Cyber risk has become one of the top risks on risk managers’ radar given its increasing incidence rate and impact. The emerging risk survey by the Joint Risk Management Section of the CAS, the CIA and the SOA named cybersecurity the top emerging risk chosen by 58% of survey responders. Cyber risk includes the risk of damage to the hardware, software and security of the information system caused by people, system failures and process failures. It could cause financial losses, business disruption and reputation damage.
The insurance industry has been adopting more new technologies that help information sharing with the clients and the public. Many companies are actively using social media to effectively communicate with clients and public audience (see Cyber Insurance and Cyber Risk Review).
Insurers are requiring more personal information from clients such as telematics data for driving behavior analysis and health/fitness data.
The embrace of the Internet of Things provides new opportunities but also leads to a higher exposure to more complicated cyber risk. Insurers may also offer cyber insurance that protects the insured from financial losses caused by cyber risk. These insurers are exposed to a wider range of cyber risk events. As a unique and quickly evolving type of risk, cyber risk needs to be embedded into the existing risk management framework to facilitate consistent capital management, risk assessment and resource allocation.
Appetite for Cyber Risk

According to Eling and Wirfs, cyber risk is less severe than noncyber operational risk in terms of loss amount and volatility. Cyber risk is more contagious than noncyber operational risk. A single cyber risk event may affect multiple firms.
Given the wider application of the internet of things, cyber risk’s frequency and severity may grow significantly.
For a specific insurer, insufficient investment in enhancing cyber security could also lead to much higher cyber risk exposure than the average level. Setting the risk appetite for cyber risk requires thorough assessment of the internet systems, potential losses due to data breach, internal control processes, staff knowledge of cyber risk, readiness of managing an incident and potential damage to reputation.
With a deep understanding of the potential losses, either financial or reputational, risk appetite for cyber risk can be set according to the company’s willingness and ability to take cyber risk.
Like other risk types, the risk appetite for cyber risk can be defined using quantitative measures such as capital at risk (CaR) and earnings at risk (EaR) or qualitative statements such as no material damage to the company’s reputation and no interruption of the business caused by cyber risk are acceptable.
An example of appetite for cyber risk could be:
- The company cannot lose more than 10% of International Financial Reporting Standards (IFRS) equity in a single cyber risk event or a series of related cyber risk events.
- The company has extremely high risk aversion to reputational risk caused by cyber security failures.
- The company has a contingency plan in place for continuing business operations in the event of an internet system failure or a cyberattack.
Here the 10% should be supported by quantitative analysis of cyber risk exposure. Setting the risk appetite for cyber insurance in a quantitative way requires experience data, expert opinions and sophisticated modeling to incorporate the changing environment.
The percentage can also be roughly estimated as the percentage for noncyber operational risk multiplied by the relative extremity of cyber risk compared to noncyber operational risk.
Hybrid Model Cyber Insurance

The uncertainty of cyber risk, the increasing use of the internet of things to share information and data privacy concerns often lead to insufficient experience data for measuring the exposure to cyber risk. Even with sufficient data, some impact of cyber risk, such as the damage to reputation, is difficult to quantify.
A hybrid model is a model that uses both limited experience data and experts’ input to evaluate cyber risk exposure. Given the significant amount of input from a variety of experts, the model also needs to be able to consistently incorporate subjective input and draw conclusions.
Hybrid models such as fuzzy logic models can be used to evaluate cyber risk exposure. Fuzzy logic models are built on fuzzy set theory and fuzzy logic. The models allow an object to belong to more than one exclusive set with different level of confidence. They are useful for analyzing risks with insufficient knowledge or imprecise data. Shang and Hossen (2013) studied the application of fuzzy logic models to risk assessment.
Available experience data can be used to help calibrate the quantitative part of the model, which describes the characteristics of key risk indicators (KRIs). Expert opinions on KRIs and their relationships to cyber risk exposures can be incorporated into fuzzy logic models as well. Consistent inference rules used in fuzzy logic models help reduce the adverse impact of human biases normally seen in qualitative risk assessment.
