Given cyber crime incidents are now estimated to cost the world economy in excess of $1trn a year – around 1% of global GDP – it is no surprise that cyber risk regularly ranks as a top customer concern in the Allianz Risk Barometer, annual survey identifying the top business risks around the world.
Indeed, AGCS’ own insurance industry claims analysis shows that external attacks are responsible for more than 80% of the value of the 3,000 cyber‑related claims we have been involved with over the past five years around the globe.
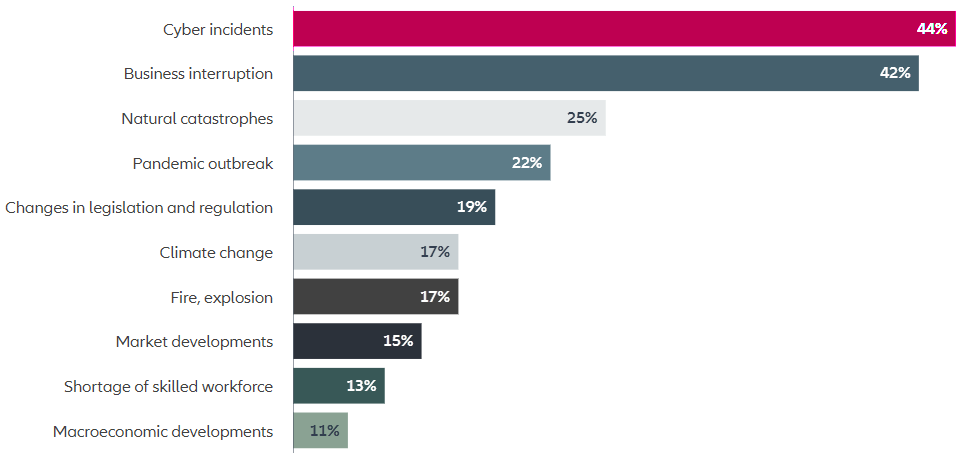
The most important global business risks for 2022
Report highlights some of the main cyber risk trends we see from an underwriting, risk consulting and claims perspective, such as the growing cost of ransomware attacks – which has been the major loss driver in recent years, the targeting of more smaller‑sized companies by hackers, the increasing frequency and sophistication of business email compromise attacks in the ‘Zoom and deep fake era’, as well as the impact of wider geopolitical tensions.
Analysis shows that business interruption is the main cost driver in more than 50% of all cyber claims we participate in, and the report also highlights some of the major exposures that can result in large loss activity for companies.
Of course, almost any cyber incident can also lead to litigation or demands for compensation from affected customers, suppliers and data breach victims, and elsewhere we look at the continuing evolution of third‑party liability exposures, and how cyber security is increasingly seen as an environmental, social, and governance (ESG) issue (see Ransomware Attacks & Cyber Insurance). Insurer also examine how a talent shortage is hindering efforts to improve cyber security.

Experience shows a number of companies still need to improve their frequency of IT security training, cyber incident response plans and cyber security governance. Incident response is critical as the cost of a claim quickly escalates once business interruption kicks in.
It is clear that organizations with good cyber maturity are better equipped to deal with incidents. It is not typical for us to see companies with strong cyber maturity and security mechanisms suffer a high frequency of ‘successful’ attacks. Even where they are attacked, losses are usually less severe.
In response to the challenging loss environment of recent years, the insurance industry is more diligently assessing clients’ cyber risk profiles and clarifying coverage areas in a bid to incentivize companies to improve cyber security and risk management controls.
The good news is that we are now seeing a very different conversation on the quality of cyber risk than we were a few years ago and are therefore gaining much better insights as the cyber insurance market matures. Insurers have a role that goes beyond pure risk transfer, helping clients adapt to the changing risk landscape and raising their protection levels. The more we can partner with our clients the more losses will hopefully reduce in future.
