Cyber warfare and the attendant risk of systemic losses have long cast a shadow over the cyber insurance market. The issue has become even more pressing since war broke out in Ukraine, according to Howden’s report.
Systemic cyber exposures present challenges for an insurance market built on underwriting mostly geographically contained and uncorrelated (physical) risks, and being guided in the process by historical data to help manage aggregations, estimate potential losses and price policies.
Cyberattacks from Russia could be set to cause more disputes between businesses and insurers following the Zurich-Mondelez case.
9% of SMEs that purchased cyber insurance said the Russia-Ukraine War was a key trigger for their purchase
Nearly one in 10 SMEs that bought cyber insurance did so as a precaution against the Russia-Ukraine war.

While it ranked behind several other key factors, businesses that cited this factor will certainly expect to be paid out if they are victims of a cyberattack for this reason (see Top Cybercrime Predictions for 2024).
The leading factors were increased working from home during the pandemic (27%) and media reports about cyberattacks (26%).
Spectre of systemic cyber risk
Recorded activity against government and IT entities was higher than all other sectors combined during this timeframe, and a number of countries close to Russia’s border, the eastern flank of NATO especially, were targeted heavily.
Sectors and countries outside of Ukraine targeted by Russian threat actors since invasion
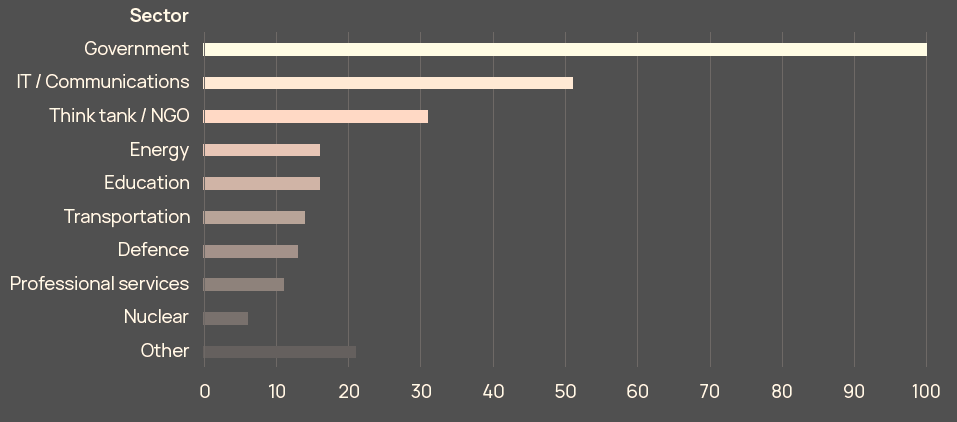
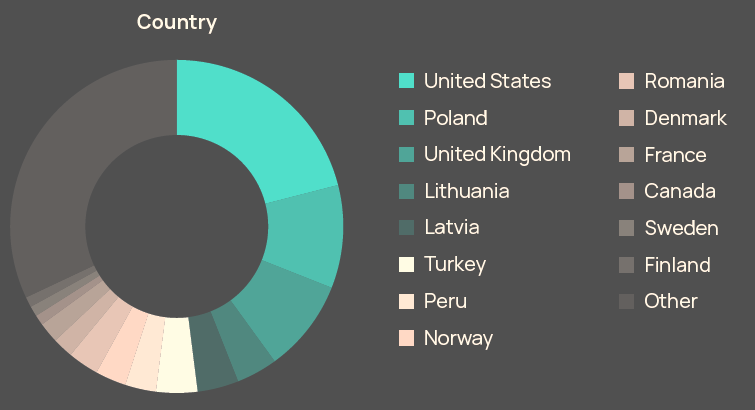
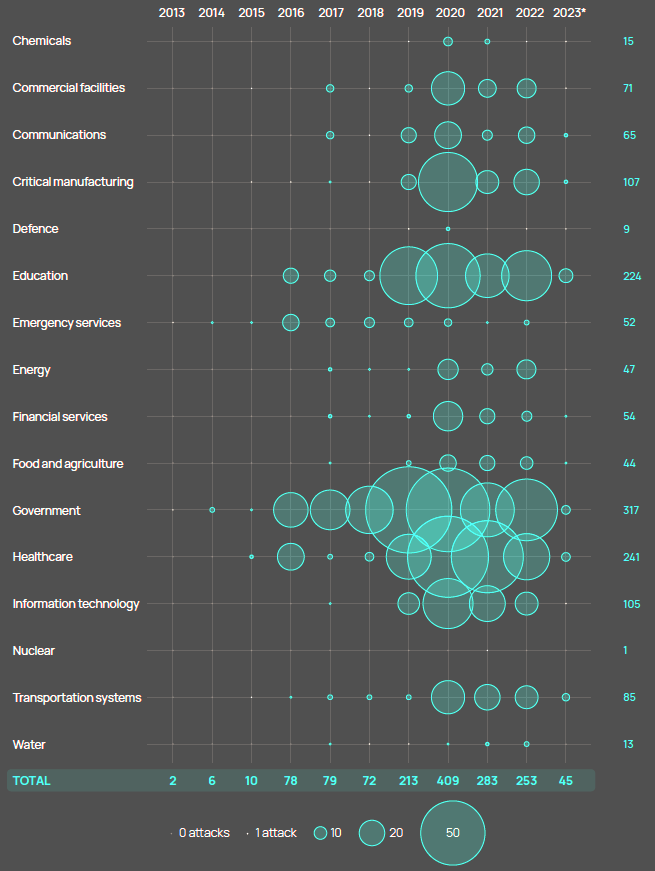
Much of this activity has been relatively low-level, ranging from reconnaissance to data exfiltration. The risk of contagion is likely to have contributed to the reduction in the number of ransomware attacks that targeted critical infrastructure last year, even if levels remained comparatively high (see New SEC Cyberattack Rule Raises Insurance Claims & Risks).
