The world of today is one of increasing geopolitical and economic instability. This has many drivers, most prominently the war in Ukraine and simmering tensions between the US and China. With many facets of life going increasingly digital contemporaneously, the spectre of cyberattacks looms large. The resulting losses from a systemic cyber event could be very large, impacting companies, the broader economy and society at large.
So far there has not been such a systemic incident. Nevertheless, the cyber risk landscape is evolving fast, with ransomware incidents and cybersecurity worries from businesses and governments at an all time high.
McAfee estimates global monetary losses from cyber crime in 2020 at around USD 945 billion. Attacks have become more sophisticated.
Hackers now use “triple extortion” techniques, and ransomware-as-a-service has lowered entry barriers to rogue actors. Small and medium-sized enterprises (SME) with little defence capacity have become easy targets for cyber criminals, while digitalisation of industries including the healthcare and critical infrastructure sectors, has increased vulnerabilities across entire supply chains.

Before the NotPetya attack of 2017, cyber risks centred around data breaches and third-party liability. For re/insurers, the proliferation of data privacy regulations opens the door to litigation procedures and increases long-tail risk exposures.
In the last two years, first-party claims have become dominant, with ransomware incidents from organised crime shifting damages to core business. Firms, insurers and public authorities have redoubled risk management efforts, and industry associations and insurers have worked together to address the related issue of “silent cyber” by clarifying the scope of traditional policies.
Insurance plays a key role, providing not just for risk transfer but incentivising risk mitigation, supporting monitoring and aiding responses to cyberattacks.
But the cyber protection gap remains large, with premiums amounting to just a fraction of total losses from cyberattacks. Most firms are uninsured or significantly under-insured for cyber risks (see Embedding Cyber Risk in Risk Management).
In a recent survey, only 55% of businesses reported having cyber cover and less than one in five have cover limits above the median ransomware attaks demand. We estimate that the total claim arising from a cyber-incident targeting an SME is in relative terms three times more than for large corporations, with forensic costs typically ranging from USD 20 000 to USD 100 000 for a firm with turnover of less than USD 50 million.
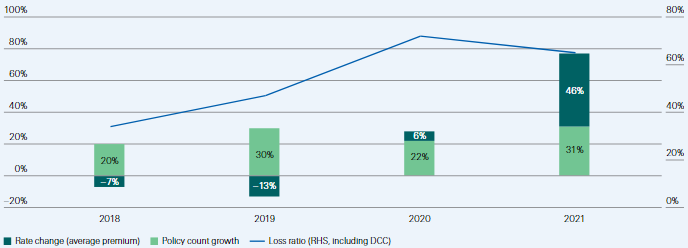
The surge in ransomware attacks drove loss ratios higher in 2020. Insurers responded by increasing prices, improving underwriting discipline, introducing sub-limits and coinsurance, clarifying terms and conditions, and excluding – or explicitly pricing for – cyber exposures in other property and liability policies. These actions had a degree of success: loss ratios plateaued in 2021.
The digital shift accelerated by COVID-19 has created new cyber vulnerabilities
Reported ransomeware incidents and their severity have skyrocketed in recent years, with monetary estimates of global 2020 cyberattack losses at around USD 945 billion. The types of attacks and targeted sectors have also evolved.
Cyber criminals have small and medium enterprises on their radar, particularly in the healthcare, professional and financial services sectors (see How to Reduce the Impact of Cybercrime?). Digitalisation of industries, including the healthcare and critical infrastructure sectors have increased cyber-vulnerabilities across entire supply chains.
Meanwhile, the cyber insurance market has been growing fast
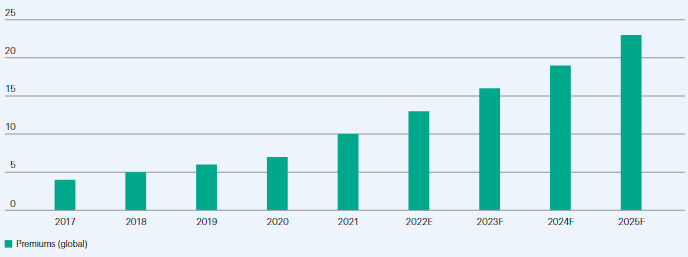
Risk management efforts and cyber insurance premiums have expanded in response to the surge in incidents, with USD 10 billion premiums written globally in 2021.