Ransomware threat continues to help drive elevated cyber claims activity
In recent years AGCS has experienced elevated levels of cyber insurance claims, driven in part by the growth of the cyber insurance market, but also by an overall rise in incidents, including notifications of ransomware attacks, which are among the biggest drivers of cyber insurance losses.
During 2020 and 2021, AGCS received more than 1,000 cyber-related claims per year overall and while claims activity has stabilized, driven by a more diligent underwriting approach and better risk dialogue with companies, 2022 has the potential to be another year of high claims frequency, as cyber claims historically have occurred predominantly in the third and fourth quarters of the year.
Despite the efforts of law enforcement agencies, the frequency of ransomware attacks remains high, as does related claims activity. Ransomware attacks hit a record 623 million in 2021, double the number in 2020 and a 232% increase since 2019.
Despite a 23% reduction in frequency at the start of this year, the number of ransomware attacks globally in the first half of 2022 still exceeded full-year totals of 2017, 2018 and 2019, according to SonicWall’s Cyber Threat Report, while Europe actually recorded a 63% surge in ransomware attacks in the first half of 2022.
Meanwhile, ransomware is forecast to cause $30bn in damages to global organizations by 2023, remaining the top cyber threat to enterprises as well as governments, according to cyber protection industry estimates.
There is no denying that cyber extortion, and ransomware, has become big business. Ransomware-as-a-service (RaaS), which gives cyber criminals access to ransomware tools and support services, has lowered the barriers to entry and enabled criminals to scale up their efforts and ramp up their attacks.

With average ransom demands in 2021 in the millions and RaaS kits costing as little as $40 per month, cyber criminals can make huge returns with little investment or technical expertise from ransomware attacks.
On a positive note, there are some signs, however, that risk management actions taken by insured companies are beginning to take effect, yet overall the frequency and severity of ransomware and cyber extortion claims for AGCS has increased significantly in recent years (see Ransomware Insurance and Cyber Risk Landscape).
The number of ransomware attacks overall remains high. It is not possible to stop every cyber-attack and there are still a large number of companies that need to improve their defenses. Awareness is increasing and there have been improvements in cyber security, but more than half of submissions from prospective clients still do not meet our checklist of required controls entirely.
Ransomware Protection – What Does Good IT Security Look Like?
- Ransomware identification
- Business continuity planning/incident response plan
- Anti‑phishing exercises and user awareness training
- Backups
- Endpoints
- Email, web, office documents security
- Segmentation
- Monitoring patching and vulnerability management policies
- Mergers and acquisitions
Rising severity: Double extortion is now the norm
The severity of ransomware claims continues to rise year-on-year as gangs employ increasingly sophisticated attack tools and extortion techniques.
The value of ransomware claims globally has increased significantly since 2019, accounting for well over 50% of all cyber claims costs that AGCS has been involved in together with other insurers over the past two years and remains a significant cost driver through 2022 to date. Business interruption, restoration costs and expert fees are the main loss drivers in a ransomware event.
The cost of ransomware attacks has increased as criminals have targeted larger companies, critical infrastructure and supply chains
Costs have also risenas criminals have honed their tactics and found ways to extort more money from their victims. Double or triple extortion, which can dramatically increase the cost of an attack, is now the norm.
In a traditional ransomware attack, criminals infiltrate a network and use malware to encrypt files, demanding a ransom in return for its restoration. A double extortion attack, however, also involves the theft of sensitive data, which is then used as leverage for extortion. By exfiltrating data, criminals can make ransom demands of companies even if they successfully restore data from backups.

Triple extortion goes one step further, with criminals making extortion demands of business partners, customers, or suppliers that may be affected by data stolen in the initial attack.
Double and triple extortion adds to the cost of a ransomware attack, as well as introducing an element of third-party liability. According to research by CipherTrace, double extortion ransomware attacks increased by almost 500% in 2021, while payments to ransomware gangs increased 42% in the first six months to $590m.
Ransomware severity is likely to remain a key threat for businesses, fueled by the growing sophistication of ransomware gangs and rising inflation, which is reflected in the increased cost of IT and cyber security specialists.
