Companies that have strong cyber security hygiene are reducing the risk of being targeted by cybercriminals. Low barriers to entry afforded by the ‘as-a-service’ model have been a key facilitator of ransomware and malware activity in recent years, and a recently discovered ‘phishing-as-a-service’ programme, where victims are directed to authentic-looking decoy login webpages, is indicative of a constantly changing threat landscape.
According to Howden’s report, investment in cyber security is crucial in this environment. Staying one step ahead of attackers not only makes organisations more resilient to financially motivated cyber attacks, but it also means that they are better prepared to navigate a highly volatile geopolitical climate that carries considerable cyber risks and the potential for large-scale events.
Rise of Malware and Cyberattacks

According to Global Cyber Insurance Market Review, whilst the high-impact cyber attacks widely predicted in the lead up to the war in Ukraine have not (yet) occurred, the last 18 months have stood out for the marked increase in wiper malware attacks.
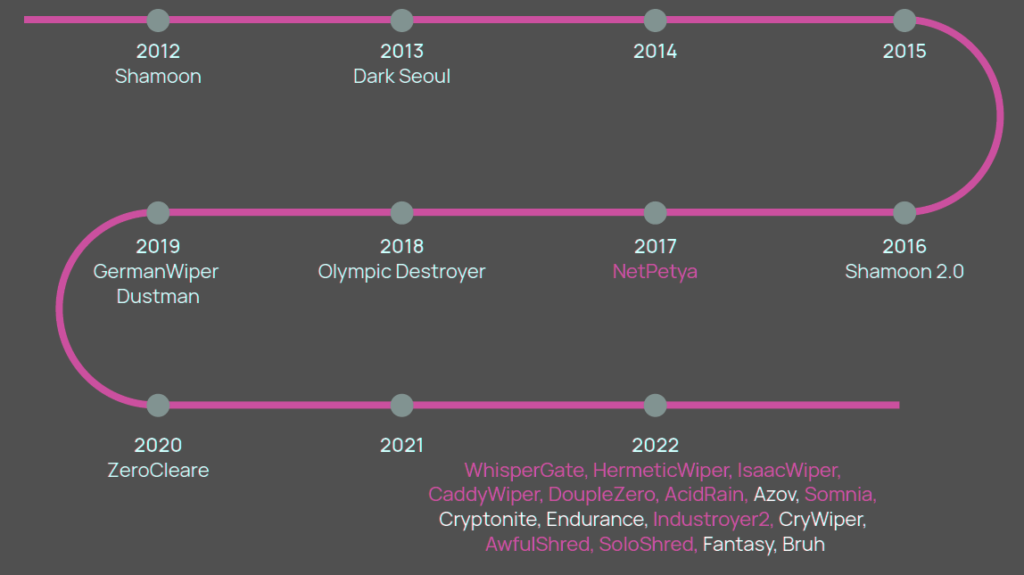
2022 saw the number of new wiper variants (designed to permanently erase files and immobilise computer systems) surge to unprecedented levels as Russia moved away from sophisticated operations designed to avoid detection, and towards quick and disruptive malware on specific strategic targets.
The rise of wipers into context shows that new variants detected last year exceeded the combined number recorded throughout the previous 10 years.
Recent history of notable wiper malware
This is indicative of shifting priorities during conflicts: cyber tactics and tools deemed most effective in supporting military goals (e.g. sabotage and / or disruption) are likely to take precedence in certain phases and bring a sudden and profound change to the threat landscape (see Insured Losses for Ukraine War & Ultimate Industry Loss Outlook)..
The realities of kinetic warfare go some way to explaining the diverging trajectory of malware and ransomware activity last year.