Cyber risks originally centred around data breaches and third-party liability, but ransomware attacks have shifted damages to the core business and first-party liabilities. We expect premiums to grow to USD 23 billion by 2025 but even so, the market remains small relative to a fast-evolving risk.
Cyber insurance profitability deteriorated as ransomware attacks skyrocketed and stabilised as underwriting actions took effect
Loss ratios for US standalone cyber insurance policies spiked in 2020 before improving slightly in 2021 as a result of price increases, stricter underwriting standards such as requirements for multi-factor authentication, and tighter terms and conditions including sub-limits and coinsurance. But they remain elevated, especially considering the necessary catastrophe load for a potentially systemic loss.
Undiversifiable aggregation risk and the fast-changing nature of cyber bring increased uncertainty, and a call for new solutions
These solutions include coordinated industry efforts to standardise data and policy languages. Improved modeling capacity (both scenario-driven and data analytics-based) and upgraded cyber skills would help address quantification shortcomings. Altogether, this would help reduce uncertainty, lay the foundation to attract new sources of capital and thereby activate a market for cyber insurance-linked securities (ILS).
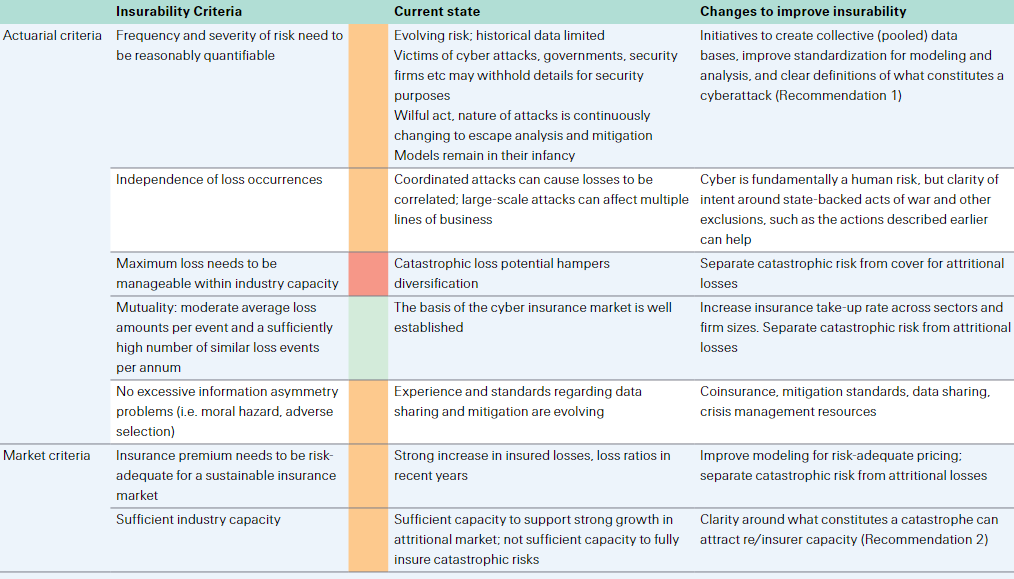
Cyber risk landscape
Cyber incidents: getting more severe and sophisticated
The digital shift accelerated by the pandemic is anticipated to change how society functions over the coming decades: the way we work, do business, consume, educate our children, manage and source energy, entertain and seek medical support. But as digitalisation proliferates, so too do exposures to cyber-threats.
The pace of technological change, the rising awareness of cyber risk and the adoption of cyber hygiene practices to keep data and networks secure, are not synchronised.
Rather, it seems as if a legacy of outdated security protocols, IT systems and regulatory frameworks are only slowly catching up with technological realities. This opens the door to rogue actors seeking to exploit digital vulnerabilities for financial, reputational or geopolitical gain.
The scope and frequency of cyberattacks are increasing, and today ransomware is seen as the predominant risk for businesses. In 2022, cyber incidents top Allianz’s risk barometer for the first time, ahead of business interruption and natural catastrophes risks.
Computer security firm McAfee estimated the total annual cost of cybercrime at USD 945 billion in 2020,2 two-thirds of which was attributable to intellectual property theft and financial crime, while the direct costs associated with the four most common types of cyber-incidents in the US quadrupled to an average of USD 100 000 per incident since 2016.
Looking at ransomware alone, NetDiligence finds that 70% of ransom attacks conducted since 2017 have occurred in the last two years, with severity at an all-time high in 2021 (average ransom of USD 750 000, more than twice the 2020 figure).