Ransom demandsare now tailor-made, with groups investing resources in establishing the ‘right’ amount and using expert negotiators to maximize their returns.
Ransomware attackers are becoming more ruthless. As the number of easy targets decreases with improvements in cyber security, they are looking to squeeze more and more profit from successful attacks. Gangs are using a wide range of harassment techniques to successfully extort money.
Ransomware costs – double extortion changes the rules and multiplies the cost
Potential costs from a ‘conventional’ ransomware attack (which encrypts the attacked company’s data without leaking it)
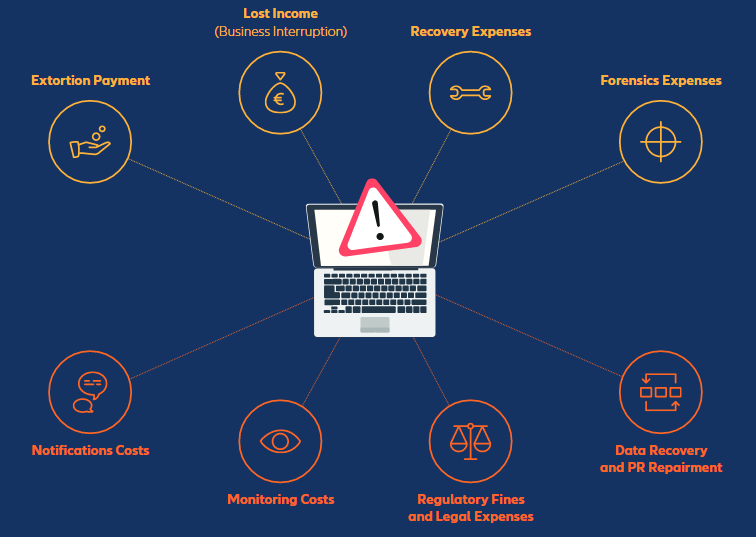
Potential additional costs from a ransomware attack which becomes a data breach event (stealing and then publishing the data)

Action on ransom payments on the horizon
High profile disruptive cyber-attacks, such as the 2021 Colonial Pipeline incident, has put ransomware on the political agenda, sparking a redoubling of law enforcement efforts. Attention has also turned to the payment of ransom demands, with new rules and potential bans on the horizon.
Ransom demands continue to rise. According to the Paloalto Ransomware Threat Report, ransom demands increased by 144% in 2021, while the average payments rose 78%.
Some 46% of companies paid ransoms in order to get data restored, according to Sophos. Manufacturing and utilities, which are particularly vulnerable to extortion, faced the highest ransom payments at an average of $2mn.
The US Treasury stated in 2020 that facilitating ransomware payments to sanctioned hackers may be illegal. EU member states can impose fines for paying ransoms under the Security of Network and Information Systems Directive (NIS Directive). Gartner predicted that by 2025, 30% of nation states will pass legislation that regulates ransomware payments, fines and negotiations, up from less than 1% in 2021.
Last year, the US Treasury Department warned organizations not to breach sanctions rules when paying ransoms. On July 29, 2022, New York State’s Department of Financial Services (NYDFS) issued new rules that would require financial services companies to report ransomware incidents and justify extortion payments.
The payment of ransom demands is a contentious topic. Critical service providers, such as hospitals or power companies, may have little option other than to pay a ransom demand in order to avoid crippling disruption. On the other hand, paying extortion demands may encourage further ransomware attacks. Sanction rules and terrorism regulations may also bar payment of ransoms to certain states, groups or individuals, including cyber groups.
Potential legal changes around ransom payments are unlikely to 100% solve the problem of ransomware, but they might help improve the maturity level of companies. Longer term, cyber criminalsare likely to consolidate and change tactics as ransomware attacks become less lucrative, and as easy targets are harder to find.
