Things have been tough recently in the cyber insurance industry. Businesses have a difficult time finding affordable policies with the right limits that don’t exclude ransomware (see Top Cybercrime Predictions).
Insurance companies could also assist their policyholders with loss control. Insurers should be aware of who is responsible for data breaches and how those breaches occur in order to assist their policyholders.
Cybercrime has catastrophic consequences in today’s corporate environment, including revenue and profit loss, brand ruin, erosion of consumer loyalty, competitive disadvantages, and, among other things, crippling lawsuits.
Following recent cyber attacks, organizations worldwide are beginning to see the crucial need for lifesaving protections that warn when risk is there. They understand that they need “risk sensors” to prevent dangerous scenarios from occurring and prevent inevitable cybercrime from becoming tragic when it appears (see Cybersecurity and the Cyber Insurance Market).
The term cyber business intelligence & cybersecurity

Underwriters suffer from the high claims associated with ransomware and struggle to return loss ratios to profitable levels. These challenging times, however, are forging a resurgence in cyber business intelligence – the idea that insights into cyber risk aren’t just for mature enterprises looking to avoid a breach.
Once they do, they will reverse the current profit loss trend into a highly profitable trend, companies will benefit from better policies more tailored to their unique risk profile and other industries that accept or deal with the transference of cyber risk will also flourish if they can recognize the opportunity to harness cyber risk intelligence.
Let’s start by leveling on the term cyber business intelligence and why it differs from cyber threat intelligence. In the mid 2010s, the term cyber business intelligence appears to have made a short run in the lexicon of cybersecurity, but terms like cyber threat intelligence or vulnerability assessments surged in prevalence (see Cyber Risk & Insurance Coverage for Businesses).
These terms differ because they imply a focus on introspection. The terms refer to activities where you assess yourself and your own risks or engage with an outside firm that will help you do those things.
At the time, the popularity of those terms were well earned. The disciplines of risk discovery were reaching maturity, aided by a maturing infosec industry with now well-established standards and best practices.
In other words, those were the areas where people needed to focus because they were so important at that time. Get your shield up, understand what types of things to look for and identify the tell-tale signs of danger (see 5 Most Important Cybersecurity Controls). The risk is real and you are holding the risk.
Cyber risks are considered as a top global risk for the financial sector and the economy as a whole. The type of ICT risks to which the undertakings are exposed have not changed in the past years, however the frequency of incidents and the magnitude of their impact on financial entities has increased. The frequency and severity of cyberattacks are ever increasing. Data breaches to steal personal information occur daily, but only the largest make the news.
Insurance will bring back cyber business intelligence

Now that the hierarchy of cyber needs had been met on this primary level, the hurdle of the 2020s presented itself. As we discovered that we are holding the risk, savvy businesses sought to transfer all or part of that risk (see about Global Cyber Market).
And that wasn’t a hurdle – until it was. As the age-old violence of “ransom” regained popularity through the ease at which attackers could execute and benefit from ransomware attacks, the increased transference of that risk caught the insurance industry off guard.
Before the era of ransomware, cyber insurance was a great way to make money
It could be fair to say that risk assessments weren’t rigorous or serious enough or that the underwriters didn’t truly understand the risk.
When times were simple, the old five-question survey during the application process where you answered questions like “how do you feel about your security” (only half joking) was just fine. It worked and it was profitable, but the old ways of assessing risk via surveys, assumptions and historical trends were very limited (see Cyber Insurance, Ransomware & Hybrid Warfare Outlook).
They served a purpose, but they were not agile enough to keep up with ransomware and whatever emerges as the next threat trend.
Because cyber insurance deals with risk that has been transferred, there is a subtle but powerful distinction from the need to understand your own risk. In many cases, insurance companies that can curate low risk pools and a favorable loss ratio can significantly improve profits. That’s not the only way they make money, but it is one way.
According to an IBM-Ponemon study, the average cost paid for each lost or stolen personal information record increased from $145 to $154. Cyber liability insurance products can help companies cover the costs of data breaches and ransomware.
The current cyber insurance market premium is $2.5 billion and is expected to grow substantially by 2023. Projections for 2023 are $5 billion (David Bradford, Advisen), $7.5 billion (PWC) and $10 billion (ABI) (see Cybersecurity Insurance Market Size)
This growth is evidenced by the number of recent rate, rule and form filings containing cyber coverages. A review of several rate filings (effective May 2016 or later) provides commercial cyber coverage for the direct data breach costs mentioned above. Some of the companies offer additional coverage for cyberattack costs, including extortion. Coverages do not appear to be available for theft of intellectual property.
Enter the resurgence of cyber business intelligence

While concepts like cyber threat intelligence and risk assessments focus on preventing loss, cyber business intelligence aligns with concepts already utilized elsewhere in a business environment.
“What pieces of knowledge and trends can I follow – that by following them I can be more profitable?” This is a different mindset. This is one anchored on the idea that “you’ve got to spend money to make money.” This drives a culture and enthusiasm that can foster better innovation, better results and faster progress.
There’s another key word there. Business. Not only relevant to technical experts, this information is equally relevant to business leaders and key decision makers.
Now the purpose of that intelligence is not just to maintain a shield. It can help drive an organization forward (see Biggest Cyber Unicorn Startups in the World).
Companies that receive transferred cyber risk provide fertile ground to sow new ideas around risk-related data and information as cyber business intelligence. The purpose of cyber business intelligence is to always be there to illuminate and guide leaders toward achieving more efficient and smarter business performance.
Why is Cyber Security Integral to Business Intelligence?