In a recent survey of the world’s top cyber leaders, 50% indicated that ransomware attacks on their organisation are among their greatest cyber risk concerns, followed by social-engineering attacks and malicious insider activity.
With the advance of technology, the sophistication of ransomware attacks has grown considerably. The emergence of cryptocurrencies has provided an easy, but hard-to-trace method of receiving payments from victims, while advances in artificial intelligence (AI) analytics is expanding both attack and defence capabilities.
Ransomware actors now employ up to three extortion techniques. They encrypt and extract a company’s data against two separate ransoms – the first to unblock the firm’s system and the second to not disclose the data (double extortion).
Hackers can then leverage the stolen data to extract a third ransom from its primary owner (triple extortion). Sometimes hackers continue their attack until the company has fixed its security protocols (re-extortions).
The types of financial loss associated with these attacks have also evolved. Whereas traditional risks confronting businesses were concentrated around third-party data protection and privacy liability, in recent years claims have been largely dominated by ransomware attacks and there has been a shift towards the insured core business.
Companies hit by a ransomware attack face several first-party loss elements such as the ransom itself, forensic and data restoration costs, and the business interruption (BI) suffered as a result of disruption to operations. Firms can also suffer reputational harm, undermining their relationship with customers and also their market capitalisation.
Description of selected malicious types of cyberattacks
| Types | Definition |
| Ransomware | Ransomware is a type of malicious software (“malware”) attack designed to block access to a computer system until a ransom is paid. This attack |
| takes the form of a network intrusion (theft of credentials, installation of backdoors and malware, lateral movement through the network, exfiltration of | |
| data, ransom demand). Hackers often spend months spying on a compromised network to plan an attack and maximize their profits. | |
| Malware | Malicious software which infects a computer and that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system. |
| Distributed | In a DDoS attack, hackers attempt to take down a target network by flooding it with traffic from multiple sources (including internet calls) to a point |
