Overview
Cyber threat actors’ tactics, techniques, and procedures (TTPs) are constantly evolving, exposing cyber insurers to an ever-changing loss mix. Annual insured losses surged from under $100 mn pre-2017 to $4–6bn by 2025.
The shifting claims environment requires insurers to regularly re-evaluate development patterns to accurately assess performance and rate adequacy.
Cyber risk remains an unavoidable reality of doing business in a digitally connected world. Threat actors continue to demonstrate their relentlessness, evolving tactics to exploit new vulnerabilities and maximize financial gain.
Cyber is exposed to changes in loss trends at a pace not observed in other classes, according to Gallagher Re’s research about cyber development patterns. Beinsure analyzed the report and highlighted the key points.
Drawing on consolidated claims experience covering over $3 bn in GWP, Gallagher Re analyses whether the shifting claims mix is driving a change in development pattern. Beinsure analyzed the report and highlighted the key points.
The shifts in loss trends and therefore development patterns means that The Underwriting Years (UWY) specific development patterns need to be considered to accurately assess the ultimate position of any one UWY.
Key Highlights
- Cyber threat actors’ shifting tactics and techniques are reshaping loss patterns, forcing insurers to continually reassess claims development and rate adequacy.
- Ransomware evolved from low-severity encryption attacks pre-2018 to large-scale “big-game hunting” and, by 2021, double extortion involving both encryption and data theft.
- Annual insured ransomware losses grew from <$100mn before 2017 to $500mn+ by 2019, peaking at $5–7bn during 2020–2021. Current estimates remain high at $4–6bn annually.
- Encryption-only ransomware claims resolved quickly, but double extortion introduced long-tail elements similar to data breaches, extending investigation, compliance, and liability costs.
- Insurers now impose stricter underwriting standards, requiring multi-factor authentication, endpoint monitoring, and response planning, while pricing policies based on insureds’ cyber maturity.
Cyber insurers face shifting loss patterns as ransomware evolves from simple encryption to double extortion and targeted attacks (see How AI is Transforming Cyber Insurance).
Stricter underwriting, stronger security requirements, and risk-based pricing now define the market as insurers adapt to complex, evolving threats.
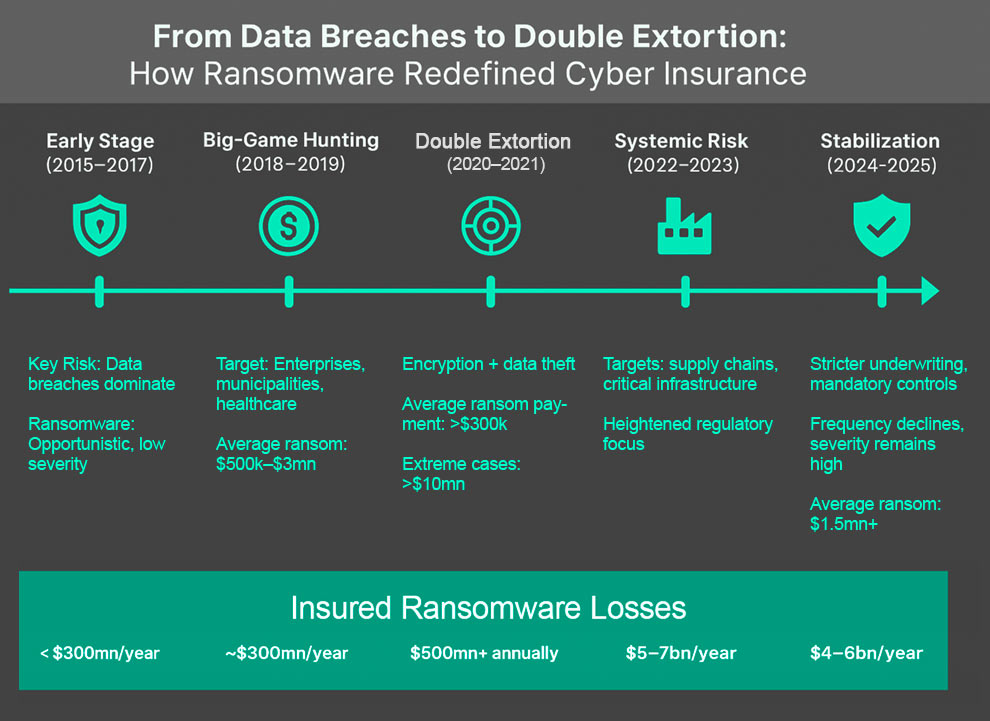
Timeline of Ransomware Evolution and Cyber Insurance
Ransomware: 2017 vs. 2025 Snapshot
| Metric | 2017 (Pre–Big Shift) | 2025 (Stabilization Phase) |
| Typical attack type | Opportunistic encryption ransomware | Targeted double extortion + data theft |
| Average ransom demand | <$50k | $1.5mn+ |
| Largest observed ransom | <$1mn | >$10mn |
| Annual insured losses | <$100mn worldwide | $4–6bn worldwide |
| Claim discovery & reporting | Immediate | Immediate, plus extended investigations |
| Claim settlement timeline | Short (weeks–months) | Longer (months–years) |
| Main cost drivers | System restoration, ransom | Ransom, BI, regulatory fines, liability |
