hybrid work models, and cybersecurity incidents shook many industries (see Cyber Insurance Market Strategy).
The scale and frequency of cyber incidents led 2022 to be the year that cybersecurity issues entered the mainstream discussion, with President Biden convening a session on the importance of protecting America’s business interests in the face of a growing wave of cyber attacks.
Overall claims frequency
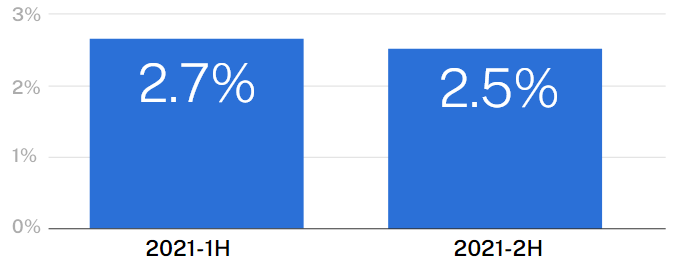
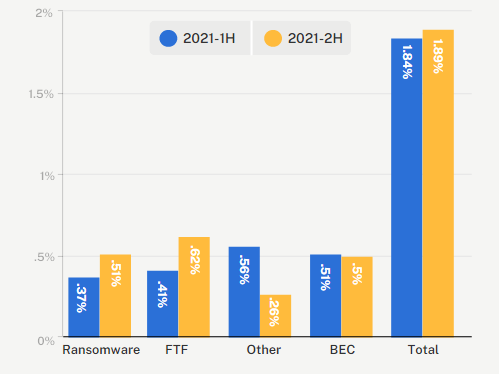
Insurance claims frequency by event type
It seemed as though the onslaught would never end — starting with highprofile cyber events such as Colonial Pipeline, Kaseya, and then Log4j in the latter half of the year. As a result, we saw a substantial increase in claims during the first half of 2021, with frequency rising 31% from the second half of 2020.
Claims frequency stabilized over the course of 2021, with frequency decreasing 7% from H1 2021 to H2 2021.
The surge in cyber crime also impacted claims severity, which we define as the average cost of a cyber claim. Overall claims severity increased 28% to an average loss of $197,000 across all of our policyholders. Claims severity in Canada increased over 4x from 2020 to the first half of 2021, only to decrease 20% during the second half of the year.
Percentage of reported claims by event type
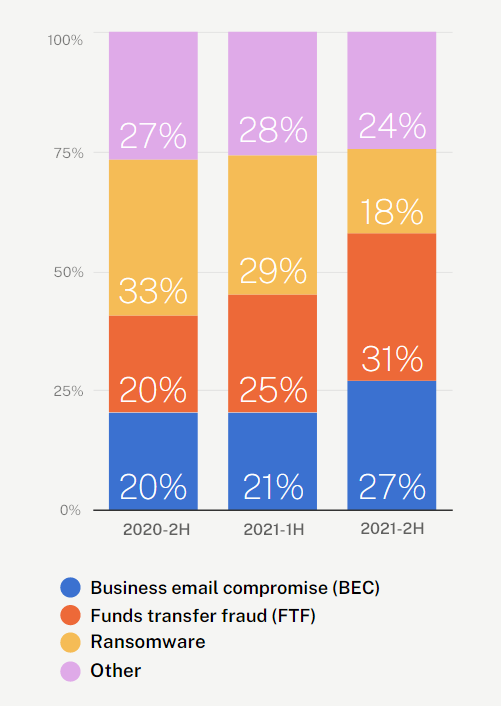
According to Ransomware Attacks & Cyber Insurance Report, small and midsize businesses seemed to be off the radar of cyber criminals, but that has unquestionably changed in the past few years.
While cyber incidents can be equally devastating to businesses of any size, we’ve seen a material uptick in claims targeting small and midsize businesses.
