The cyber warfare in Ukraine, a clash of titans in terms of cyber security, has considerable implications for the cyber threat landscape. For the purposes of this piece, XCyber analytics have broken down our analysis into three key sections: a review of Ukraine war-linked cyber activity to date, read-across implications for future conflicts and the threat posed by other hostile countries.
Cyber activity in the conflict zone

According to Global Cyber Insurance Market Review, whilst the high-impact cyber attacks widely predicted in the lead up to the war in Ukraine have not (yet) occurred, the last 18 months have stood out for the marked increase in wiper malware attacks.
Russian cyber activity aimed at the West has seen no discernible increase, with the exception of countries in close vicinity to the conflict zone, most notably Poland.
Concern that untargeted cyber attacks could spread out of the conflict zone, or even trigger a NATO response if deemed an act of war, has contained Russia’s cyber ambitions so far.
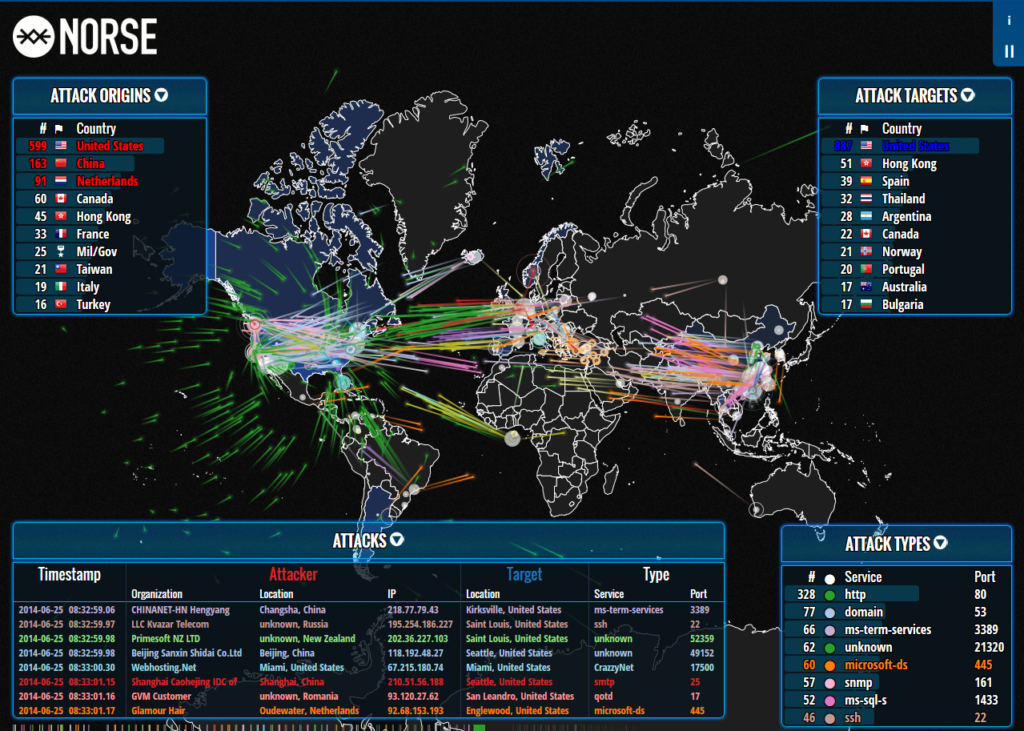
For all the focus on state-sponsored attacks in the current geopolitical climate, lower level activity carried out by criminal gangs still poses the biggest threat to Western businesses.
Of the USD 10 bn cyber-related losses reported by the FBI in the U.S. last year, the majority were carried out by criminal groups, not state-sponsored actors.
The FBI report details more than 800,000 cyber crime-related complaints. With Russian actors less able to shield behind a veneer of plausible deniability, the response threshold appears to be lower. In the past five years, the IC3 received a total of 3.26 million complaints for $27.6 billion in losses.
TOP 5 cyber crime types
- Phishing: 300,497 complaints
- Personal Data Breach: 58,859 complaints
- Non-Payment / Non-Delivery: 51,679 complaints.
- Extortion: 39,416 complaints.
- Tech Support: 32,538 complaints.
The FBI also outlined various threat overviews in their report. These overviews included business email compromise (BEC), investment scams, ransomware and call center fraud.
TOP 5 sectors affected by ransomware
- Healthcare and Public Health
- Critical manufacturing
- Government facilities
- Information Technology
- Financial services.
For example, the wiper malware discovered in Ukraine over the last 18 months has had its ability to self-replicate set very low when compared to the Russian-linked NotPetya ransomware in 2017, which started in Ukraine and then wreaked havoc when it spread across the globe.
It is also possible that Russia is focussing its outward cyber efforts on espionage, both to prepare for future attacks and gather intelligence on other countries’ responses to the war.
Pro-Ukraine cyber activity has mostly focused on the release of confidential information and other sensitive material, although hackers based in other former Soviet territories have recently lifted an informal embargo on attacking Russian-speaking companies in protest against Russian aggression.
Read-across implications for future conflicts
How cyber is deployed in any war depends heavily on the warring factions involved but developments in Ukraine may offer some insights for future conflicts where at least one of the state actors has advanced cyber capabilities, such as China, Israel or the U.S.
According to Cyber Security Top Trends, the blending of military and cyber goals is one such area. By focussing some of its conventional warfare efforts into capturing physical cyber infrastructure, such as network cables and data centres, Russia has set the dominance of Ukrainian cyberspace as a clear military goal, something confirmed by the recent Vulkan leaks (the unauthorised disclosure of documents relating to Russian IT contractor NTC Vulkan).
There is also precedent for governments experiencing stringent economic sanctions to shield criminal actors and encourage cybercrime to boost their own economies.
Other disclosures from the Vulkan leaks have revealed the (long suspected) role private Russian companies play in causing cyber disruption or carrying out digital espionage at the behest of the state.