| Insurer underwriting focus | Breach response | Cyber hygiene, MFA, EDR, risk maturity |
2015–2017: Early Data Breach Dominance
Cyber insurers were largely focused on data breach exposures, including notification costs, regulatory penalties, and third-party liabilities.
Ransomware existed but losses were modest, generally under $100 mn annually in insured claims worldwide.
2018: The Rise of RaaS and Un-Targeted Ransomware
The growth of cryptocurrencies enabled easier ransom payments, while Ransomware-as-a-Service platforms allowed less sophisticated actors to launch attacks. Encryption-based ransomware spread widely, focusing on volume rather than high-value targets.
Insured ransomware claims climbed past $300 mn globally, marking the beginning of systemic growth in severity.
Cryptocurrency adoption enabled anonymous payments, while Ransomware-as-a-Service expanded access for attackers.
2018–2019: Shift to “Big-Game Hunting”
Threat groups began moving away from indiscriminate attacks, instead targeting enterprises with deeper pockets. Groups began targeting large corporations, municipalities, and healthcare providers.
Average ransom demands jumped from tens of thousands to several million dollars per incident. Insured ransomware losses reached $500 mn+ annually, according to Beinsure’s Outlook for Global Cyber Insurance Segment.
Victims faced higher ransom demands, and the risk profile for insurers shifted dramatically toward large-scale first-party losses.
2020–2021: Double Extortion Becomes Standard
Attackers began combining encryption with data theft, creating longer-tail exposures. Even if victims restored systems, criminals threatened to publish stolen data unless a ransom was paid.
Insured losses escalated sharply.
Average ransom payments exceeded $300k in 2020, with some topping $10 mn. Global insured ransomware losses surged into the multi-bn range—estimated at $5–7 bn annually, contributing to sharp premium hikes.
This created longer-tail exposures, combining elements of data breach claims with ransomware demands.
2022–2023: Supply Chain and Critical Infrastructure Attacks
Ransomware groups increasingly targeted managed service providers, cloud platforms, and critical infrastructure. High-profile cases, including pipeline and healthcare disruptions, underscored systemic risk.
Cyber insurance claims severity remained elevated, with insured ransomware losses holding in the $5–8 bn annual range.
Insurers responded by tightening underwriting, requiring MFA, endpoint detection, and incident response planning as conditions for coverage.
Regulators and insurers heightened scrutiny of cyber risk controls, driving changes in underwriting standards.
2024–2025: Market Stabilization and Risk Differentiation
Improved security practices, mandatory multi-factor authentication, and stricter underwriting helped stabilize ransomware claims frequency.
However, severity remained high, with average ransom demands in 2025 above $1.5 mn and insured losses estimated at $4–6 bn annually.
Insurers now differentiate more heavily on insureds’ security posture, with pricing and coverage reflecting risk maturity.
Carriers are increasingly pricing based on risk maturity, rewarding organizations with advanced controls and penalizing laggards.