Tighter regulation on ransom payments could see cyber criminals shift their focus to other forms of attack, such as data theft or supply chain attacks, as well as more targeted attacks. If ransomware becomes less attractive, they will just look for other ways to monetize cyber-attacks.
Any impacted company should always inform and cooperate with the police or national investigation authorities.
Small and mid -sized companies an increasing sweet spot for hackers
All companies, across all sectors, are now exposed to ransomware attacks, although small and mid-sized companies are proving a more attractive target for cyber criminals as larger companies beef up their cyber security.
Cyber security, rather than sector focus, is now the key driver for cyber-attacks.
Themost attractive targets for cyber criminals traditionally have been large organizations, where they can get the most financial gain for reasonable effort. With these organizations investing heavily in security, the focus is gradually shifting to small and mid-sized firms.
The current real sweet spot is a mid-sized business with weak controls, risk management and cyber security in place. That is what cyber criminals like most.” Large companies are better positioned to mitigate the growing threat landscape than smaller companies, which often lack the resources to invest in cyber security and risk management.
Small to medium sized companies see their risks increasing with digitalization, but typically would not carry out impact analysis linked to cyber security and the value of the business.
Even larger companies can have vulnerabilities and blind spots.
In around 80% of AGCS cyber insurance claims, involving companies with an annual turnover in the triple digit millions, a significant flaw in the security of the insured led, or contributed, to the eventual loss.
No organization is 100% secure. We know of a recent case in Europe involving a large company with an excellent IT setup, but the attacker found an entry point and compromised their systems. It just takes a software vulnerability, a mistake by an employee, or a supplier with weak controls, and it can result in a large claim. Size and IT maturity will not protect you completely.
Business email compromise incidents rise in the ‘deep fake‘ era

Business email compromise (BEC) attacks have been on the rise, made easier by the growing availability of data, ‘deep fakes’ and the shift to remote working.
Targeting businesses large and small, BEC attacks can be impactful events, leading to financial loss or more damaging cyber-attacks.
BEC attacks can come in different flavors, but typically criminals will use phishing emails and social engineering to steal user credentials or trick an employee to make an unauthorized transfer of funds. BEC is attractive to criminals because they can achieve a big payoff for a relatively low investment of time and resources.
Between June 2016 and December 2021, BEC scams globally totaled $43bn, according to the FBI. There was a 65% spike in scams between July 2019 and December 2021 alone.
BEC attacks continue to grow more sophisticated and targeted, with criminals now using virtual meeting platforms to convince victims to transfer funds or to collect information on day-to-day operations. Increasingly, these attacks are supplemented by artificial intelligence (AI) enabled ‘deep fake’ audio or visuals that mimic senior executives on the telephone or during online meetings.
Last year, criminals used ‘deep fake’ audio to clone the voice of a company director in order to mislead a UAE bank employee into making a $35mn fraudulent transfer.
Data stolen during double extortion ransomware attacks, and then shared by criminals, is also driving the increase in BEC attacks.
Data leak sites offer searchable indexed data that enables cyber criminals to search for specific types of data, enhancing social engineering.
According to analysis of ransomware leak sites, Accenture found that an estimated 91% of ransomware victims incurred subsequent data disclosures.
Cyber criminals will continue to evolve their strategy for business email compromise. We continueto see claims in the US from business email compromise, despite increased awareness of cyber security and efforts to educate employees on phishing. If anything, the risk of attacks is growing. As more and more data is made available online the focus on social engineering and phishing has increased.
Geopolitical conflicts reshape threat landscape
The conflict in Ukraine, and wider geopolitical tensions, are reshaping the cyber threat landscape. As yet, the war between Russia and Ukraine has not led to a notable uptick in cyber insurance claims, however it does point to a potentially increased risk from nation states.

In addition to an increased risk of espionage, the war raises the risk for destructive cyber-attacks against companies with ties to Russia and Ukraine, as well as those in neighboring countries and allies.
The spill over of hostilities into cyber space, could see targeted attacks against Western critical infrastructure, supply chains and corporations with the aim of causing physical damage or disruption.