Fuzzy Logic Model Structure
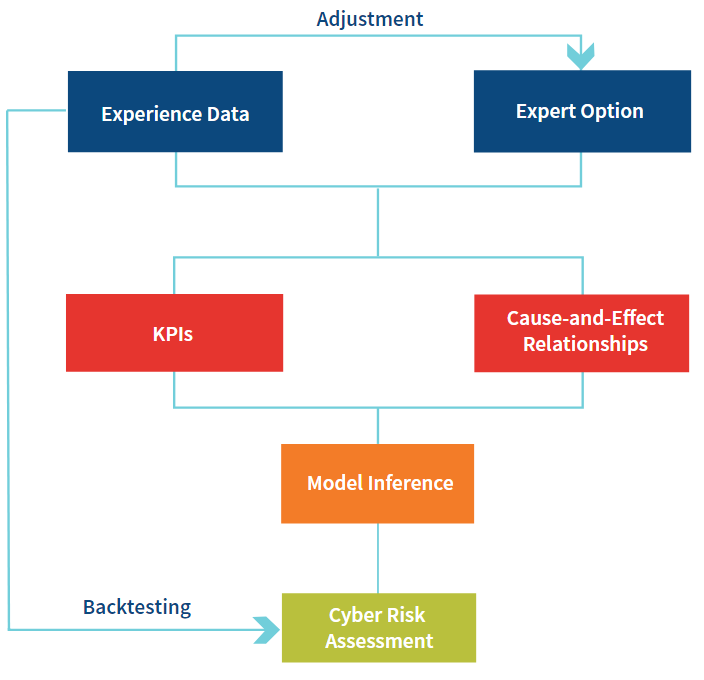
Given that the knowledge and experience of cyber risk evolve quickly, fuzzy logic models make the assessment of cyber risk both flexible and consistent.
Experts need to compile a list of key indicators of cyber risk considering the company’s IT infrastructure, business and data.
Most of the indicators are not quantifiable and need to be rated to represent the degree of confidence that the current level is high, medium or low.
Sample Key Risk Indicators for Cyber Security
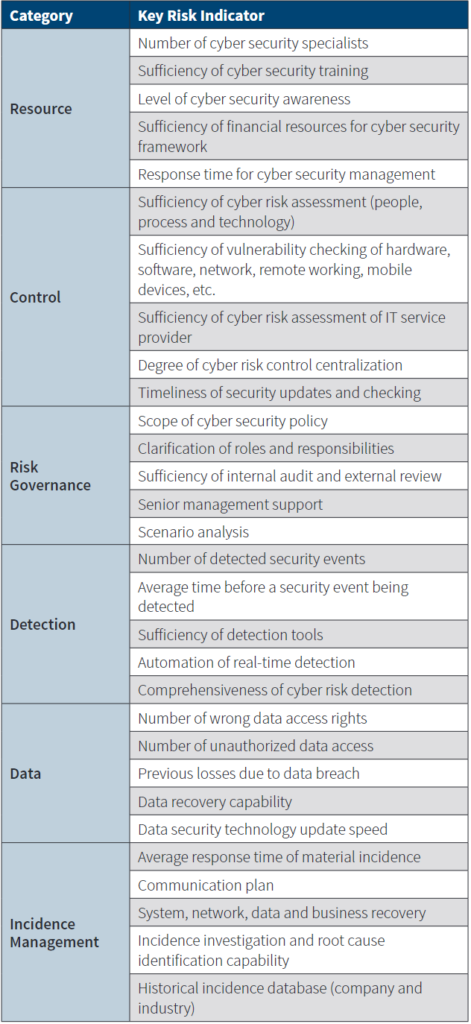
Expert opinions on the relationship between these indicators and the risk assessment result for each category aggregate cyber risk level are needed. For example, if the number of detected security events is not high and the average time before a security event being detected is long, the risk of cyber event detection is high. With the indicators and cause-and-effect relationships, fuzzy logic models can be used to calculate the level of cyber risk, indicating both frequency and severity. New experience data can be used to backtest prior cyber risk assessment results. Experts may also change their opinions after digesting new knowledge and new experience.
Cyber Risk Management
The risk appetite for cyber risk sets the high-level strategy regarding cyber security. However, like other operational risks, proactive management is important to make sure that the cyber risk tolerance level will not be exceeded. Most approaches used for managing operational risks can be adjusted and used for cyber risk management.