Ransomware Evolution and Insurance Impact (2015–2025)
| Period | Threat Evolution | Claims Characteristics | Estimated Insured Losses |
| 2015–2017 | Data breaches dominate; opportunistic ransomware | Quick resolution, modest severity | <$100mn annually |
| 2018 | RaaS & cryptocurrency adoption; un-targeted ransomware | Volume-driven, rising severity | ~$300mn annually |
| 2018–2019 | “Big-game hunting” targeting large orgs | Higher ransoms ($500k–$3mn) | $500mn+ annually |
| 2020–2021 | Double extortion (encryption + data theft) | Longer-tail exposures, regulatory costs | $5–7bn annually |
| 2022–2023 | Supply chain & critical infrastructure targets | Systemic risk; stricter underwriting | $5–8bn annually |
| 2024–2025 | Stabilization & risk differentiation | Frequency declines, severity remains high | $4–6bn annually |
Comparing Ransomware and Non-Ransomware
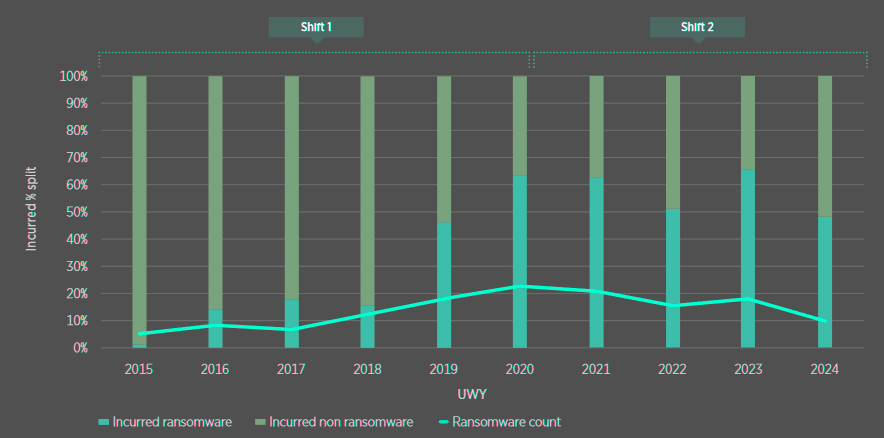
Ransomware has observed two notable shifts which may have altered development patterns:
- Shift 1: 2015-2020 – The Rise of Ransomware
- Shift 2: 2021-2022 – Ransomware Matures – Double Extortion
As cyber threats continue to evolve, businesses that take a proactive approach to managing and mitigating risk are experiencing the greatest successes.
The Rise of Ransomware
Until 2018, cyber insurers were primarily exposed to data breach claims. The emergence of cryptocurrencies and the rise of Ransomware-as-a-Service (RaaS) changed the threat landscape, fueling the spread of un-targeted, encryption-based ransomware attacks.
By 2018–2019, threat actors began to move beyond indiscriminate attacks, adopting a “big-game hunting” strategy that focused on larger organizations with greater ability to pay.
These attacks typically relied on encryption, with criminals demanding ransom payments soon after compromising systems.