There is particular concern that companies could become collateral damage in any cyber conflict between Russia or Ukraine. In 2017, destructive ‘wiper ware’ linked to Russia – known as NotPetya – spread to companies around the world, causing an estimated $10bn in damage and business interruption. In addition to the risk of contagious malware, there are also concerns that the tools and techniques used by nation states during the conflict could filter down over time to cyber criminals.
The cyber threat landscape is constantly evolving. AGCS see new exposures and newthreats emerging.
Six months ago, few people were concerned about a hybrid cyber war, now we see that supporters of Ukraine and Russia have been the targets of cyber-attacks, while critical infrastructure around the world faces an elevated risk.
New forms of malicious attack are always to be expected.
Cyber war clauses will provide clarity of cover
Although acts of war are typically excluded from traditional insurance products, the invasion of Ukraine by Russia has accelerated the insurance market’s efforts to address the issue of war in cyber wordings and provide clarity of cover for customers.
Cyber risks pose systemic aggregations of exposure, particularly when it comes to war and conflict.
A cyber conflict between nations could cause unimaginable damage and disruption to thousands of companies, and potentially whole populations, if attacks target critical infrastructure like utilities, communications or payments systems.
Acts of war are understood in the context of physical damage and personal injury, but cyber war or conflicts are harder to define and difficult to attribute. The lines are increasingly blurred between the actions of nation states, terrorist groups and cyber criminals, while hostilities by nation state threat actors and their affiliates may be clandestine or amount to state-sponsored cyber-attacks that stop short of all-out war.
Such events are not without precedent.
The 2017 NotPetya contagious malware attack, which affected organizations in more than 60 countries, was attributed by US and UK security agencies to a Russia-backed hacking group.
Other high-profile attacks on private companies over the past few years that have been attributed to nation states include Russia’s 2020 SolarWinds hack, China’s 2021 Microsoft Exchange server breach and Iran’s 2021 attack on Boston’s Children’s Hospital, although in many cases attribution can be very difficult to prove.
The NotPetya attack sparked a debate on cyber war, prompting insurers and brokers to refine contract wordings.
A number of standard cyber war exclusions have been developed alongside claims processes to address the issue of coverage and also, in many instances, attribution. The Lloyd’s market recently announced it will exclude nation-state cyber-attacks in a bid to limit systemic risk and promote contract clarity.
As the cyber insurance market and product has matured, there is increasing focus on what a cyber war clause should look like.
Business interruption impact

Cyber business interruption is the number one digitalization risk of concern for many companies, and the biggest driver for cyber insurance losses overall. According to the Allianz Risk Barometer 2022, which asks more than 2,600 risk management experts around the world to identify the top worries for their businesses for the year ahead, cyber incidents and business interruption ranked highest.
Cyber was also the most feared cause of business interruption, reflecting the rise in ransomware attacks but also vulnerabilities in today’s increasingly interconnected world.
According to AGCS analysis of cyber-related insurance industry claims that it has been involved with over the past five years, business interruption is the main cost driver for 57% of claims globally and is a significant driver for the rising severity of claims in recent years.
Digitalization is driving deeper into companies, creating interfaces with customers, suppliers and employees. IT-outsourcing and cloud-usage is more widely and more extensively used.
While improving efficiency, these trends also change the threat landscape, creating vulnerabilities as well as increasing interconnectivity and aggregations of risk.
Cyber business interruption can be caused by a wide range of triggers, including a malicious cyber-attack, a software or hardware glitch, human error or a disruption to third party IT infrastructure or services, such as a power or cloud outage.
However, skyrocketing ransomware attacks in recent years have also thrust business interruption into the limelight – this is the largest loss driver for cyber insurance claims in Europe. Some 90% of cyber claims are first party, of which 80% are from ransomware. Business interruption losses can be as much as seven times extortion demands, based on claims AGCS has seen.