| Denial of Service | that the system freezes and cannot function properly. The goal is often to sabotage web properties, damage brand reputations or prompt financial loss |
| (DDoS) | by making a website or network resource inaccessible. |
| Phishing | Phishing attacks occur when hackers exploit peoples’ vulnerabilities by sending an email from a seemingly trusted source. By clicking on a link in the |
| email and entering a password, the victim allows the hackers to get into the system, access data and/or send emails on their behalf. The term “spear- | |
| phishing” refers to cases where hackers take the time to research one intended target and approach the victim with a personally relevant message | |
| that appears legitimate and is more difficult to identify. | |
| Social- | Social-engineering is a method hackers use to exploit a person’s trust in order to obtain money directly or obtain confidential information to enable a |
| engineering | subsequent crime. This risk is often executed by tricking employees of a company into transferring funds to a fraudulent scammer on the other end. |
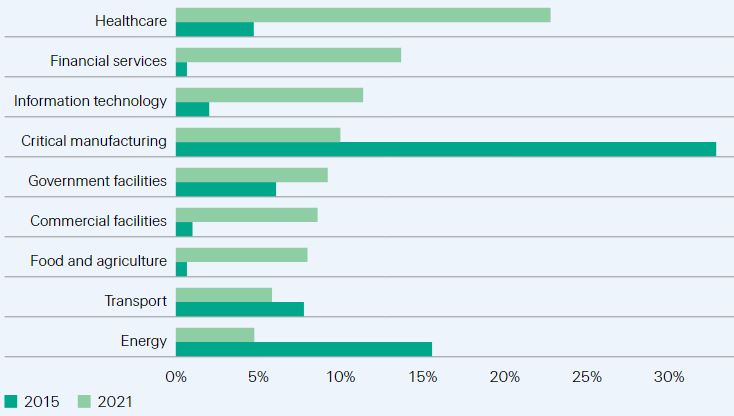
Cyber incidents by sector
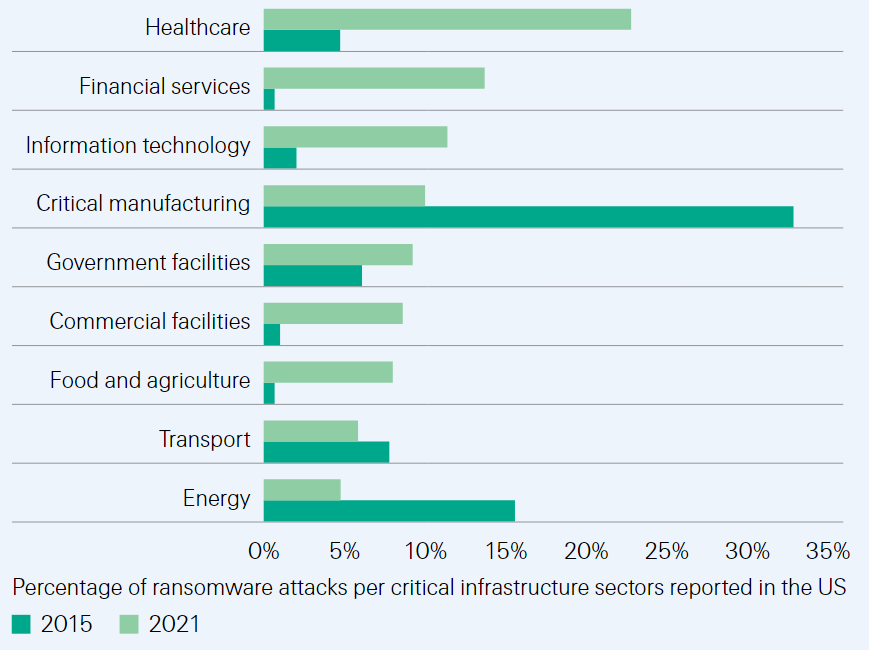
As cyber criminals deploy new tactics that make it harder for organisations to protect themselves, the exposure to attacks has grown considerably across every aspect of the economy. Comparison of ransomware incidents targeting critical infrastructure sectors in 2015 and 2021 show that the number of attacks has jumped 120%, while their distribution has shifted toward the healthcare, financial services and IT sectors.
Likewise, smaller entities are more exposed to cyber threats. In the aforementioned survey, 88% of respondents indicated that they are concerned about the cyber resilience of SME and the associated threat to supply chains.
Ransomware attacks in critical infrastructure sectors reported in the US (percentages)
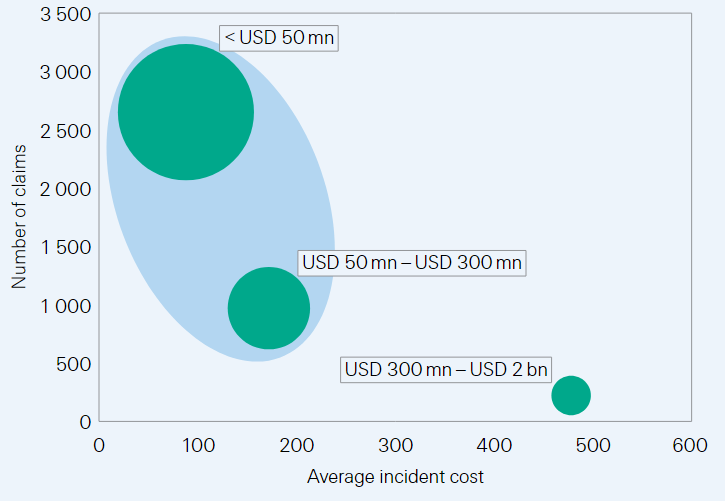
SME at risk: targets with limited resilience
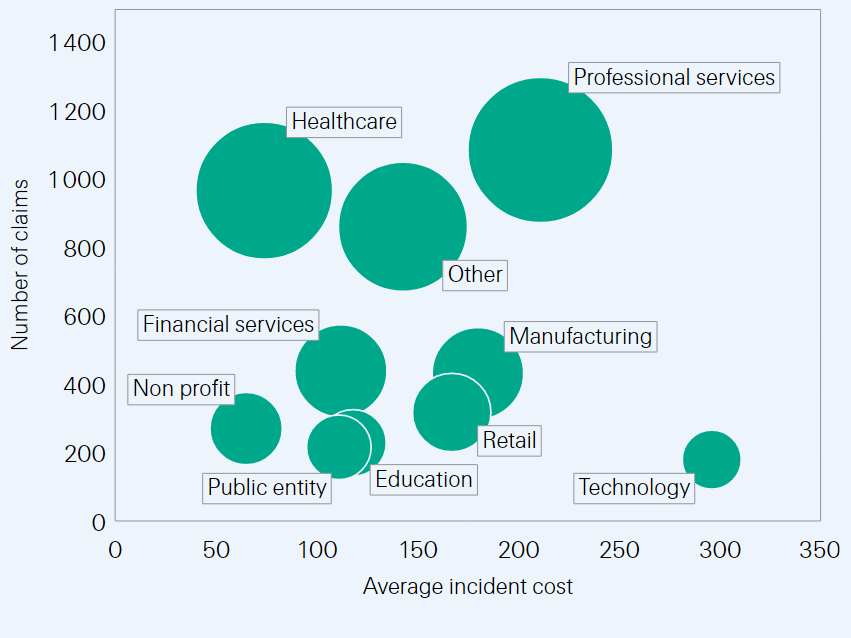
Data show that firms with turnover below USD 300 million in the US, UK and Canada made the highest number of cyber-related insurance claims between 2016 to 2020. The attacks reported affected many sectors including predominantly healthcare, professional and financial services, manufacturing and retail.