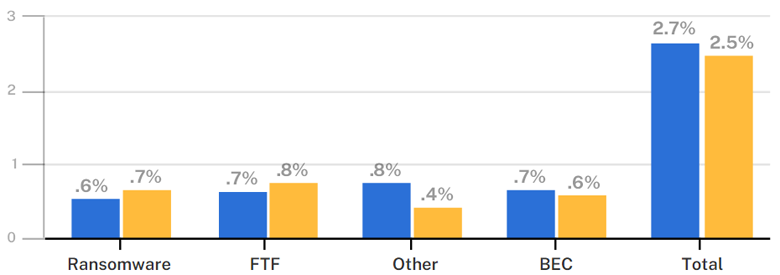
Claims severity by event type
Claims frequency for small businesses (<$25M revenue)
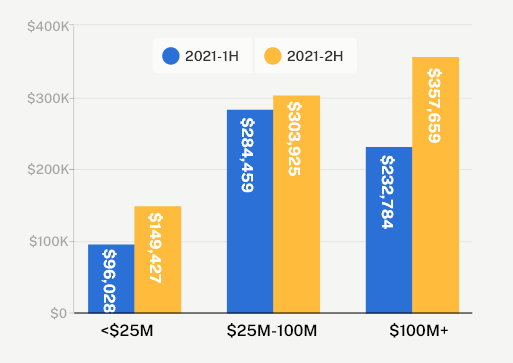
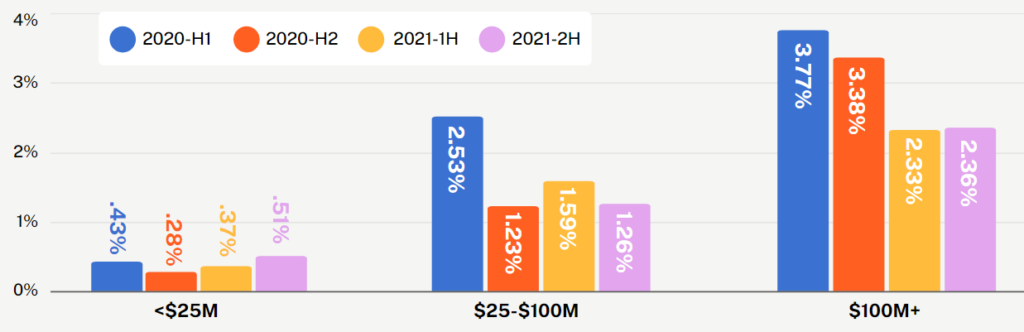
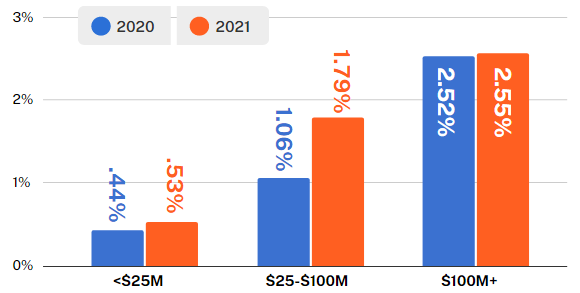
Small businesses with under $25M in revenue were particularly vulnerable in 2021. We saw a 56% increase in the average claim cost, increasing to $149,000 by the end of 2021. We also observed dramatic increases in the frequency of attacks; small businesses also saw a 40% increase in ransomware attacks and a 54% increase in funds transfer fraud incidents. Small businesses are especially vulnerable to threat actors as they often lack the resources to respond quickly.
Middle market businesses with $100M in revenue or more also saw a material increase. Claims severity increased 54% to a whopping $358,000 from H1 to H2 2021. While claims frequency fluctuated for this segment, it remained consistently 2-3x higher than the claims frequency for small businesses.
Cyber criminals are opportunistic, particularly when it comes to small and midsize organizations, and the technology and processes that organizations use are far more key to their risk than what their industry is.
