Improvements in cyber security and business continuity are helping to combat encryption-based ransomware attacks, yet the cyber threat landscape is continually evolving. 2023 has seen a worrying resurgence in ransomware and extortion claims, resulting in an uptick in costly incidents, demonstrating that although progress is being made, the threat posed by ransomware shows little sign of abating, according to Allianz report about cyber security trends and future cyber insurance market.
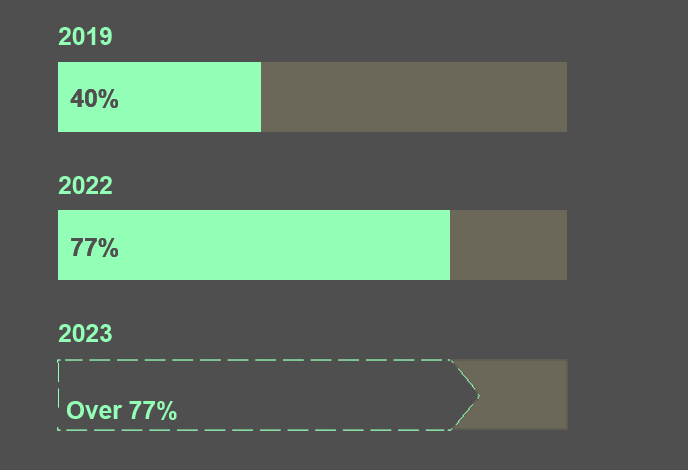
Allianz analysis of a number of large insurance cyber losses shows that the proportion of cases in which data is exfiltrated is increasing every year – from 40% of cases in 2019 to around 77% of cases in 2022, with 2023 on course to surpass last year’s total.
Hackers are increasingly targeting IT and physical supply chains, launching mass cyber-attacks and finding new ways to extort money from companies, large and small.
Most ransomware attacks now involve the theft of personal or sensitive commercial data for the purpose of extortion, adding further cost and complexity, as well as the increased potential for reputational damage and third-party liability.

Reports note that the number of ransomware victims surged by as much as 143% globally during the Q1 of 2023 with January and February seeing the highest number of hack and leak cases in three years.
Ransomware alone is projected to cost its victims approximately $265bn annually by 2031.
Companies that are routinely and properly managing their data, making sure it is stored appropriately and deleted when it is no longer required, will reduce the amount of data at risk.
Protecting an organization against intrusion remains a cat and mouse game, in which the cyber criminals have the advantage. Threat actors are now exploring ways to use artificial intelligence to automate and accelerate attacks, creating more effective AI-powered malware and phishing.

Combined with the explosion in connected mobile devices and 5G-enabled Internet of Things, the avenues for cyber-attacks look only likely to increase in the coming years.
Preventing a cyber-attack is therefore becoming harder, and the stakes higher. As a result, early detection and response capabilities are becoming ever more important.
An intrusion can quickly escalate, and once data is encrypted and / or stolen, the consequences and costs snowball – costs can be as much as, or even more than, 1,000 times higher than if an incident is not detected and contained early, Allianz analysis shows (see Cyber Security Top Trends & Cyber Attack Threats).
Resurgent ransomware targets data and supply chains
Ransomware remains the top cyber threat and the single largest cause of cyber insurance claims by some distance. Following a short hiatus in 2022, ransomware attack frequency has picked up again in 2023 as threat actors use data exfiltration and supply chain attacks to maximize their leverage.
In many ways, the last 12 months has been business as usual for ransomware gangs. They continue to evolve their tactics and business models in response to changes in cyber security and as they find new ways to extort money from businesses and public sector organizations.
According to research from cyber threat intelligence firm Black Kite, ransomware attacks surged in early 2023, with the number of victims in March nearly double that of last April and 1.6 times higher than the peak month in 2022. Akamai Technologies said the number of ransomware victims surged by 143% globally in the first quarter of 2023.
Meanwhile, January and February 2023 saw the highest number of ransomware hack and leak cases in the past three years, according to the NCC Group, which also noted that ransomware activity was up almost 50% year-on-year as of May 2023 (see Top 20 Cybercrime Predictions for 2024).