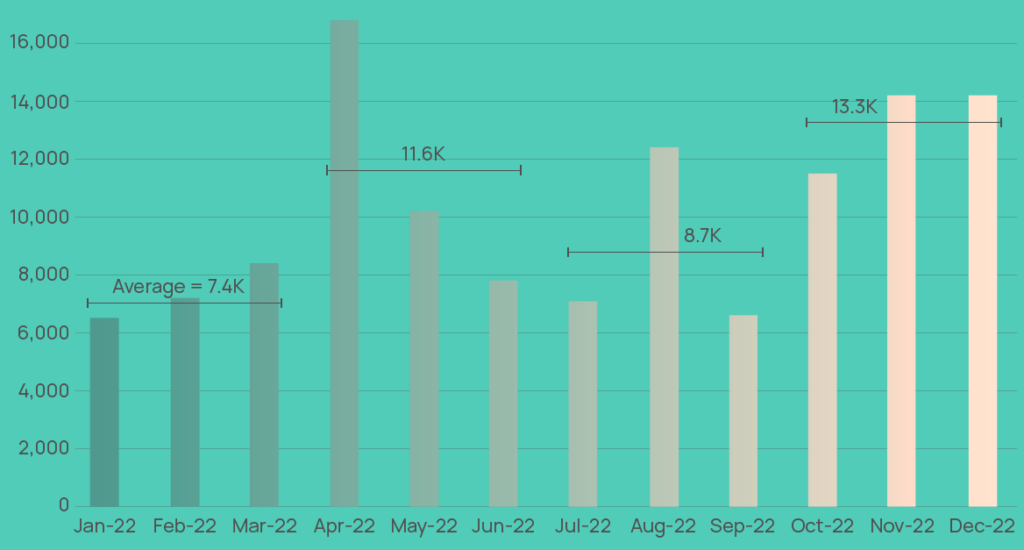
Wiper attacks, already at a high base in 1Q in the lead up to and following Russia’s invasion of Ukraine, accelerated through much of last year (frequency was up 53%).
Some variants first identified in Ukraine are now being used by commercial hackers for malicious operations on targets worldwide, although perceived difficulties in extracting financial gain from wipers are likely to see cybercriminals continue to pursue more lucrative methods of attacks, according to report Risks & Cyberattacs in Russia-Ukraine War.
Cyberwarfare has provided just a handful of notable skirmishes in the Russia-Ukraine War. But fears linger that the scale and frequency of digital attacks on financial, industrial, and state targets in Ukraine, and among its allies, could escalate.
Realization is changing the dynamic of cyber risk management, pushing damage limitation to the forefront and, as a result, turning the spotlight on attack detection.
Frequency of global wiper malware attacks
With nation states increasingly bolstering their cyber capabilities to seek political, economic and military advantage, and distinctions between state-orchestrated attacks and those carried out by affiliate groups becoming increasingly blurred, a big dose of complexity has been introduced into an already complicated cyber risk environment.
Insights provided by XCyber overleaf provide intelligence-led expertise into what can be expected in relation to the fallout from the Ukraine War.
Russia could use cyberattacks to target entities from countries that are allied with Ukraine as a means to gain an advantage in the conflict.
For the time being, cyberattacks have been less severe than we expected. Of the about 201 rating actions we have taken as a result of direct or indirect consequences of the war, none have been due to cyber-related issues.

According to Cyber Security Top Trends, a catastrophic cyber attack is the top scenario in 2023 resilience plans. Such an attack would surely put C-suite alliances to the test. Cybersecurity has become a more dynamic field, rapidly adjusting and shifting to keep apace with business inventiveness.
The 2023 PwC Insights is a survey of 3,522 business, technology, and security executives (CEOs, corporate directors, CFOs, CISOs, CIOs, and C-Suite officers)
Long-standing and familiar cyber threats remain on the horizon in 2023, highlighting the challenge facing cyber security leaders – just over a quarter (27%) of organisations say they expect business email compromise and ‘hack and leak’ attacks to significantly increase in 2023, and 24% say they expect ransomware attacks to significantly increase.
According to Cyber Security, Insurance & Cyber Business Intelligence Review, 33% of senior executives also say they expect attacks against cloud management interfaces to increase significantly in 2023, while 20% say they expect attacks on Industrial Internet of Things (IIoT) and operational technology (OT) to significantly increase in the next 12 months.
To better understand the role that detection plays in cyber risk management it helps to understand the nature of a typical cyberattack (see What are the Most Common Types of Cyberattacks?). Contrary to common perception, cyberattacks are not singular events.
Survey shows that the C-Suite is becoming more aware of how these complex cyber threats and the potentially damaging impact of them can pose a major risk to wider organisational resilience.
……………….
Edited by Oleg Parashchak – Editor-in-Chief at Beinsure, CEO Finance Media Holding