Claims severity by revenue band – US
Claims frequency by event type
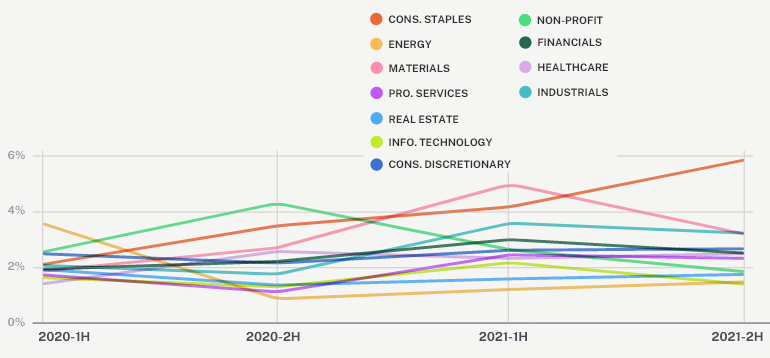
No company is too small to be an enticing financial opportunity for attackers. Still, some industries did experience notable increases in claims in the past year. From H1 2021 through H2 2021, we saw a 40% increase in claims severity for consumer staples businesses and 23% increase for energy businesses.
Ransomware: The cyber epidemic that’s made hacking into a lucrative business
Ransomware has reshaped the way we view cyber risk. Over the last two years, ransomware attacks have made headlines frequently, impacting everything from critical infrastructure to healthcare and small businesses. It has become clear that all organizations are vulnerable to this persistent digital risk.
Throughout 2021, ransomware demands and frequency continued to increase, while claims severity has started to plateau.
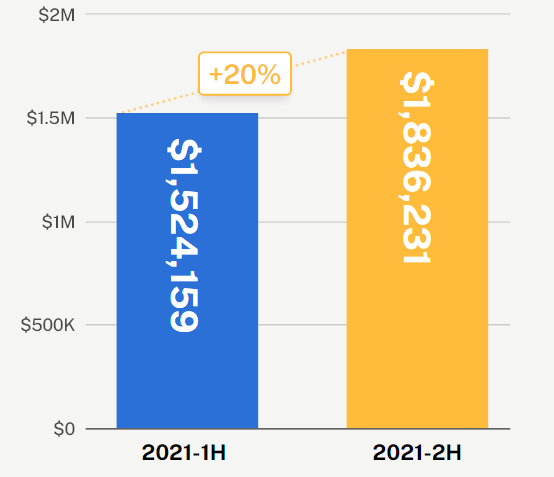
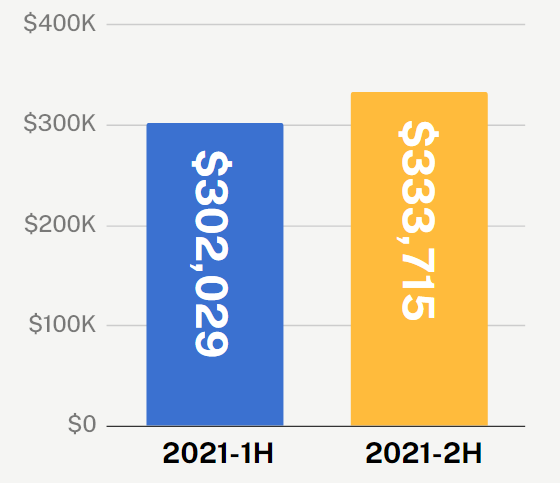
Coalition policyholders experienced a 20% increase in ransomware demands to an average of $1.8 million — a cost that remains untenable to pay for many organizations. We also observed a 23% percent increase in ransomware claims frequency in the second half of 2021, to 0.67% of all policyholders.
Ransomware claims severity also continued to increase, albeit moderately, rising 10% from the first half of 2021. We anticipate that the severity of ransomware will continue to flatten over time. As we predicted in our previous Claims Report, there is little leverage threat actors can gain beyond what they already have once they have taken an organization’s operations and data hostage.
Average ransom demand made against policyholders
Payments, highlighting potential sanctions risks associated with making ransom/extortion payments in response to a ransomware event.
Ransomware claims severity
Not all industries have been impacted equally by the ransomware epidemic, and healthcare organizations suffered an epidemic of ransomware attacks. Threat actors capitalized on the frantic nature of the continued COVID-19 pandemic to attack a vulnerable industry that was focused on providing critical patient care. Over the first half of 2021, the claims frequency for healthcare increased 67% and increased another 20% in the second half of the year.