The proliferation of entry points brought on by digital practices has increased cyber risk exposures. Prior to the pandemic, cyber security protocols were primarily implemented on premises at corporate locations, a model that has been altered with the surge of remote work, cloud solutions and online retailing. The business ecosystem is likewise changing, with real time collaborations through MS Teams and Zoom, while emails remain an open door for phishing attacks.
SME: Number of cyber-related claims and average incident cost, per company turnover (2016–2020; USD thousands).
SME: Cyber-related claims and average incident costs, per sector (2016–2020; USD thousands)
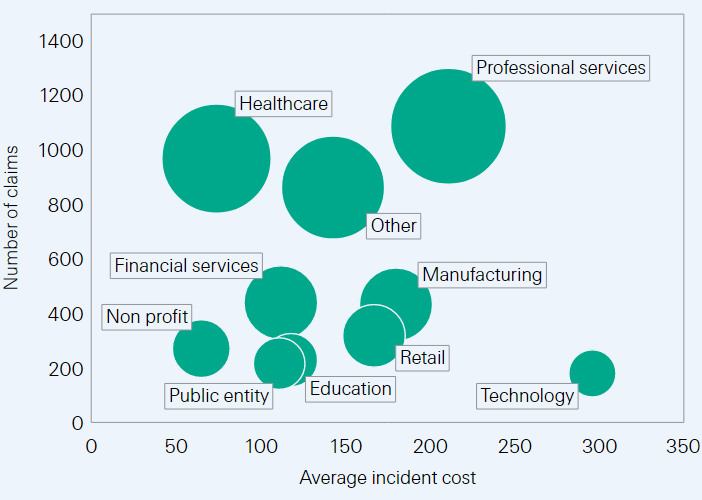
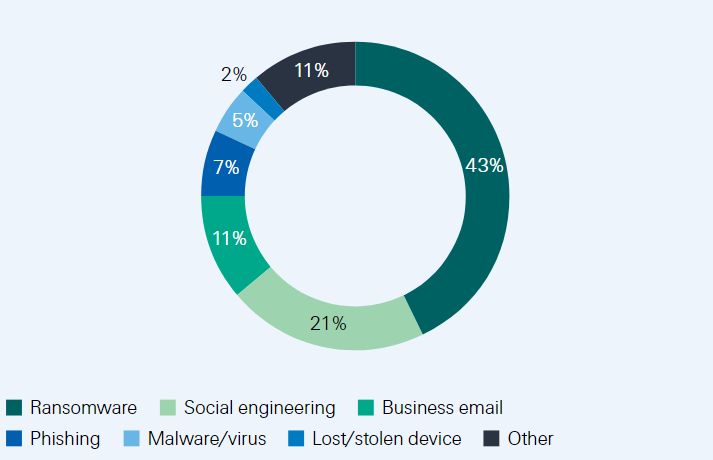
Smaller companies with lower cyber-defence capacities have become easy targets for cyber criminals and their loss absorption is more limited than at larger corporations. Analysis of claims data from 2016 to 2020 reveal that ransomware, social engineering and business emails tactics were employed in 3 out of 4 successful cyberattacks on SME, costing an average of USD 152 000.
Once attacked, the financial resilience of a cyber-entrant is lower than that of a cyber-incumbent. This is because a company without initial cyber capacity generally has little attack preparedness and incident response protocols in place. It will thus take longer for the threat to be detected and resolved and all the while, first-party losses rise. We assess that the total claims arising from a cyber incident suffered by a SME is in relative terms three times larger than that for bigger firms.