The actual data collected and stored by Business Intelligence (BI) systems requires tangible cybersecurity to support business intelligence operations. In this way, business intelligence operations become more economically viable, respected, and better equipped to protect the valuable yet compassionate data generated by IoT and IIoT technology.
Many people are unaware that businesses that keep a tight grip on their data are considerably better positioned to ward off cyberthreats than those that do not. The problem isn’t with data; it’s whether we have complete control over it.
The first step in managing and deploying data is to make mining and visualization analytics as simple as possible.
If you’re having trouble creating a system that works for your company, a business intelligence platform is an excellent place to start.
This situation bridges the gap between modern business intelligence tools and any outdated software you might still be using. Using embedded analytics, companies may also link reports, dashboards, and visualizations with essential applications and processes.
Cybersecurity and data governance are continuous commitments that need continuing focus and effort.
Cybercrime’s dynamic nature causes many issues for contemporary businesses. Still, it’s also a powerful motivator to maintain their databases clean, safe, and connected to an effective business intelligence system at all times.
It’s always best to do things ahead of time to protect digital infrastructure. It’s pointless to wait until a significant cyber assault has harmed you before taking action (see Global Cyber Crime, Fraud & Ransomware Survey).
Top businesses recognize the necessity of preventing substantial disruptions to their operations at all costs, which can only be accomplished by regularly upgrading and strengthening every area of their cybersecurity plan. It will eventually protect you if you keep your data safe.
The Cost of Insecure Business Intelligence

