Since the war began, governments, companies, civil society groups and countless others have been working around the clock to support the Ukrainian people and their institutions. Cyberwarfare has provided just a handful of notable skirmishes in the Russia-Ukraine War. But fears linger that the scale and frequency of digital attacks on financial, industrial, and state targets in Ukraine, and among its allies, could escalate, according to S&P Global Ratings analysts and cyber experts.
Realization is changing the dynamic of cyber risk management, pushing damage limitation to the forefront and, as a result, turning the spotlight on attack detection.
Thankfully, defenders don’t have to face the threat posed by accelerating cyberattacks alone. Government organizations are playing a growing role in incident detection.
Issuers that quickly detect an attack afford themselves a chance to break the attack lifecycle at an early stage and thus limit financial damage and potential credit quality impacts. An attacker doesn’t gain access to a target’s systems until step three of five (exploitation) in the attack lifecycle (see (Re)Insured Losses for Ukraine War & Ultimate Industry Loss Outlook).
Risk of cyberattacks on public and financial entities

A catastrophic cyber attack is the top scenario in 2023 resilience plans. Such an attack would surely put C-suite alliances to the test. Cybersecurity has become a more dynamic field, rapidly adjusting and shifting to keep apace with business inventiveness.
There is a rising likelihood of a prolonged stalemate, or an escalation in military attacks, and with that we see heightened risk of cyberattacks on public and financial entities
Zahabia Gupta, S&P Global Ratings’ associate director in the Sovereign and International Public Finance team.
S&P are monitoring whether any cyberattacks on Ukraine could cause disruptions to payment systems or critical infrastructure that could affect its ability to service debt (see Cyber Security Top Trends & Cyber Attack Threats).
This risk is incorporated into our ‘B-/B’ sovereign ratings on Ukraine, which remain on CreditWatch negative.
Russia cited for hacking Ukrainian targets

History suggests there is good reason to be wary. Russia is often cited for hacking Ukrainian targets, though it denies the allegations. A 2015 attack temporarily turned off power for about 230,000 Ukrainians.
Two years later, hackers, reputed to be linked to Russia’s military, knocked government agencies offline, shut transport systems, closed banks, and cost U.S. and European companies that were inadvertently caught in the attack about $10 bn.
Russia could use cyberattacks to target entities from countries that are allied with Ukraine as a means to gain an advantage in the conflict.
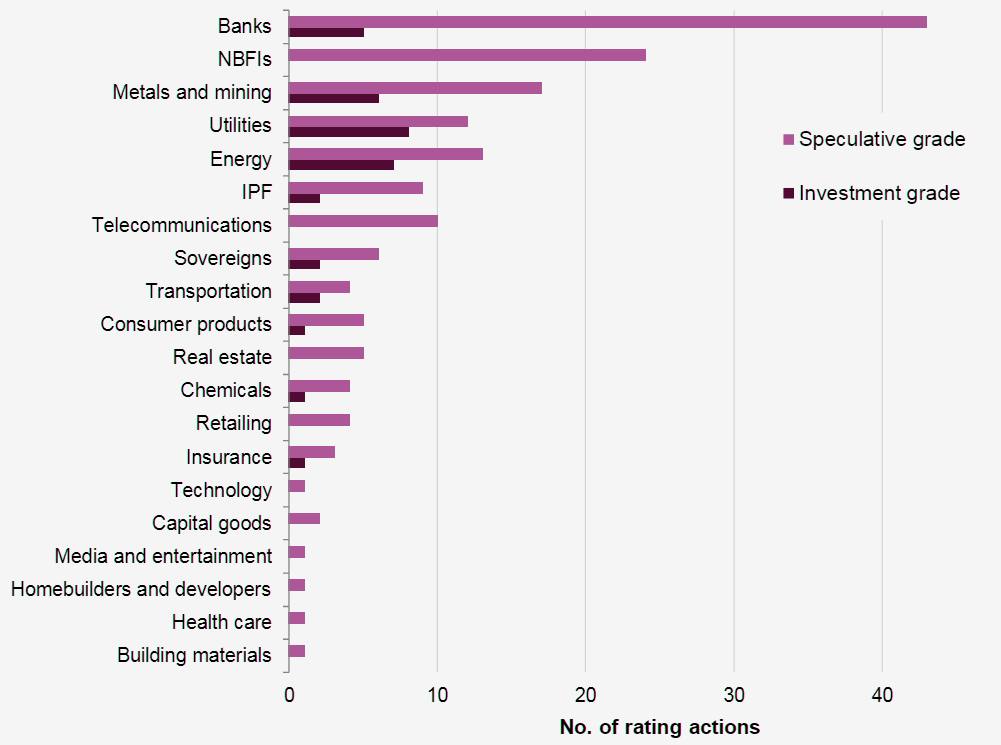
For the time being, cyberattacks have been less severe than we expected. Of the about 201 rating actions we have taken as a result of direct or indirect consequences of the war, none have been due to cyber-related issues.