Ransomware frequency by revenue band
Top ransomware variants
Top ransomware variants by number reported and instead are likely to align themselves with whatever variant is accessible and inflict the most damage.
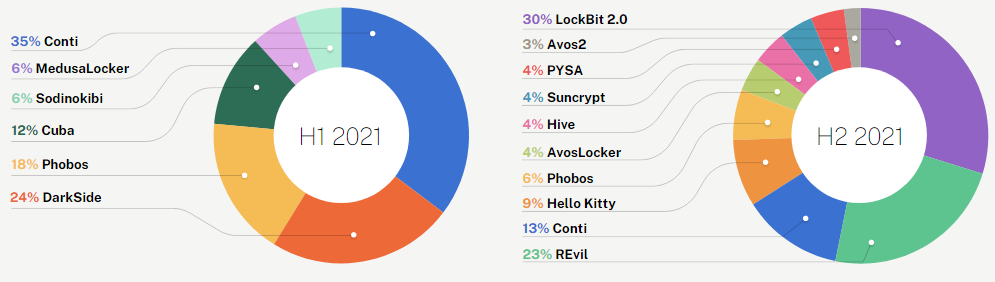
In the first half of 2021, we observed an explosion of new and invasive ransomware variants. Surprisingly, the second half of the year saw a near-complete shift: only Conti ransomware was consistently seen among our top ransomware variants. Seeing a wide shift in ransomware variants across the same year points to the opportunistic nature of cyber criminals — just as they target organizations irrespective of size and industry, they will utilize whatever ransomware variants are accessible, easy-to-use, and successful.
Top ransomware variants by number reported
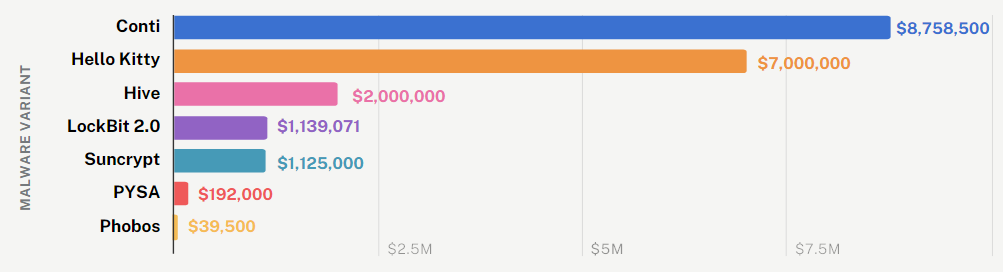
Average ransom demand in H2 2021
Tips for ransomware recovery and prevention
Recovering from a ransomware attack can be a long process for any organization — even those that have good backups and cyber insurance. To prevent future incidents, organizations should utilize a combination of security tools and best practices.
- Maintain good backups
A good data backup can mean the difference between a full loss and a full recovery after a ransomware attack. Develop a regular schedule to backup critical and non-critical business data and test backups to ensure they are viable. We recommend maintaining copies of your data, with two different backup formats, and one backup stored offsite (AKA 3-2-1 rule) to store essential data completely separate from the primary network. Often, onsite backups use the same credentials as the rest of the network and there are ransomware variants that will delete or encrypt backups.
- Keep servers updated/patched
Keeping servers up to date as soon as security patches are released can make the difference between a minor inconvenience, and a full blown ransomware incident. Threat actors scan for, and exploit servers which have not been updated following the release of major security vulnerabilities such as ProxyLogon, and Log4j. A company that keeps all servers updated is much less likely to experience ransomware, as an unpatched server can become patient zero.
- Implement strong passwords and multi-factor authentication (MFA)
We recommend organizations adopt strong password guidelines. Additionally, a combination of multifactor authentication (MFA) and strong passwords can help mitigate a threat actor’s success rate at stealing user credentials.