A data breach occurs when thieves obtain illegal access to a computer system or network to jeopardize or steal the private, proprietary, sensitive, or confidential personal, corporate, or financial data of users, customers, or businesses.
Businesses have been crippled or destroyed due to cyber security breaches in recent years.
Fines and penalties for data breaches are sometimes significant and devastating. GDPR offenders, for example, might face penalties of up to €20 million or 4% of their annual worldwide revenue for the previous financial year, whichever is higher.
In comparison to the GDPR, various federal and state agencies in the United States impose fines and punishments for data breaches that can be large in scope and have a similar commercial impact.
A data breach comes as a result of a cyberattack or insider actions that allows criminals to gain unauthorized access to a computer system or network to compromise or steal the private, proprietary, sensitive, or confidential personal, corporate, and financial data of the users, customers or the business enterprises.
Data breaches are no longer novel and unexpected due to the intensity and volume of attacks, which are growing from year to year. According to a recent data security reports by Cisco, 31% of organizations have at some point encountered cyber-attacks on their operations technology.
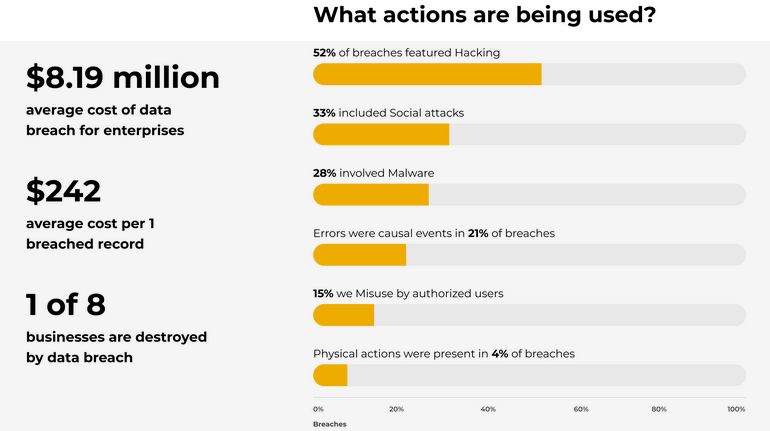
Cyber security solutions that detect sensitive data and assess its quality can assist businesses in minimizing the consequences of insufficient data and making better business decisions.
Businesses cannot afford to run on unsecured business intelligence platforms. Following an assault, the value of large firms is likely to plummet, and they will swiftly fall behind in today’s competitive global market.
Smaller groups, which are frequently underfunded, may never recover. Furthermore, cyber security may aid business intelligence by preserving high-quality data, allowing decision-makers to focus on tactical company plans.
Who is behind the Data breach?
According to the Verizon Data Breach report, 28% of all data breaches involved internal actors. While malicious outsiders (72%) were the leading source of data breaches, these made up only 23% of all compromised data. On the other hand, insiders accounted for 76% of all compromised records. The insider threat is indeed substantial.
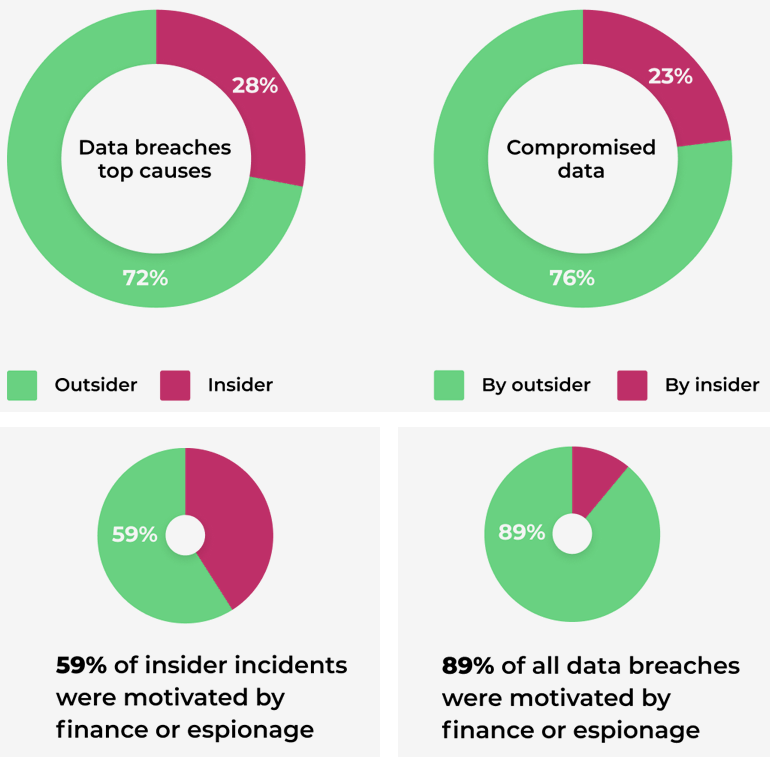
Insiders pose a significant threat to an organization’s cybersecurity. They have a number of advantages over outside attackers, as they have legitimate access to the organization’s network and know its cybersecurity system from the inside.
Data breaches are growing
The statistic shows the growing number of data breach incidents and the number of compromised records by year. Besides, the average cost of the data breach grows.
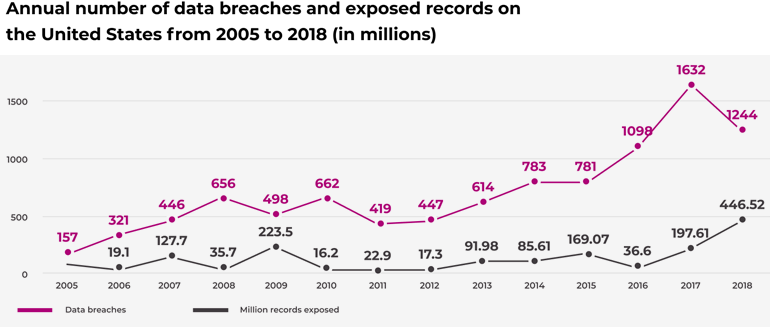
According to a study conducted by the Ponemon Institute and sponsored by IBM, the global average for breached records in 2018 was 24,615 per country, while 31,465 records were breached in the United States during the 12 months of the study review. The study also found that the average size of a data breach rose by 2.2 percent in 2018.
Over the past two years, the number of data incidents reported to the Information Commissioner’s Office (ICO), the UK’s data security authority, increased by 75%.
In the United States in 2017, the number of significant breaches totaled more than 1,300 compared to less than 200 in 2005.
How to protect your business?
To avoid data breach fines, penalties, stock price drops, and reputational damages that can drive business to liquidation, the business should implement the best security practices, protecting themself from both insider and outsider threats on both technical and non-technical sides.
Non-technical measures of the data breach prevention in the organization should include: set up corporate data security and management standards, follow GDPR / DPP and other national or state data protection and privacy regulations, educate employees on data breach threats and potential consequences of data leakage for the company and participants of the crime, enforce a strong Bring-Your-Own-Device policy, hire a data security and compliance officer, design a breach response plan, notify your team about the social engineering, phishing, viruses, and malware threats, etc.
Technical measures should include corporate antiviruses, firewalls, behavior analytics & reporting, data encryption, decentralized data storage, 2-factor authentication for accessing the data. Since one of the main sources of problems related to a data breach is that the sensitive information is stored unencrypted in easy access within centralized databases, where it can be easily stolen or compromised by insiders or hackers, the blockchain technology is becoming indispensable.
……………..
AUTHOR: Jacob Foster Davis – COO & Co-Founder at BreachBits, Vadi Ivanen – Global Head of Sales & Marketing at Optherium