In future, ransomware alone is projected to cost its victims approximately $265bn annually by 2031, Cybersecurity Ventures predicts.
A surge in data exfiltration attacks from the likes of LockBit and Clop in 2023 has seen the number of attacks reach new levels, while according to cryptocurrency firm Chainalysis, ransomware victims paid demands of $449.1mn in the first six months of this year, already close to last year’s total of $500mn. At the current rate, 2023 could end up as the second biggest year for ransomware revenue after 2021 (see How to Make Cyber Security an Part of the Business Culture?).
This year has witnessed several large mass ransomware attacks as threat actors used exploits in software and weaknesses in IT supply chains to target multiple companies. At the same time, ransomware gangs continue to fine tune their business models in order to carry out more attacks, faster.

According to research from IBM X-Force, the average number of days taken to execute a ransomware attack has fallen from 60+ days in 2019 to less than four days in 2021.
In June, ransomware group Clop carried out a successful mass cyber-attack that is thought to have impacted thousands of companies, compromising the data of millions of individuals and businesses. Clop exploited a ‘zero-day’ vulnerability in MOVEit file transfer software to steal data from companies and public sector organizations, threatening to publish the data if they failed to pay a ransom demand.
According to Cybersecurity Spending Trends, the attack affected a number of large corporates, including energy giant Shell, British Airways, broadcaster the BBC, logistics firm DHL, insurer Genworth Financial, as well as the US Department of Health and Human Services and the US Department of Energy.
Genworth Financial alone reported that the personal information of nearly 2.5 million to 2.7 million of its customers was breached. Clop is now the second-largest ransomware group by number of victims.
RaaS groups responsible for majority of incidents
Ransomware-as-a-Service (RaaS) remains a key driver for the ongoing frequency of attacks. With access to RaaS kits and services, criminals lacking the skill to develop their own malware can launch ransomware attacks quickly and affordably.
With prices starting from $40 per month, RaaS kits enable cyber criminals to make millions from extortion demands with little financial investment.
Ransomware attacks against large companies typically originate from a relatively small number of groups.
For example, Allianz has handled several claims attributed to the likes of Black Basta, Clop and LockBit.
According to the US Cybersecurity and Infrastructure Security Agency, LockBit was the most deployed ransomware variant across the world in 2022, with more than 1,700 attacks since 2020 in the US alone, and approximately $91mn of ransoms paid.
Data exfiltration becomes the norm
Double and triple extortion – using a combination of encryption, data exfiltration and Distributed Denial of Service (DDoS) attacks to extort money – are not new, but they are now more prevalent, and potentially more impactful and costly for affected companies (see 5 Key Benefits of Ransomware Insurance).
Allianz analysis of a number of larger insurance industry cyber losses (>€1mn) between 2019 and the end of the first half of 2023 shows that the proportion of cases in which data is exfiltrated increases from year to year – from 40% of cases in 2019 to around 77% of cases in 2022, with 2023 on course to surpass 2022’s total.
Several factors are combining to make data exfiltration more attractive for threat actors. The scope and amount of personal information being collected is increasing, while privacy and data breach regulations are tightening globally.
At the same time, the trend towards outsourcing and remote access leads to more interfaces for threat actors to exploit.
The proportion of cases in which data is exfiltrated increases year on year
With potentially costly financial and reputational consequences, companies may feel under more pressure to pay ransoms where data has been stolen.
The same Allianz analysis of a number of larger insurance industry cyber losses (>€1mn) between 2019 and the end of the first half of 2023 also shows that the proportion of companies paying a ransom has also increased from year to year – from as little as 10% in 2019 to 54% in 2022.