Types of cyber-related attacks affecting SME (%)
Average cost of cyberattacks affecting SME (USD thousands)
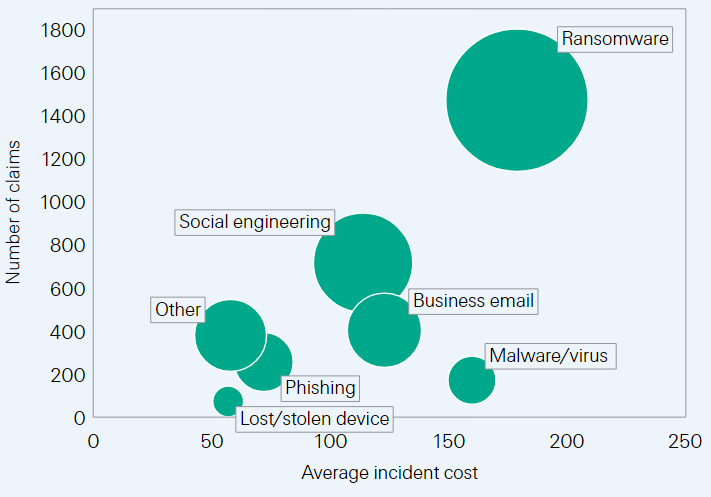
The financial, administrative and legal burden from a cyberattack targeting an SME is generally considerable. Forensic costs typically range from USD 20 000 to USD 100 000 for companies with turnover of less than USD 50 million, while initial ransom amounts can reach up to USD 25 000 in 75% of cases.
If customer data is compromised, the company needs to comply with the notification requirements applicable in the jurisdiction(s) where the customer resides. Court proceedings by customers may also lead to financial compensation obligations.
Meanwhile, the company incurs internal costs to get its operations back up and running, and to address the damages it has suffered from the attack (ie, restore systems and data, quantify BI losses, work with a public relations firm to communicate the breach and minimise reputation losses). Cyber policies typically cover most of these elements.
They often also offer rapid incident management services that provide step-by-step guidance and swift access to a network of specialised service providers along the incident management cycle to facilitate prompt and effective intervention.
Stepping-up cyber-security takes time and resources but delaying this process threatens SME’s operations. Estimates found that half of small firms go out of business within six months of a cyberattack.26 Cyber hygiene and digital capacity are the two main forces at play. First, digitalisation makes the risk landscape more complex, raising the cost of attaining the optimal level of cyber hygiene. In parallel, a company with lower initial cyber hygiene is likely to be less digitalised and therefore less competitive.
The resilience of a company with low and stagnant digital capacity is thus threatened by two factors:
- the loss of competitive advantage within a market environment that is going digital;
- the higher investment cost of building the optimal level of cyber hygiene.
Both variables impact profitability by lowering revenues and increasing costs. When the profit nears zero, an SME may ultimately exit the market. A cyberattack can accelerate this process. Here insurers can help to bridge the cyber-defence gap for smaller companies by raising risk awareness, establishing cybersecurity requirements and incentivising continuous monitoring/adjustments to risks.
Healthcare data: digital ecosystems on the radar of cyber criminals
Healthcare is undergoing a digital shift. IoT devices can monitor patients’ health, machine learning algorithms are bringing early-stage cancer detection to new levels, while wearable devices and Health & Wellness apps enable consumers to take an active role managing their health.
Likewise, insurers are showing growing interest in leveraging this new health ecosystem for preventive diagnostics, early interventions, and to best tailor coverage to policyholders’ needs. For instance, live data analysis possible through new wearable devices, can improve early detection of cardiovascular diseases.
The healthcare revolution is creating massive amounts of sensitive data. A study from Stanford University estimated that over 2300 exabytes of healthcare data would be produced yearly from 2020.
The interconnected nature of this data – centralised in healthcare centres and decentralised in external private devices or insurers’ databases – heightens the exposure of healthcare ecosystems to cyberattacks.
Data breach incidents among healthcare stakeholders are a concern on account of patient privacy, but also for the continuous provision of healthcare services should they be suspended by a ransom encryption.
A recent survey covering the US found that one in four cyber attacks over the previous 24 months resulted in increased mortality by delaying care. Intertwining the financial costs of privacy and mortality litigations raises the bar for insurers grappling with data protection coverages in the healthcare sector.