Rating actions by sector since the start of Russia-Ukraine War
The average cost of a cyber breach lasting 200 days or more was $4.86 million, technology company IBM said in its “Cost Of A Data Breach Report“.
Sums like that underline the importance of detection to companies’ cyber risk management. And they highlight why S&P Global Ratings considers effective cyber detection to be integral to cyber risk management and ultimately a potential factor in the assessment of issuers’ credit worthiness.
Cyberattacks are something we are closely watching, [but] they haven’t thus far been a major contributor to any of these rating actions
Tiffany Tribbitt, S&P Global Ratings director and lead analyst for U.S. public finance
To better understand the role that detection plays in cyber risk management it helps to understand the nature of a typical cyberattack (see What are the Most Common Types of Cyberattacks?). Contrary to common perception, cyberattacks are not singular events.
How the Ukraine conflict transformed the cyber threat landscape?
Russian government-backed attackers have engaged in an aggressive, multi-pronged effort to gain a decisive wartime advantage in cyberspace, often with mixed results.
This includes a significant shift in various groups’ focus towards Ukraine, a dramatic increase in the use of destructive attacks on Ukrainian government, military and civilian infrastructure, a spike in spear-phishing activity targeting NATO countries, and an uptick in cyber operations designed to further multiple Russian objectives. For example, we’ve observed threat actors hack-and-leak sensitive information to further a specific narrative.
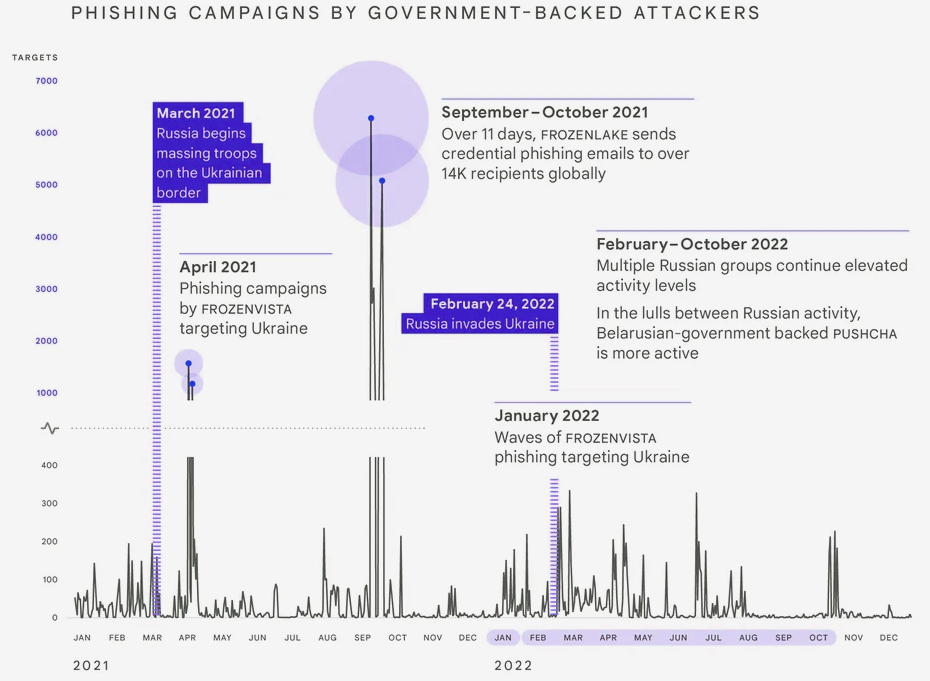
Russian government-backed attackers ramped up cyber operations beginning in 2021 during the run up to the invasion (see How Russian War in Ukraine Impacts for Global Insurance Sector?).
In 2022, Russia increased targeting of users in Ukraine by 250% compared to 2020. Targeting of users in NATO countries increased over 300% in the same period.