Components of Active Cyber RiskManagement
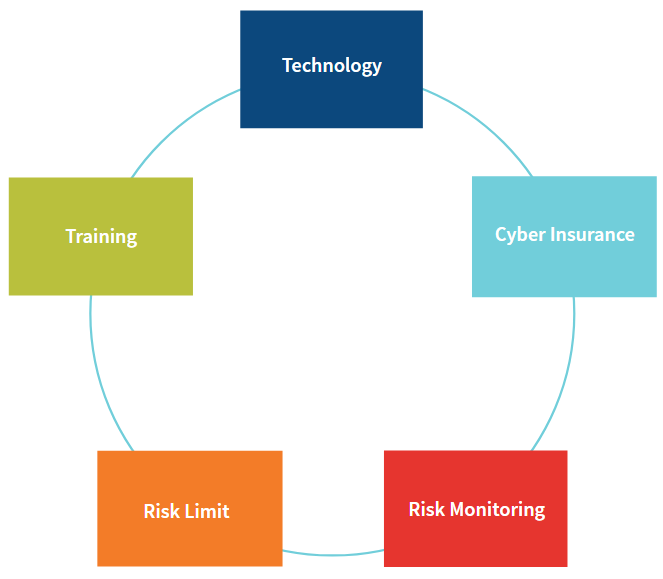
Investment in new technologies is important. New technologies can help identify the sources of cyber risk, prevent cyberattacks and maintain robustness of the internet system. New forms of cyber risk emerge every day, and the technologies used to combat cyber risk also evolve quickly. Even though new technologies may be too expensive to use now, it is important to understand their functions and applications so that they can be adopted when it is economical and necessary to do so.
Cyber risk training can help employees understand the sources and formats of cyberattacks, detect the existence of these attacks, follow precautious procedures and be able to take timely actions to mitigate their impact.
Risk limit setting for cyber risk is quite different from other risk types. For example, limits for insurance risk can use quantitative measures such as net amount at risk and mortality/morbidity/lapse experience. With the risk appetite setting the risk tolerance for cyber risk, the company’s internet system, data attractiveness to cyber criminals and employee awareness need to be assessed to understand the current level of cybersecurity.
KRIs for cyber risk need to be designed based on the company’s specific business, data and system. Possible KRIs may include the number of system breakdowns per month, number of users with access to key sensitive data, the level of risk awareness measured by the training that has been taken by employees and the average length of time before a cyberattack is detected (see What are the Most Common Types of Cyberattacks?).

Limits can be set by making reference to pioneers in cyber risk management while at the same time making adjustments according to the company’s situation.
Cyber risk monitoring is difficult because of the risk’s wide scope and fast evolution. Focus needs to be put on key data and key system protection, as the monitoring is unlikely to be complete and perfect.
Because cyber risk events can happen quickly, the monitoring frequency needs to be higher than most other risk types such as insurance risk. The monitoring should include not only checking the current risk exposure against the risk limit, but also automatic and real-time monitoring of the internet system, communication system (email, phone, etc.) and social media data to identify any issues that could lead to a cyber risk event.
Monitored issues may include a break of system security policies and procedures, malware, inappropriate user privileges, irregular system activities, communication to outside systems such as a third-party system or a home computer, key data access and transfer and so on.
A contingency plan is critical to managing losses, either financial or reputational, caused by cyber risk events. An action plan can help the company quickly respond to a cyber risk event such as a data breach and a system failure.
It can help minimize business disruption and avoid being a headline on cyber security, or at least demonstrate the company’s determination and capability to manage cyber risk.
Cyber insurance can be used to transfer severe impact of cyber risk events to a counterparty. Even with heavy investment in technology, training and active risk monitoring, unexpected cyber risk events can still happen. Cyber insurance adds an extra layer of protection to cover unexpected losses.
Proactive cyber risk management is needed because cyber insurance does not cover all losses, and good cyber risk management can reduce the exposure to cyber risk and therefore get lower cyber insurance premiums.
If a counterparty insures a huge amount of cyber risk, its ability to pay the promised benefits needs to be assessed because cyber risk events can affect many companies and personal users at the same time.
Conclusion
Cyber risk has become a top risk for the insurance industry with the embrace of the digital world and the internet of things. Cyber risk shares many features with other operational risks but is considered a fast-evolving and more influential risk in the future.
Like other risks, risk appetite for cyber risk is useful for setting the high-level risk tolerance.
However, it needs sophisticated modeling that can leverage both limited experience data and subject matter expertise in a consistent way. Proactive measures such as technology investment, training, risk monitoring and cyber insurance are important to control cyber risk exposure and keep pace with the development of new cyber risks.
…………………………
AUTHOR: Kailan Shang – FSA, CFA, PRM, SCJP, cofounder of Swin Solutions