Ransomware costs – double extortion changes the rules and cost
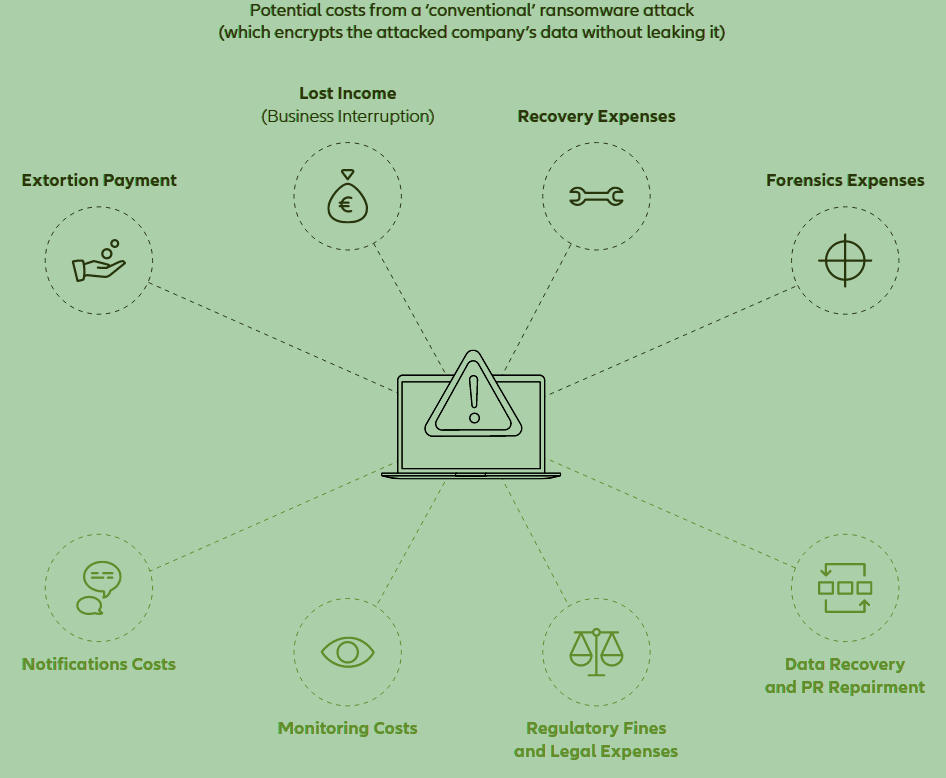
Indeed, there are very few cases where a company may believe that there is no other solution than paying the ransom to be able to re-access their systems or data. Any impacted company should always inform and cooperate with the police or national investigation authorities.
In the past, companies holding personal data and credit card information were targets of data breaches, but increasingly industrial and manufacturing companies that share ecosystems are falling victim to data exfiltration attacks.
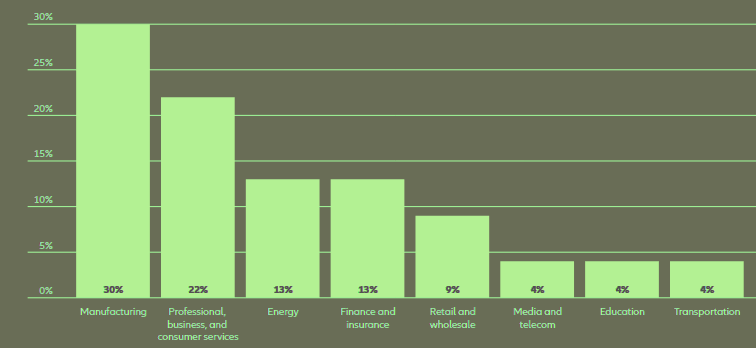
Manufacturing was the most targeted sector for ransomware cyber-attacks and the most extorted industry in 2022, according to IBM Security’s 2023 X-Force Threat Intelligence Index.
Top industries ransomware targeted
Threat actors target weak links in supply chains
Supply chain-enabled ransomware attacks are not new, but they have now become an established part of the ransomware playbook. Increasingly, threat actors are targeting companies in the IT supply chain, as well as companies that hold sensitive data in physical supply chains, in order to demand extortion payments from multiple companies.
Supply chain attacks first hit the headlines in 2019, following an intrusion at the system management company Solar Winds, which marked the start of one of the largest software supply chain attacks in history.
