Logpoint’s research has uncovered the Akira ransomware infection chain through malware analysis. Akira actively targets Cisco ASA VPNs without multifactor authentication to exploit CVE-2023-20269 as an entry point for their ransomware.
The group primarily targets organizations in the UK and US within various industries, including education, finance, real estate, manufacturing, and consulting.
The gang employs several different malware samples in their campaigns, which initiates a series of steps when executed to encrypt victim files, including shadow copy deletion, file and directory search, and enumeration and encryption process (see Future of Global Cyber Insurance Market – Ransomware Challenges).
Since its emergence in March this year, it already has a trail of victims, and there’s no suggestion that the activity level is decreasing. It’s quite the contrary, as the number of victims increases each month.
Akira ransomware is sophisticated malicious software designed to encrypt files on a victim’s system, delete shadow copies, and provide instructions for ransom payment and data recovery. It employs encryption algorithms, exclusion criteria, and a TOR-based communication system to perform malicious operations.
Akira has shown itself as incredibly active and quickly built an extensive victims list. With every campaign, the gang evolves with new features and capabilities
Swachchhanda Shrawan Poudel, Logpoint Security Research Engineer
The Akira ransomware group has emerged as a tenacious adversary and grabbed widespread notice quickly. The group appeared in March 2023 and became the 4th most active group in August, demanding millions of dollars in ransom from victims.
Implementing multifactor authentication can make the difference between a devastating cyberattack and an insignificant breach attempt.
Organizations must monitor risks and build adequate defenses, such as keeping software and systems updated, auditing privileged accounts, and employing network segmentation.
Akira is a Ransomware-as-a-Service (RaaS) group that started operations in March 2023. Since its discovery, the group has claimed over 60 victims, which have typically ranged in the small- to medium-size business scale.
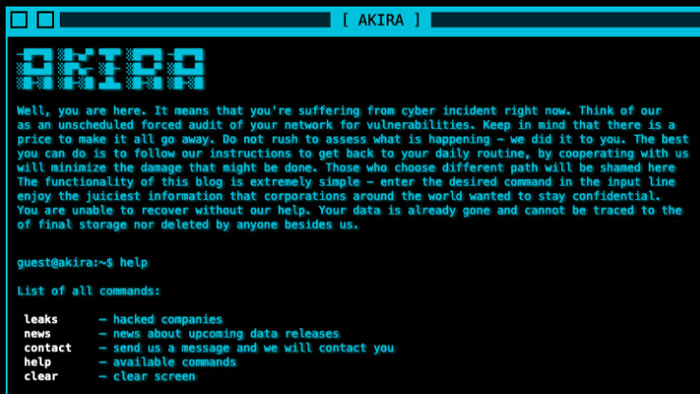
Akira has garnered attention for a couple of reasons, such as their retro 1980s-themed website (see figure below) and the considerable demands for ransom payments ranging from $200,000 to $4 mn.
Akira has been observed obtaining initial malware delivery through several methods, such as leveraging compromised credentials and exploiting weaknesses in virtual private networks (VPN), typically where multi-factor authentication (MFA) is not being used. Like many ransomware groups, they employed the double-extortion technique against their victims by exfiltrating data prior to encryption.
It is also believed that the group may contain some affiliation with Conti due to observed overlap in their code and cryptocurrency wallets. The group has targeted multiple sectors, including finance, real estate, manufacturing, and healthcare.

 by
by 