Ultimate Average Cost Per Claim of Ransomware Losses by UWY
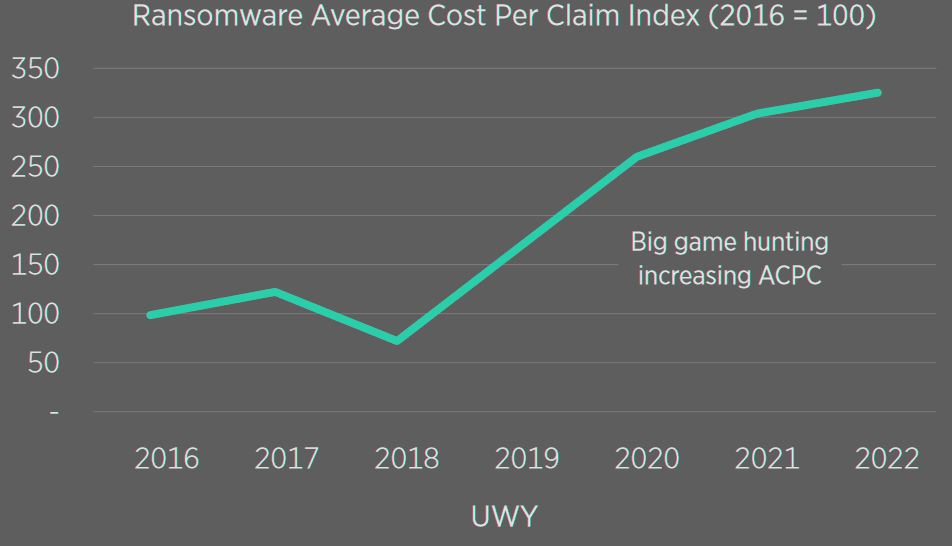
For insurers, ransomware claims differed significantly from traditional data breach exposures. They were generally identified and reported more quickly, and the financial impact could be quantified and settled in a shorter timeframe.
Timeline for Two “Traditional” Cyber-Attacks
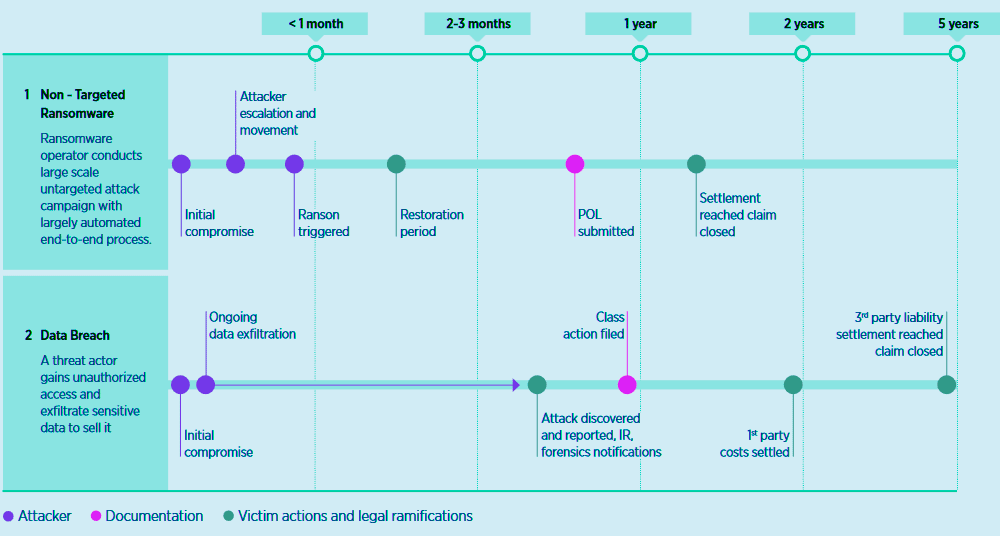
Data breaches, by contrast, carry long-tail third-party liabilities and extended notification and litigation costs, making them more complex and drawn out for insurers to resolve.
Ransomware Matures – Double Extortion
As insureds’ cyber hygiene improved to combat the threat of encryption-based ransomware, with the introduction of effective back-ups and restoration procedures, threat actors pivoted again to double extortion.
In addition to data encryption, threat actors would also steal information, using the threat of releasing the extracted data to ensure ransoms were paid.
The shift to highly targeted operations involving data exfiltration began prior to 2022.

- 2019: Ransomware groups like Ryuk adopted targeted attack methodologies, conducting extensive reconnaissance to infiltrate specific organizations.
- Late 2019: The Maze ransomware group pioneered the double extortion tactic, exfiltrating sensitive data before encrypting systems and threatening to publicly release the information if ransoms were not paid. This approach was soon emulated by other ransomware operators.
- By late 2021: These targeted, data-exfiltrating ransomware attacks had become the norm, with groups like Conti adopting exfiltration-first strategies to pressure victims into paying ransoms.
The incorporation of data breaches into ransomware attacks has altered claim timelines and complexities.