- Disable Remote Desktop Protocol (RDP) and implement zero trust protocols
Remote access points (especially Remote Desktop Protocol or RDP) are one of the most common methods for ransomware gangs to infiltrate your network. Many organizations turned to RDP to support remote or hybrid work models, but they also can serve as an easy entry point for threat actors if not properly configured and secured. To safely offer remote access, we recommend implementing a virtual private network (VPN).
Funds Transfer Fraud: The low-tech attack that disproportionately target small businesses

Cyber criminals are opportunistic, often opting to target businesses based on technology and processes rather than industry. One of the easier methods to monetize cyber crime is funds transfer fraud (FTF), which is often perpetuated through social engineering techniques like phishing or business email compromise (BEC).
Once a threat actor has access to your business mailbox, they can manipulate your contacts and modify payment instructions, sometimes without even triggering any security alerts.
Threat actors can also send you a change in payment instructions that purports to come from a customer or vendor via a lookalike email domain or by compromising the customer or vendor’s email system.
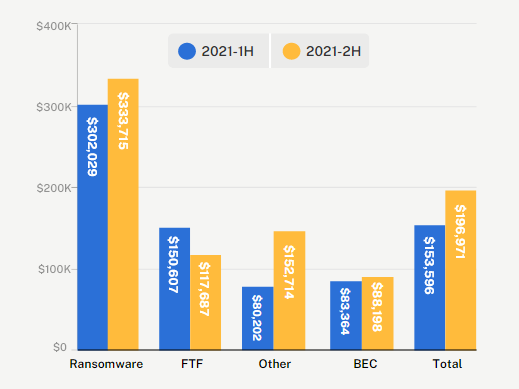
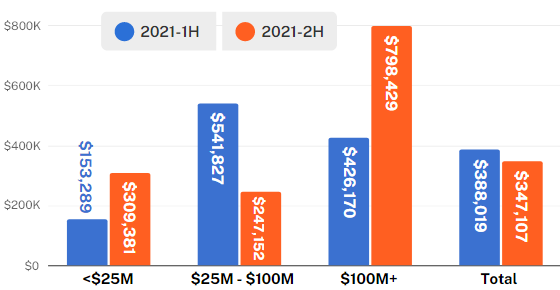
Funds transfer fraud skyrocketed in the first half of 2021. The initial FTF loss, defined as the loss before we were able to recover funds, surged to an average of $388,000 before accounting for recovered funds. Over the second half of the year, the average initial loss decreased by 11% to $347,000. While a small decline may initially appear optimistic, this is still a 78% increase in initial losses from 2020.
From 2020 to 2021, overall FTF losses increased by 69%. The frequency rose by 21% for organizations with under $25M in revenue and 68% for organizations with $25M-$100M in revenue.
Furthermore, we observed some organizations were disproportionately impacted. For small organizations with less than $25 million in revenue, the initial FTF loss increased by 102% in the second half of 2021. The frequency of these attacks also increased dramatically for small businesses under $25M in revenue, rising 54% from H1 2021.
Initial funds transfer loss before recoveries – by revenue band
Funds Transfer Fraud frequency byrevenue band
Organizations of this size are likely especially vulnerable to funds transfer fraud attacks. They often have a smaller digital footprint than larger organizations, leaving threat actors with fewer options to pivot inside a network and less infrastructure and data to hold hostage in a ransomware attack.
Recovering from funds transfer fraud — speed is essential
Funds transfer fraud losses can be devastating for any business, but there are steps your organization can take in the event of a fraudulent transfer. We recommend policyholders take immediate action to maximize their chances of recovery.
- Notify Coalition’s claims team of the loss as soon as possible, ideally within 72 hours of the transfer.
- Immediately notify your bank of the fraudulent transfer, and request a clawback of the funds.
- File a report with the FBI at IC3.gov.
- File a report with your local police department.
- Repeatedly inquire with your bank and the receiving bank on the status of the recovery.
Additionally, we recommend implementing multi-factor authentication (MFA) to reduce the risk of a BEC attack and a cybersecurity education program to enable employees to recognize and report potential email compromise attacks.
While ransomware spent much of 2021 in the limelight, FTF cases continue to rise like never before.