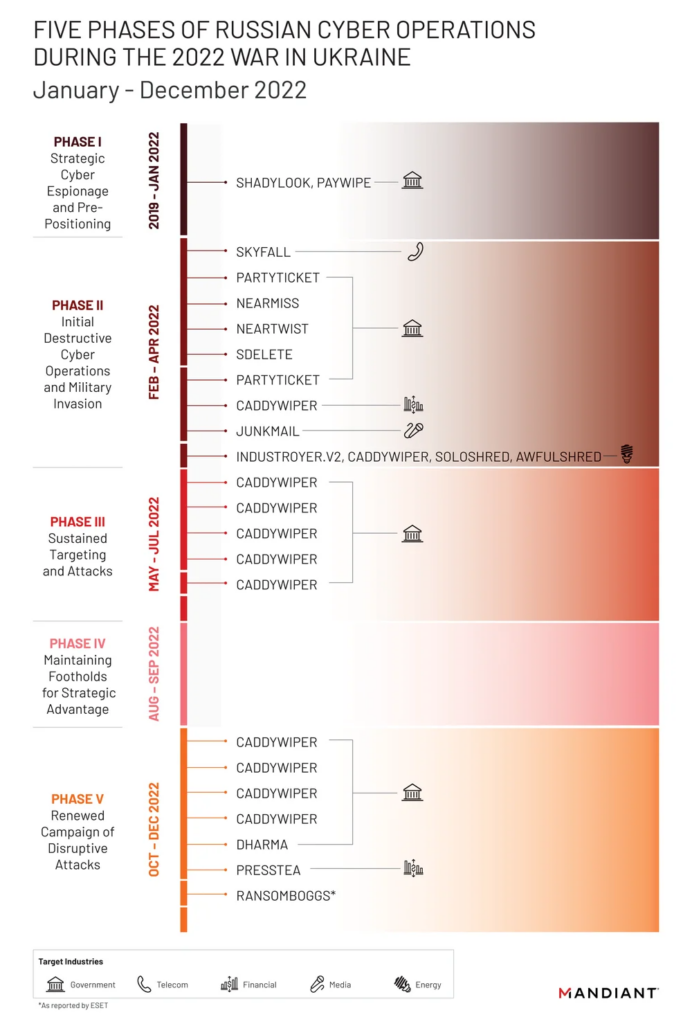
From its incident response work, Mandiant observed more destructive cyber attacks in Ukraine during the first four months of 2022 than in the previous eight years with attacks peaking around the start of the invasion.
While they saw significant activity after that period, the pace of attacks slowed and appeared less coordinated than the initial wave in February 2022.
Specifically, destructive attacks often occurred more quickly after the attacker gained or regained access, often through compromised edge infrastructure.
Many operations indicated an attempt by the Russian Armed Forces’ Main Directorate of the General Staff (GRU) to balance competing priorities of access, collection, and disruption throughout each phase of activity.
Moscow has leveraged the full spectrum of IO – from overt state-backed media to covert platforms and accounts – to shape public perception of the war.
These operations have three goals:
- Undermine the Ukrainian government
- Fracture international support for Ukraine
- Maintain domestic support in Russia for the war
We’ve seen spikes of activity associated with key events in the conflict such as the buildup, invasion and troop mobilization in Russia.
The invasion has triggered a notable shift in the Eastern European cybercriminal ecosystem that will likely have long term implications for both coordination between criminal groups and the scale of cybercrime worldwide.

Some groups have split over political allegiances and geopolitics, while others have lost prominent operators, which will impact the way we think about these groups and our traditional understanding of their capabilities.
We’ve also seen a trend towards specialization in the ransomware ecosystem that blends tactics across actors, making definitive attribution more difficult.
Shane Huntley – Senior Director, Threat Analysis Group at Google
The war in Ukraine has also been defined by what we expected but didn’t see. For example, we didn’t observe a surge of attacks against critical infrastructure outside of Ukraine.
TAG also sees tactics closely associated with financially motivated threat actors being deployed in campaigns with targets typically associated with government-backed attackers. In September 2022, TAG reported on a threat actor whose activities overlap with CERT-UA’s UAC-0098, a threat actor that historically delivered the IcedID banking trojan, leading to human-operated ransomware attacks.