Timeline for a Targeted Ransomware Attack Involving a Data Breach Element
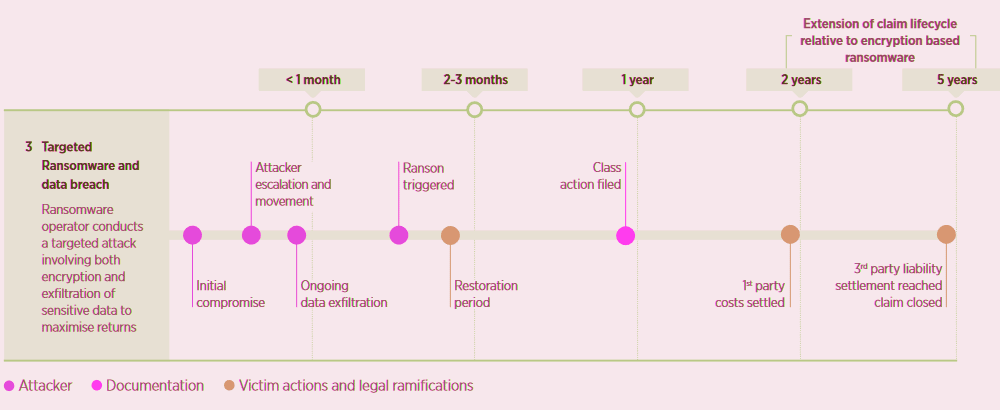
The need for forensic investigations, regulatory compliance, and potential liability due to data breaches extends the lifecycle of claims, contrasting with the quicker resolution periods of earlier ransomware incidents.
Ransomware vs. Data Breach Claim Dynamics
| Factor | Ransomware (Encryption-Based) | Ransomware (Double Extortion) | Data Breach |
| Discovery & Reporting | Immediate, often within days | Immediate + extended due to exfiltration | Often delayed |
| Settlement Timeline | Short (weeks–months) | Longer (months–years) | Long (years) |
| Cost Drivers | System restoration, ransom payment | Ransom + regulatory + liability costs | Notification, litigation |
| Claim Tail | Short | Medium to long | Long |
Impact of Claims Mix Changes on Development Patterns
Between 2019 and 2021 (orange box), the paid to incurred ratios were higher compared to 2018 and prior, which as hypothesised is likely driven by the shift in loss mix towards a greater proportion of encryption based ransomware incidents with a shorter tail relative to data breach losses.
For the period of 2022-2023 (blue box), the data appears more consistent with pre-2019 figures.

This change could be due to the transition from encryption-based ransomware to double extortion, where the additional third-party elements is decelerating payment and development patterns.
Drawing definitive conclusions from this data alone is challenging, due to:
- Russia’s invasion of Ukraine in 2022 disrupted the normal operations of many threat groups, which altered the loss mix again. 2022 appears to be an outlier with significantly lower paid to incurred ratios
- The disruption of operations drove a reduction in frequency predominantly within smaller losses, leaving a cohort of larger losses, which tend to develop slower due to the claims complexity. Leading to a greater delay when assessing liability, business interruption and significant first party costs