Although spillover concerns appear to have contained Russian ambitions up to this point, the risk of more destructive attacks remains elevated in such a volatile geopolitical environment.
Western governments continue to warn of the threat to critical infrastructure from state-affiliated threat actors who have already shown the intent and capacity to launch attacks in more tranquil times.
Staying one step ahead of attackers not only makes organisations more resilient to financially motivated cyber attacks, but it also means that they are better prepared to navigate a highly volatile geopolitical climate that carries considerable cyber risks and the potential for large-scale events.
Number of ransomware attacks on critical infrastructure worldwide
Cyberwarfare has provided just a handful of notable skirmishes in the Russia-Ukraine War. But fears linger that the scale and frequency of digital attacks on financial, industrial, and state targets in Ukraine, and among its allies, could escalate.
Realization is changing the dynamic of cyber risk management, pushing damage limitation to the forefront and, as a result, turning the spotlight on attack detection.
Warning cyber shots
Business interruption is one of the more dominant exposures associated with large-scale cyber attacks, and COVID-19 offered a glimpse into how borderless and non-physical threats have the potential to see losses spiral quickly, according to 10 Most Important Global Business Risks for 2023-2024.
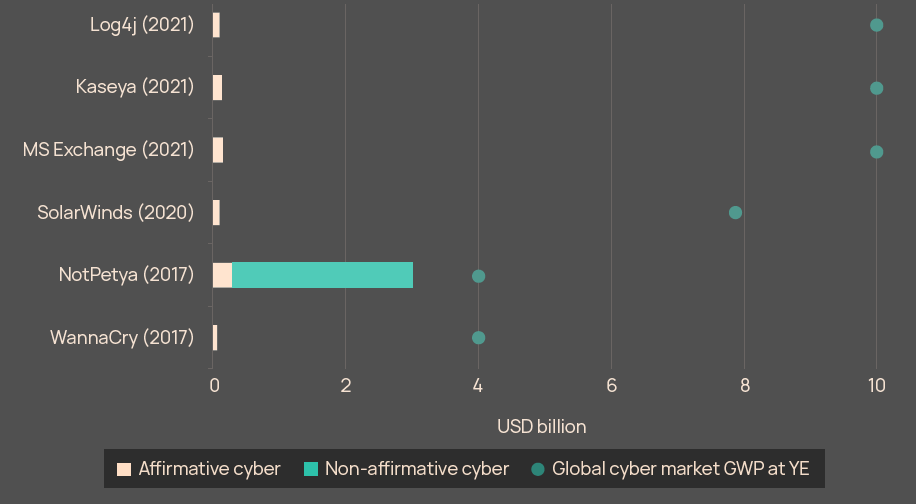
Cyber incidents, including WannaCry, NotPetya, SolarWinds, Microsoft Exchange, Colonial Pipeline, Kaseya and Log4j, highlighted the potential for systemic losses, even if the quantum ultimately ended up being manageable for the insurance market.
The recent MOVEit hack is another reminder of how companies need to manage supply chain risk, even if losses from this particular incident are unknown at this stage.
NotPetya remains the biggest individual cyber insured loss so far. It is important to point out here that approximately 10% (or USD 300 million) of the NotPetya loss was absorbed by dedicated cyber policies, with a near 100% payment record.

Recent, high profile claims litigation around NotPetya has been centred on all-risk property policies, and not standalone cyber.
Buyers will also benefit from further innovation, increased competition and higher limits (or increased risk appetite) as the market scales up.
The growth potential is huge: gross written premium (GWP) has more than doubled in the five years since NotPetya and could reach USD 50 bn by 2030.
The ability of the cyber market to absorb economic losses of the quantum often associated with large-scale events will grow over time as it approaches the scale of other major P&C insurance lines of business and pricing is sustained at levels commensurate with risks.
Insured loss for high profile cyber events vs GWP for global cyber market
This is of course not to say that the threat of aggregated losses is exaggerated. A large-scale event that resulted in a widespread cloud outage, for example, clearly poses a serious risk to the market (as the Q&A overleaf with cloud downtime insurer Parametrix indicates), although this is true of any tail event in other lines of business.
Cyber insurance prices
Cyber insurance prices stabilizing in the second half of 2022 and the first half of 2023 has resulted in an improvement for those clients renewing their cyber cover, and really good news in terms of being able to bring new buyers in and grow the market.
For existing customers, the rate increases and coverage restrictions that insurers were imposing when the hard market was in full swing wasn’t sustainable in terms of clients continuing to see the value of the cover. Some things had to change there, which fortunately they have (see about Future of Global Cyber Insurance Market).
Prices were soaring by 150% heading into 2022 but are now ticking up by 10% to 15% on average, according to Marsh. In some cases, reductions ranging from 10% to 25% are being seen. It’s stabilizing to the point where clients can actually budget and plan for the cost of it.
Pricing has also become more predictable. Sudden price changes two weeks before renewal were not unheard of in the past, but now, insurers can have formal discussions three-to-six months out again.
……………….
AUTHORS: Julian Alovisi – Head of Research Howden, Shay Simkin – Global Head of Cyber Howden, Sarah Neild – Associate Director Howden