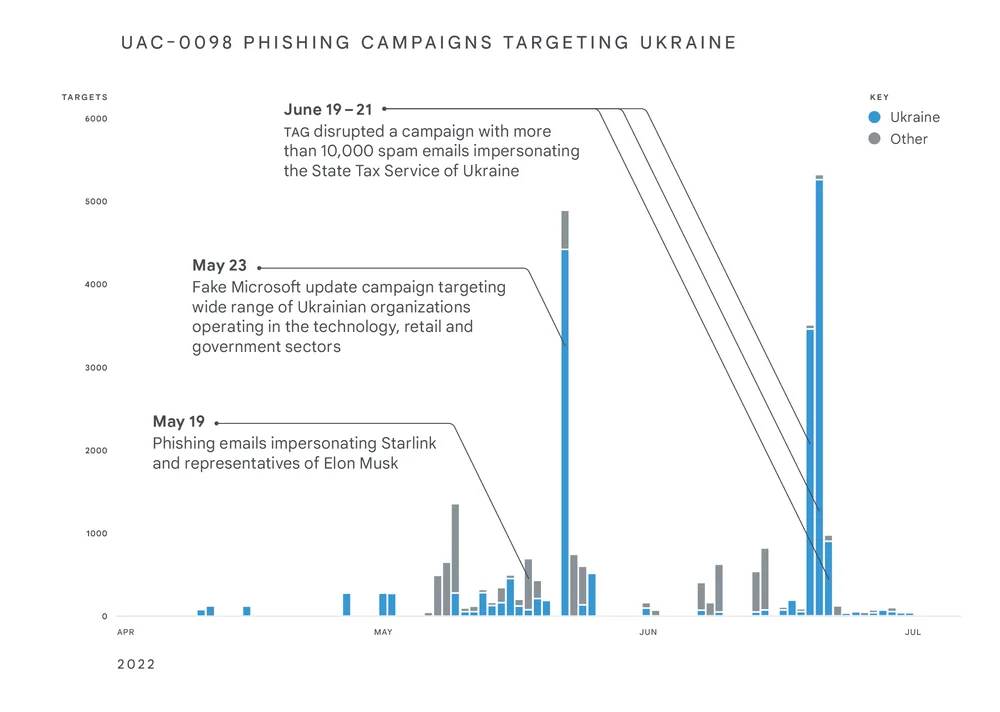
The War hasn’t been without a cyber element
The Ukrainian defense ministry and two banks were hit with distributed denial-of-service (DDoS) attacks, which seek to take down websites by overloading them with fake queries, in the days before the invasion began.
Other Ukrainian government sites have suffered “web defacement,” a form of digital vandalism.
There have also been accounts of more destructive, though largely unsuccessful, activity, including the use of wipers, malicious programs that seek to destroy IT systems by erasing data.
We have seen several wipers in play recently, some created before the hostilities occurred and some during
Paul Alvarez, a cyber risk expert within our Analytical Innovation team
Wipers have a notorious history in Ukraine. It was a wiper malware, called NotPetya, that in 2017 exploited two historical weaknesses in Microsoft’s operating systems to disable Ukrainian airports, railways, and banks.
NotPetya was a culmination of a Russian campaign
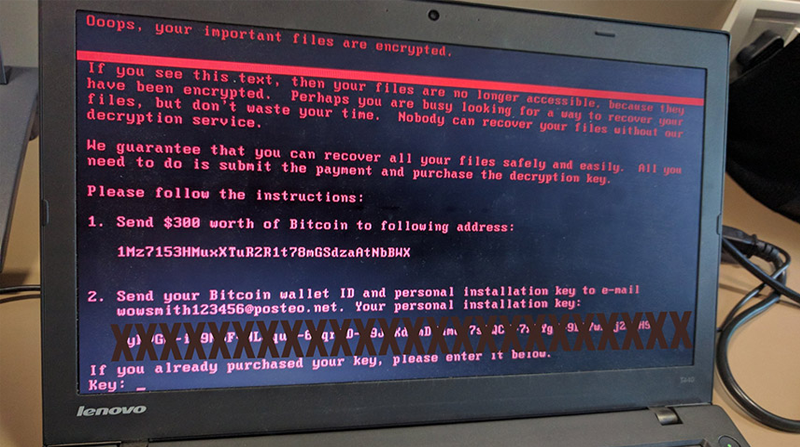
NotPetya was actually the culmination of a three-year campaign of targeted disruption against Ukrainian infrastructure…banks, nuclear plants, and electricity suppliers.
It wasn’t a well-controlled campaign in that it may have been targeted at Ukraine, but a number of really large organizations got hit by NotPetya, even though it wasn’t designed to actually attack them.
Among the collateral damage was drug maker Merck & Co and transportation group FedEx, which suffered about $695 mn and $400 mn of losses, respectively, making them significant corporate contributors to a total of about $10 bn of losses caused by the attack.
Still, this did not lead to any rating actions, since analysts assessed the credit implications as manageable within the current rating thresholds.