- Whilst current ULR projections suggest that 2022 will outperform other UWYs, we note this presents an uncertainty (which may be adverse or favourable) to the magnitude of the outperformance
The Paid to Incurred Ratio Development by UWY
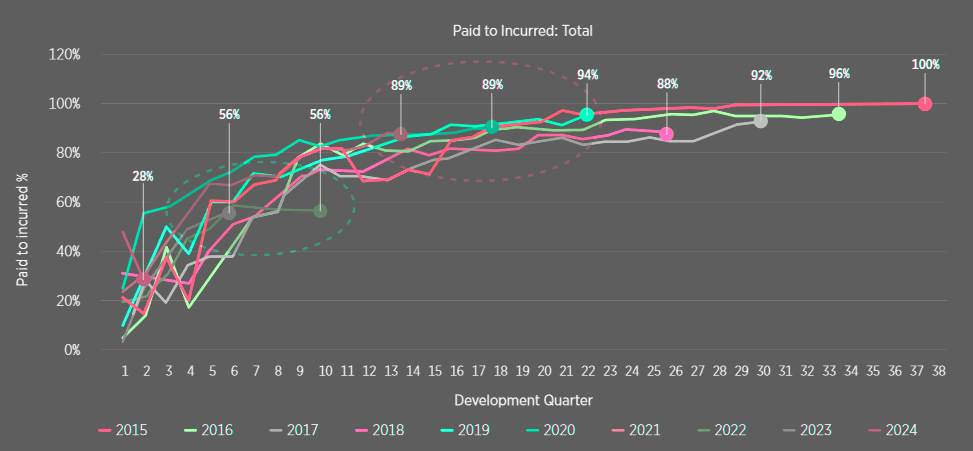
Paid-to-Incurred Ratios by UWY (Indicative Trends)
| UWY Period | Dominant Loss Mix | P/I Ratio Trend | Drivers of Change |
| 2015–2018 | Data breach heavy; limited ransomware | Lower P/I ratios | Long-tail exposures, slow claim settlement |
| 2019–2021 | Surge in encryption-based ransomware | Higher P/I ratios | Faster resolution of short-tail ransomware claims |
| 2022 | Disrupted by Russia–Ukraine conflict | Significantly lower | Reduced frequency, skew toward larger/complex cases |
| 2022–2023 | Double extortion ransomware dominates | Ratios decrease again | Longer-tail claims due to exfiltration & liability |
| 2023–2024 (mature) | Mix of ransomware + breach exposures | Returning to pre-2019 | Third-party aspects reasserting longer development |
To evaluate the potential impact of the shift from encryption-based ransomware to double extortion, we conduct a more granular analysis of claims categorised by type, focusing specifically on ransomware and non-ransomware claims.
Underwriting Shifts Over Time
| Period | Key Underwriting Response |
| Pre-2018 | Focus on breach response, limited ransomware underwriting |
| 2018–2019 | Introduced higher scrutiny on backups and restoration |
| 2020–2021 | MFA, endpoint detection, incident response plans required |
| 2022–2023 | Stricter loss modeling, higher premiums for poor cyber hygiene |
| 2024–2025 | Risk-based pricing tied to security maturity & controls |
The Paid to Incurred Ratio Development for Ransomware and Non Ransomware Losses
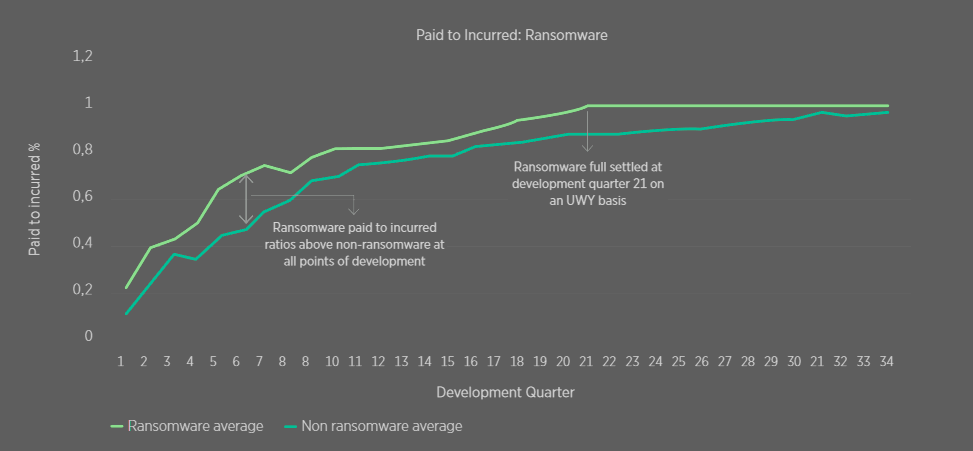
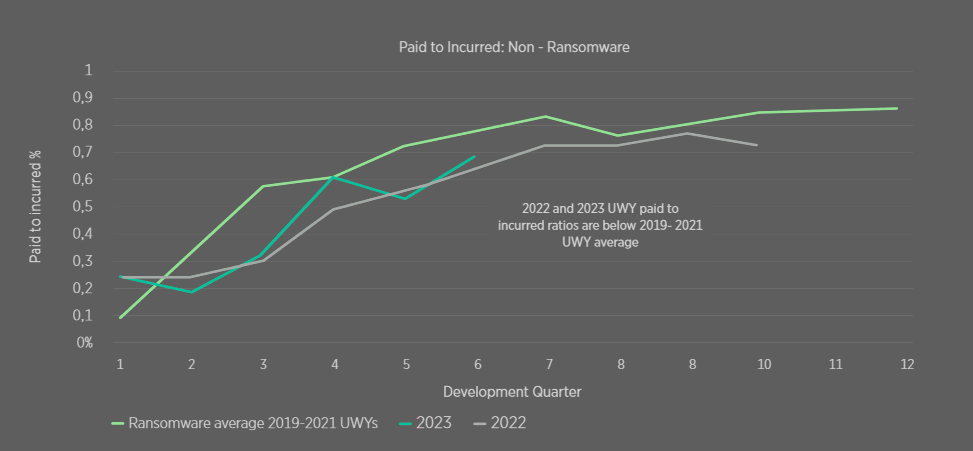