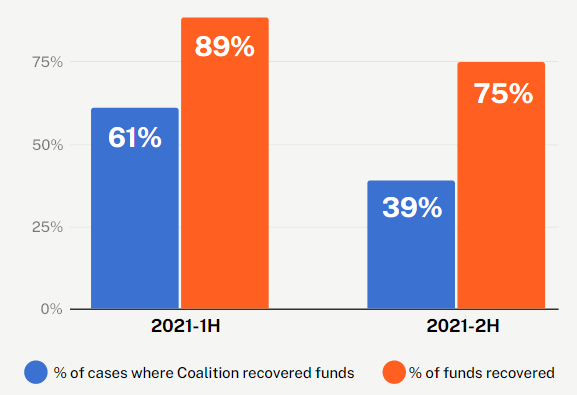
Time is of the essence with FTF cases, and we encourage our policyholders to reach out as soon as they notice an incorrect payment as we are more likely to recover funds within 48-72 hours of the transfer.
In the latter half of the year, many organizations were slower to report losses, which unfortunately makes it less likely that we can recover the funds.
Funds Transfer Fraud recovery
How to combat FTF?
The primary defense against funds transfer fraud is a defined process for how your organization processes new requests and change payment requests. The procedures should include calling the requesting party on a known good number to confirm the demand — never use the contact information provided in an email as these are often manipulated via phishing.
These verification procedures should also have a defined, two-party approval process for transfers and required reviews for payment change details.
Emerging attack techniques: Tactics and techniques threat actors used to execute cyber crime
Over the last two years, the COVID-19 pandemic fueled a fueled a fast transition to remote work to remote work, and organizations found themselves reliant on insecure technologies to facilitate this change. As a result, we previously observed that remote access tools such as remote desktop protocol (RDP) led to an explosion in ransomware and funds transfer fraud cases. Over time, these tactics have become the main ways that immediately monetize cyber crime.
Threat actors use a wide array of attack tactics and techniques to gain access to systems, and while some are less newsworthy, they are no less dangerous to organizations and the data they protect.
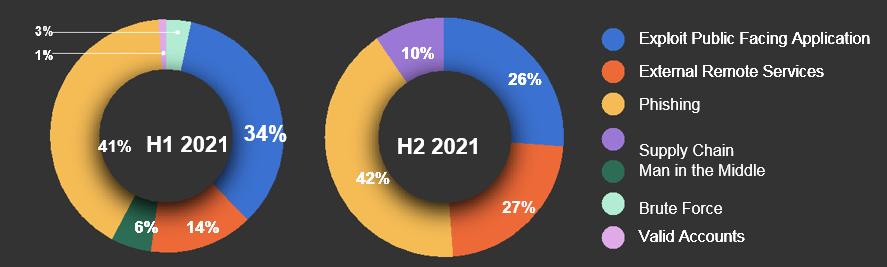
We examined the common attack techniques that were used against our policyholders, and found that while cyber criminals continue to expand their techniques, phishing and social engineering remains the most common tactic. Here is how criminals executed cyber crime in the past year.
Percentage of reported claims by attack technique
Phishing
A popular technique used to target victims, phishing attacks can also precipitate other types of cyber crime. Once an attacker is inside your email inbox, they have access to a treasure trove of sensitive business information they can use to phish others in your organization, redirect funds, or deploy ransomware. In H1 2021, email phishing was the initial vector of attack for 41% of reported claims where this data was available.
Stolen credentials from valid accounts
Attackers can also gain access to a system by exploiting a username and password, either by brute force, a type of trial and error hack, or credential stuffing where they utilize login data that has previously been exposed in data breaches.
Brute force
When all else fails, attackers can brute force their way into networks by guessing passwords by exhausting all possible combinations or using dictionaries of common passwords and their variations. This attack technique occasionally does work if employees are using extremely weak passwords or leaked passwords, though it can be easily defeated by multifactor authentication. This can be especially risky when the weak password is used on a risky remote access technology, such as RDP.