The shockwaves of NotPetya also reverberated through the insurance sector, which found itself on the hook for about $3 billion of damage claims (the remaining $7 billion was uninsured).
Worse, for the insurers, about $2.7 billion of those claims were likely unforeseen, since they came via traditional property and casualty (P&C) polices that neither explicitly included nor excluded losses from cyberattacks.
Businesses are still over reliant on their insurance policies to cover cyber exposure
At best, silent cyber risks hurt insurers’ profitability by exposing them to payouts for risks for which they never collected premiums. At worst, it could harm their profitability and solvency levels.
A lack of clarity leads to disputes, with policyholders arguing for a more generous and broader interpretation of the wording, and insurers doing the opposite
Manuel Adam, associate director within the Insurance Ratings team
This is leading to dissatisfaction for policyholders. And it leaves the scope of coverage uncertain, particularly in the case of large scale cyberattacks like NotPetya, and potentially in the case of the current Russia-Ukraine conflict.
The extent of those risks was made explicit in January, when a court ruled that an all-risk property policy held by Merck entitled it to claim against damages resulting from NotPetya.
Merck’s insurer, Ace American Insurance, had argued that the cyberattack was an act of war, which would typically be excluded from a P&C policy.
A New Jersey Superior Court disagreed, ruling that Merck had every right to anticipate that the exclusion applied only to traditional forms of warfare.
Insurance Rate Increases did not offset combined ratio deterioration
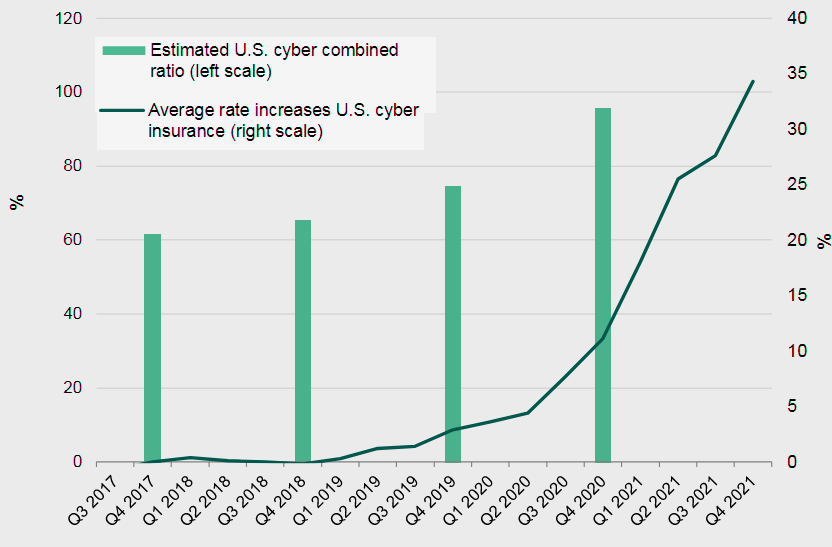
It is unclear to what extent that ruling will set a precedent. Yet cyberattacks emanating from the Russia-Ukraine conflict could once again test the arguments used in the case, including the extent to which insurers must prove that a cyberattack is directly linked to a conflict, and thus an act of war. That could prove a difficult task, particularly when belligerents are unlikely to claim responsibility.
Insurers are, either way, coming to terms with the need to identify, quantify, and manage silent cyber risks.
Progress has been made in moving clients to affirmative cyber coverage, but it has been hampered by a mismatch between strong demand for such policies and supply that is constrained by insurers’ caution, due to the relative infancy of cyber as an insured risk.
That imbalance has contributed to a sharp increase in cyber protection prices since mid-2020, though the increase isn’t likely to have been sufficient to protect profit margins that were in place before the COVID-19 pandemic.
Spotlight On Cyber Governance
There seems little doubt that demand for cyber insurance will grow, as the financial effects of cyberattacks increase. And there is the important question of how cyber insurance fits into overall cyber risk management?
Risk management, including cyber risks, is considered within our ratings process, weak governance protocols can lead to a lower rating than pure financials might otherwise indicate.
That is the reason why you don’t always see rating changes after an attack, governance risks are already baked into our ratings.
…………………..
AUTHORS: Zahabia Gupta – S&P Global Ratings’ associate director in the Sovereign and International Public Finance team, Tiffany Tribbitt – S&P Global Ratings director and lead analyst for U.S. public finance, Paul Alvarez – a cyber risk expert within our Analytical Innovation team, Manuel Adam – associate director within the Insurance Ratings team, Shane Huntley – Senior Director, Threat Analysis Group at Google Security