Russian cyber activity has undoubtedly been consolidated further during the war, raising the potential for the state to carry out strategic attacks on Western targets, disguised behind the actions of criminal gangs (further complicating the attribution issue).
Indeed, Western organisations that have offered support to Kyiv appear to have been targeted specifically, with U.S. officials claiming the intent of the attacks was to disrupt supply chains and logistics important to Ukraine (see What are the Most Common Types of Cyberattacks?).
Such strategies may offer a glimpse into how a conflict between China and Taiwan could progress, with China looking to replicate some of Russia’s cyber efforts were a conflict to occur.
The West is looking to strengthen existing partnerships in response to the threat. As an example, U.S. Congress has proposed new bipartisan legislation under the Taiwan Cybersecurity Resiliency Act to bolster cyber security and collaboration.
How cyber is deployed in other conflict zones?
How cyber is deployed in other conflict zones will differ depending on the circumstances. Despite Russian involvement in several conflicts in Africa in the form of Wagner group mercenaries, limited cyber attacks have been recorded here.
Russia’s co-ordinated disinformation campaigns may nevertheless be paying dividends: a recent European Union report drew a link between Russia’s information operations in the global south (i.e. Africa, Latin America and Southeast Asia) and the limited number of countries in the region that have joined the sanctions regime imposed by the West.
Cyber threats from other hostile nations

Geopolitics and cyber security are inextricably linked, and whilst attention is focused on Ukraine, it is important to remember that Russia is not the West’s only cyber adversary. China, Iran, North Korea and Venezuela are also hostile to Western interests and are actively seeking to disrupt, exploit and influence to further their goals.
China generally focuses its cyber activity on espionage, both for strategic geopolitical gains and the theft of intellectual property to boost its domestic industries.
In 2021, the Chinese government passed a law that made the reporting of ‘zero-day’ vulnerabilities to authorities before public release compulsory, which appears to have significantly boosted China’s offensive cyber capabilities.
Iran has pursued a more aggressive cyber policy since President Ibrahim Raisi assumed power, as demonstrated by the hacking of the Albanian government in 2022 (which led Albania to consider invoking NATO’s Article 5 collective defence clause).
The war in Ukraine has created a complex web of risks and geopolitical alliances, with national strategic interests being temporarily put aside to shape direction at the transnational level.
The best demonstration of this is China playing both the West and Russia, according to its best outcome. The blocs being formed in the physical world are being replicated in the cyber word. Iran is supplying Russia with drones to use in Ukraine in exchange for cyber surveillance technology.
Any attempt to collaborate further and form a tripartite group would likely trigger a response from the West, where friendly countries do often co-ordinate in cyberspace.
Russia, China and Iran all have offensive cyber capabilities and each has signed co-operative agreements around cyber security.
There is also the danger of false flag attribution, particularly where cybercriminal groups engage in activity that has an impact on defence companies, national utilities or infrastructure. These could be classed as an act of war and escalate responses accordingly.
…………………….
AUTHOR: Milo Wilson – Lead Intelligence Analyst XCyber