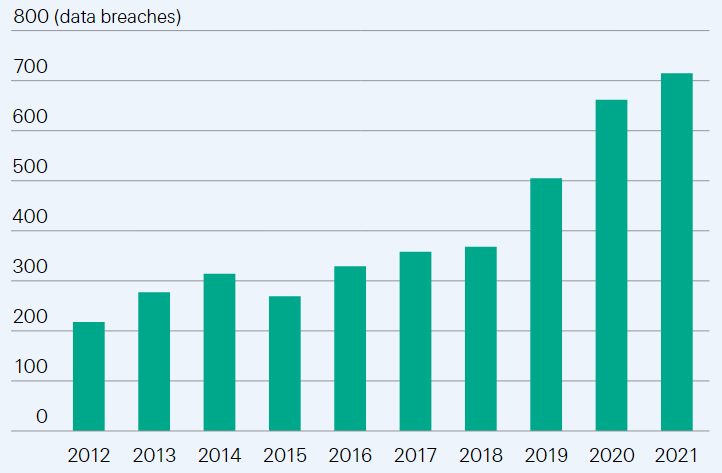
The number of data breach attacks in the healthcare sector is growing in line with other data-intense sectors with smaller structures emerging as the preferred targets of cyber criminals.
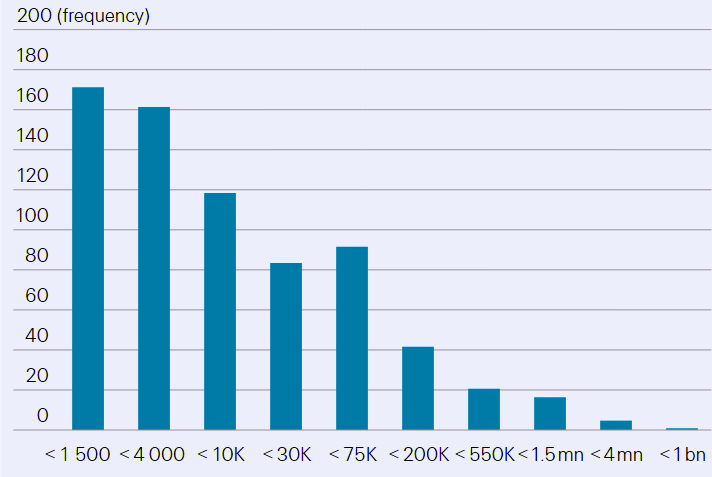
In the US, 2021 was a record year for data breaches reported by healthcare entities. As with SME generally, cyberattacks a greater impact on smaller healthcare entities with lower cyber capacities most. Last year, 75% of data breaches were reported by entities with under 30 000 affected individuals per attack. Conversely, the realisation of large data breaches was scarcer, with attacks affecting more than 1.5 million people accounting for less than 1% of the total.
US healthcare industry: number of reported data breaches
Individuals affected per data breach event (logarithmic scale)
Critical infrastructure: potential for systemic fallout
Major security breaches have highlighted the vulnerability of critical infrastructure to cyber threats, a risk that is gaining scrutiny among policymakers and chief executives around the world. Should a cyberattack discontinue the provision of clean water, energy or internet services for an extended period of time, the consequences on the broader economy could be disastrous. When Colonial Pipeline in the US was hit by a ransomware attack in 2021, the company stopped its gas supply operations for six consecutive days, impacting downstream customers and consumers.
Recent geopolitical turmoil increases the potential for a large-scale attack on critical infrastructure. A recent survey finds that infrastructure breakdowns due to a cyberattack is the top personal cybersecurity concerns of cyber leaders, with 42% saying so.
Throughout the years, critical infrastructure has become reliant on operational and information technologies (OT/IT) that make them vulnerable to cyber threats. From renewable energy generation to water management systems and energy distribution networks, critical infrastructure is composed and operated through networks of industrial control systems and enterprise information technology systems.
For instance, Singapore governs its water supply management and water quality system through AI analysis of real time data collected by IoT devices, themselves monitoring quality parameters and consumption patterns.
Further, the interconnected nature of critical infrastructure means the failure of one system is likely to impact others. With the digitalisation of operations and adoption of remote technologies, cyber targets have thus evolved beyond traditional IT systems, towards those OT used to manage entire industrial systems. These are all new entry points for rogue actors seeking to disrupt critical assets.
Supply chain vulnerabilities
Supply chains have multiple entry points for hackers. The interconnected nature of supply chain networks across digital and physical borders makes participating companies vulnerable to shocks that can propagate through the entire system. The more digitally integrated the network, the faster the propagation of the shock and the less clustered the impacts.
The NotPetya attack of 2017, during which hackers embedded malware in accounting software used by companies in Ukraine for tax reporting purposes, is one example of such a shockwave event.