Notably, ransomware incidents have seen business interruption overtake third -party liability as the main source of loss in the US, where the cyber insurance market has historically been driven by data breaches.
If a ransomware attack or an IT outage is not rectified quickly, business interruption losses quickly mount. Manufacturing and industrial companies are particularly exposed to such business interruption losses as it can take weeks or even months to restore production levels from just a small outage. A cyber-BI incident at a major supplier could also ripple through the value chain, causing contingent business interruption (CBI) losses for customers and suppliers around the world.
Hackers zero in on vulnerable supply chains and M&A
Another worrying development is the deliberate targeting of supply chains, both traditional and digital. Such attacks are a particular concern for the insurance market, as a single cyber-attack can trigger losses at potentially thousands of companies around the globe.
Supply chain attacks have emerged as a significant risk in recent years, in part a reflection of the growing sophistication of ransomware attacks.
Cyber criminals are targeting supply chains, which are already under pressure since the pandemic, and where they may have additional leverage.
They are also targeting smaller critical suppliers within supply chains as well as suppliers that are in the process of a merger or acquisition, in order to gain access to the larger acquiring firm.
Last year, the Colonial Pipeline – which distributes fuel to the US East coast, was hit by a ransomware attack that shut down the pipeline. Hackers are also targeting software supply chains, inserting malware into legitimate software. The 2021 ransomware attack against cloud-based MSP platform Kaseya affected some 1,500 companies via malware inserted into a software update.
According to IBM, manufacturing overtook financial services to become the most attacked industry in 2021, as ransomware gangs used the threat of supply chain disruption to pressure firms into paying ransoms.
Almost half (47%) of attacks on manufacturing were due to unpatched vulnerabilities.

Manufacturers are particularly vulnerable to cyber-attacks through their supply chains, which can be complex and involve thousands of suppliers. While many large companies have taken measures to reduce the risk of ransomware attacks, cyber security maturity and transparency throughout the supply chain is still largely absent, while cyber risk management among small- to medium-sized companies is lagging.
Organizations need to be careful not to create gaps in cyber security in their supply chains or when outsourcing. The safe use of cloud services requires distinct security knowledge, which organizations need to build first. It is a common misconception thatthe outsourcing or cloud vendor will assume full responsibility.
Third-party liability
Cyber-related third-party liability exposures continue to evolve with technology and regulation creating new exposures.
Third party liability is becoming more relevant with advances in technology, as organizations and connected devices collect a growing volume of personal data, including information on health, behavior and biometrics.
At the same time, artificial intelligence (AI) and powerful analytics enable organizations to process data and make decisions or provide advice in real time, such as with chatbots and automated services.
Data breach and privacy regulations continue to expand, following the introduction of tough rules in Europe under the General Data Protection Regulation (GDPR), and more stringent regulations in locations and countries such as California, Brazil, China and India. In addition, a number of US states have passed biometric privacy laws, while the EU is developing a regulatory framework on AI.
Through 2023, government regulations requiring organizations to provide consumer privacy rights will cover five billion people worldwide, representing more than 70% of global GDP, and up on around three billion people in 2021, according to Gartner.
As technology evolves, it tends to be regulated on the backend as the drawbacks inherent in new advancements come to light, Stephens explains. For example: technological advancements and the move to online business models have altered the ease with which companies can gather, store and share consumer data.
Social media companies mined users’ data for years, often without their knowledge of what the data was ultimately being used for. As consumer privacy rights became an area of increased concern, regulators have responded with regulations.
Third party liability losses are also becoming more important for ransomware claims, where losses are typically driven by business interruption and restitution costs. The rise of double extortion ransomware attacks, where criminals steal and use personal data, can give rise to data breach claims and litigation.
……………………….
AUTHORS: Scott Sayce – Global Head of Cyber and Group Head of the Cyber Centre of Competence AGCS, Rishi Baviskar – Global Cyber Experts Leader, Risk Consulting, AGCS