Comparing ransomware and non-ransomware paid to incurred ratios further shows that the shift observed in 2019 across all losses is likely driven by the increasing proportion of ransomware losses.
2022 and 2023 paid to incurred ratios appear to have decreased relative to 2019-21, which could support the hypothesis that double extortion is extending the development tail. We note the uncertainty in the data due to 2022, the immaturity and low volume, and therefore we are unable to draw strong conclusions at this stage.
Effects of Historical Development on Current Development Tails
In 2023 and 2024, the market observed prior year developments across several relatively mature underwriting years (UWYs).
This highlighted the importance of ensuring that the development tail accurately represents the long-tailed third-party aspects of cyber insurance.
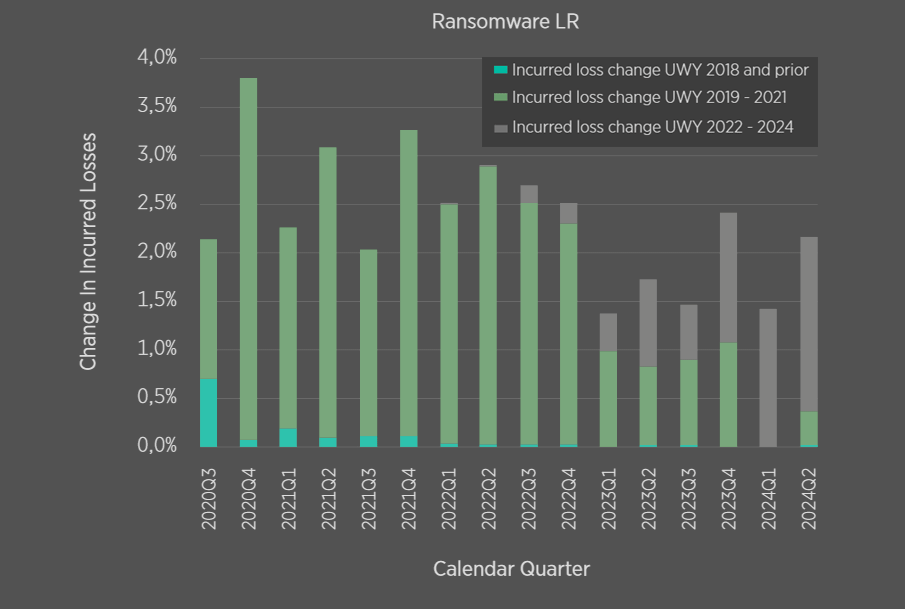
Development Pattern of Incurred Claims Categorised by Ransomware Types
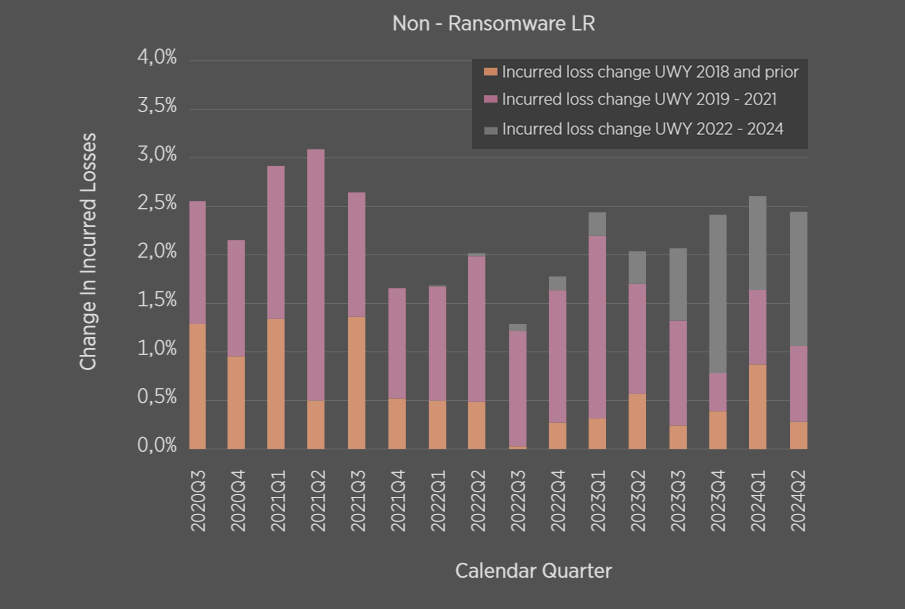
Development Pattern of Incurred Claims Categorised by Non Ransomware Types
Impact of Ransomware Evolution on Claim Development
| Ransomware Type | Claim Tail | Typical Costs Involved |
| Encryption-only (pre-2020) | Short (weeks–months) | System restoration, ransom, limited BI |
| Double extortion (2021–22) | Medium–long (months–years) | Ransom, regulatory fines, liability, notification |
| Data breach (all years) | Long (years) | Regulatory compliance, litigation, monitoring |
The data suggests that patterns are continuing to shift and therefore separate development patterns are required by loss type, which further require adjustment over time as threat actors tactics evolve.
FAQ
Cyber threat actors continually change tactics, techniques, and procedures (TTPs), which shifts the types of losses insurers face. This volatility forces insurers to regularly reassess development patterns to maintain accurate performance metrics and rate adequacy.