It propagated horizontally by discontinuing the operations of infected companies and had vertical spill-over effects across multiple supply chains and borders.
It is estimated that affected downstream companies experienced a loss of USD 7.3 billion, a fourfold increase from the losses reported by the firms upstream hit directly. Losses were found to be higher among companies with an undiversified pool of suppliers, and infected suppliers were more likely to be cut out of the supply chain after an attack.
Data privacy regulations: increasing long tail risks for insurers
Europe has been a leader in establishing data privacy regulations, and many other regions are following. Since the General Data Protection Regulation (GDPR) came into force in 2018, not less than 60 countries have either enacted or considered enacting new data privacy laws, with many adopting similar concepts to the ones enshrined in the GDPR.
In Asia, last year saw the introduction of new privacy laws in Japan, Singapore and China. In the US, while there is no federal privacy law yet, California introduced a first state-based privacy legislation in 2018. Since then, Colorado and Virginia among others, have implemented their own data privacy and security legislations.
Stronger data privacy rights expose firms and insurers to consumer-led litigation and regulatory sanctions that can result in huge financial losses. New privacy and security laws provide additional rights for consumers and reinforce those already in place.
For instance, the California regime provides for statutory damages on a per-person basis and has seen increasing claims settlement values for state residents. And in Europe, reporting a security and/or privacy breach to regulators and consumers is mandatory.
Failure to do so, or to have the wrong security measures in place, can result in fines being levied under the GDPR, of up to 4% of a company’s global turnover or EUR 20 million, whichever is greater. The GDPR also rules that any person who has suffered material and non-material damages (ie, emotional distress) as a result of an infringement of the regulation has right to compensation for the damage suffered. Litigations in Europe post GDPR, either via individual lawsuits or EU-style class actions, show that consumers are now using this right to obtain compensation in cases of data/privacy breach.
Third-party claims are just one of several elements constituting a data-breach related loss. In addition, there can also be legal fees, crisis management costs (first party) and potential fines.
Breaches become even costlier when they involve many jurisdictions because of the international regulatory implications and potential lawsuits that may be filed by aggrieved parties in different countries.
Conclusion
The cyber risk landscape is rapidly evolving and, as cyberattacks have increased, so too has awareness of the risk and demand for cyber insurance solutions. However, most businesses and individuals are uninsured or significantly under-insured for cyber exposures, and cyber insurance premiums amount to just a fraction of total losses from cyberattacks.
Estimates put the cyber protection gap at 90%. This points to the large growth potential for the insurance market, but there is much work to do to ensure sufficient risk protection is available to make society more resilient to cyber risk.
And this effort will require collaboration between businesses, the insurance industry and government.
A first requirement is to improve data quality and modelling. Cyber risks are difficult to quantify due to a lack of standardised data and modelling constraints. Future risks are typically inferred based on backward-looking data, but this approach is of limited value in the rapidly changing environment of cyber risk.
Introducing cybersecurity standards will improve data in terms of breadth and transparency to allow meaningful risk insights and enable more accurate pricing and modelling.
Re/insurers must also invest in the cyber workforce to help strengthen the actuarial, technical and forensic skills needed for the underwriting and claims management cycles.
Meanwhile, the high degree of uncertainty regarding expected losses and the evolving nature of the risk challenges the insurability of peak and accumulation risks.
Second, re/insurers should update policy language for clarity and consistency. The relative youth of the cyber insurance market and complexity of the risk are reflected in a lack of standardisation around exclusion clauses and terms and conditions. Exposures to hard-to-insure systemic risk scenarios remain a barrier for industry capacity.
Stakeholders have taken steps to fix some of these issues, but factors such as attribution of cyber events remain a core problem. By clarifying the scope of coverage, as well as supporting risk analysis and mitigation efforts, contract clarity and consistency can lead to increased cyber capacity.
Finally, there is also need and scope for new types of public-private risk sharing mechanisms. Public and private sector collaboration is key to mitigating cyber threats to critical infrastructure.
A public-private partnership insurance scheme, where coverage of systemic risks is split between insurers and a government(s)-backed fund is one option to address part of the protection gap. Another would be to tap into the market for alternative capital, such as by developing a market for cyber-insurance-linked securities.
……………………
AUTHORS: Elena Jelmini Cellerini – Senior Claims & Key Case Expert Swiss Re, James Finucane – Senior Economist, Dr Thomas Holzheu – Head of the Swiss Re Institute for the Americas