Exploiting public-facing applications
Adversaries are constantly scanning the internet for vulnerable, external-facing applications. These can be VPNs, firewall devices, web servers, and more. When a server becomes vulnerable, it can be exploited easily by an adversary if it is publicly-facing. After exploitation, adversaries will try to move laterally to deploy ransomware. Coalition’s Active Risk Platform scans for these external-facing applications and notifies policyholders a vulnerability is identified.
External remote applications
While remote access helps organizations stay connected through remote work, it can also create an open door for attackers to target. Employees using weak or reused passwords to connect to remote access technologies pose a risk to the security of their organizations. Attackers will abuse these accounts to connect to the network and attempt to exfiltrate data or deploy ransomware. It’s important to enforce MFA and VPN, keep remote access technologies updated, ensure they’re properly configured, and limit administrator logins.
Man-in-the-middle attacks
These attacks allow threat actors or adversaries to position themselves between your device and the connection to your organization’s network.
Once you attempt to connect, they can steal your credentials and gain network access. Internetfacing applications are accessible via the public internet and provide a service to the public or allow access to an internal network. Threat actors exploit these applications to gain access to a network and launch other attacks.
Aggregate digital risks: your vendor’s attack perimeter becomes your attack perimeter
Traditionally, the digital perimeter of a company, which protected business information, employee information, and customer information, was a straightforward castle and moat model. The physical office, or castle, was protected by a moat, or traditional firewall and VPN solutions.
The transition to a hybrid work culture upended that model. Organizations must now protect their critical business data from attacks against their own digital perimeter and that of their vendors and employees.
Most businesses partner with several third-party vendors — it is simply the cost of doing business in a fastpaced world. Examples of vendors include IT service providers, online software, cloud computing providers, or third-party services that are part of your network infrastructure.
In the first half of 2021, we observed several high-profile attacks against vendors: Mimecast, Kaseya, and Microsoft Exchange, to name a few. These attacks are sometimes referred to as supply chain attacks; however, that is an oversimplification. Often organizations directly partner with these vendors to provide IT functions such as email, firewalls, VPN access, and more. Cyber criminals attack vendors and, through successful compromises in the vendor’s digital perimeter, can victimize a large number of connected organizations at once, rather than just one. At the time, we correctly predicted that the increased reliance on vendors would mean organizations would continue to struggle to control such risks, and new attacks would continue to surface.
Predictions for Cyber Insurance
At Coalition we have unique insight into the cyber threat landscape and its impact on our policyholders. We expect the market will continue to evolve and our claims, incident response, and insurance teams share the following predictions for the upcoming year.
Cyber insurance will become harder for many businesses to access.
In 2021, the insurance market continued to harden and this is unlikely to slow down. In the first half of 2021, we predicted the insurance market would continue to harden throughout the year and it would become harder to qualify for cyber insurance. Over the second half of the year we observed more than one carrier pause underwriting cyber insurance policies entirely — after previously rolling out price increases, coinsurance, and sublimits on critical coverages. We predict the market will stay hard for some time, particularly in response to the insecurity surrounding potential government oversight and intervention. As the world’s focused Active Insurance company, Coalition has not pulled back coverage and is instead focused on preventing digital risks before they strike. Our Active Cyberand Active Executive Risk products help organizations assess, prevent, and cover digital risks.
Government scrutiny regarding ransomware payments and cybersecurity will continue.
Previously, we predicted more regulation and public frameworks from governmental entities regarding the disclosure of cybersecurity incidents. In 2021 we saw an uptick in ransomware events along with increased government scrutiny surrounding payments.
Continued impact of vulnerable and unpatched boundary devices.
The devices designed to protect or provide access to organizational networks (such as firewalls, VPNs, and remote access appliances) proved highly vulnerable in 2021. As return-to-office plans were delayed or scrubbed, and temporary setups became permanent, these assets drew attention from threat actors and the patch cycle for firmware at many organizations is far slower than operating system and software updates.
Supply chain attacks will continue to plague affected businesses in emerging ways.
……………………
AUTHOR: Catherine Lyle – Head of claims at Coalition