Early ransomware claims were largely encryption-based and settled quickly. As threat actors adopted “big-game hunting” and later double extortion tactics, claim complexity increased, extending the lifecycle of losses and aligning them more closely with long-tail data breach claims.
Cryptocurrencies enabled anonymous ransom payments, while RaaS lowered barriers to entry for attackers. Together, these developments in 2018 fueled widespread, un-targeted ransomware attacks and drove insured ransomware claims above $300mn globally.
Beginning in 2019 and becoming mainstream by 2021, ransomware operators began exfiltrating sensitive data in addition to encrypting systems. This shift added regulatory, liability, and notification costs to ransomware incidents, slowing settlement and extending claim tails.
Insured ransomware losses escalated from under $100mn annually before 2017 to $500mn+ by 2019. By 2020–2021, annual insured losses surged into the $5–7bn range. While frequency has stabilized, severity remains elevated, with losses in 2024–2025 estimated at $4–6bn annually.
Carriers are demanding stronger cyber hygiene—such as multi-factor authentication, endpoint detection, and incident response plans—as conditions for coverage. Insurers are also differentiating more heavily on insureds’ security maturity, with pricing tied to risk management practices.
Because ransomware and data breach losses develop differently, UWY-specific patterns must be applied to accurately assess ultimate results. For example, encryption-based ransomware created shorter-tail losses around 2019, while double extortion in 2021–2022 extended claim development.
………….
AUTHORS: Patrick Brooke, FIA – Head of UK Cyber Analytics at Gallagher Re, Aurelia De Maleissye – Cybersecurity & Digital Risks Consultant at Gallagher Re, Leah Merryweather – Cyber Actuarial Analyst at Gallagher Re
Edited by Yana Keller — Insurance Editor at Beinsure Media