In 2021, a similar attack involving IT management company Kaseya exploited a zero-day vulnerability in the company’s remote management software to carry out ransomware attacks that are thought to have impacted some 1,500 businesses and resulted in a $70mn ransom demand.
In June 2023 a North Korea hacking group penetrated software-as-a-service provider JumpCloud in order to target cryptocurrency companies, according to media reports. Blockchain analytics firm Chainalysis said last year that North Korean-linked groups stole an estimated $1.7bn worth of digital cash across multiple hacks.
Supply chain cyber-attacks were typically associated with sophisticated nation state hacker groups, but increasingly they are being used by RaaS groups to launch mass ransomware attacks.
Much like the recent MOVEit extortion, ransomware gangs are now alive to the opportunities to exploit the interconnectivity of digital and physical supply chains and will target organizations with weak cyber security in order to infiltrate other companies elsewhere in the supply chain, circumventing more robust cyber security.
Mass cyber attacks raise accumulation concerns
2023 has seen several mass ransomware extortion attacks, where RaaS groups exploit vulnerabilities in software and the interconnectivity of digital supply chains to exfiltrate data and demand ransoms from hundreds, if not thousands of companies.
In addition to the recent MOVEit attack, in which the Clop ransomware group used a zero-day vulnerability in widely used file transfer software, RaaS groups have launched other such attacks in 2023.
Earlier this year Clop also used a zero-day flaw in the GoAnywhere file transfer software to steal data from over 130 companies.
In another separate attack, threat actors exploited a known vulnerability in unpatched VMware ESXi servers, compromising 3,800 servers worldwide
AI, IoT & skills shortage to fuel future cyber-attacks

Artificial intelligence (AI) is widely expected to power future ransomware attacks, with automated attack processes, more convincing phishing, and faster malware development. However, it could also enhance cyber security, with more effective and faster detection and threat intelligence.
Threat actors are already using AI-powered language models like ChatGPT to write code.
Generative AI can help less technically proficient threat actors write their own code or create new strains and variations of existing ransomware, potentially increasing the number of attacks they can execute.
AI can be used to carry ore automated attacks, as well as develop new techniques to steal or poison data. When you think about the potential to combine AI with the proliferation of the IoT and the speed of 5G, for example, we may have a serious issue on the horizon (see Internet of Things in Insurance and How IoT Technology Reshapes Business?).
Voice simulation software has been a recent addition to the cyber criminal’s arsenal. In 2019 the CEO of a British energy provider transferred €220,000 to a scammer after they received a call from what sounded like the head of the unit’s parent company, asking them to wire money to a supplier. The voice was generated using AI.
In August 2023, researchers at the Google-owned cybersecurity company Mandiant documented the first known instances of deepfake video technology designed and sold for phishing scams.
The going rate was as little as $20 per minute, $250 for a full video or $200 for a training session, although the researchers were unable to confirm that the services they identified on hacker forums were legitimate or whether a deepfake had been used in any scam.
Mobile devices expose personal and corporate data

Lax security and the mixing of personal and corporate data on mobile devices is making for an attractive target for cyber criminals.
Allianz Commercial has seen a growing number of incidents caused by poor cyber security around mobile devices. During the pandemic many organizations enabled new ways of accessing their corporate network via private devices, without the need for multi-factor authentication (MFA). This also resulted in a number of successful cyber-attacks and large claims.
Cyber criminals are now targeting mobile devices with specific malware in order to gain remote access, steal login credentials, or to deploy ransomware.
The roll out of 5G technology is also an area of potential concern. 5G will power more connected devices, including more sophisticated applications, such as driverless or assisted vehicles and smart cities. IoT devices do not have a good track record when it comes to cyber security.
Many IoT devices are not inherently secure, while the sheer number of these devices globally and the addition of AI could result in a very serious cyber threat. Many of these devices are easily discoverable and will not have MFA mechanisms.
Cyber security skills shortage affects cost and frequency

A growing shortage of cyber security professionals will increasingly complicate cyber security efforts, potentially increasing the chances of successful attacks in the future.
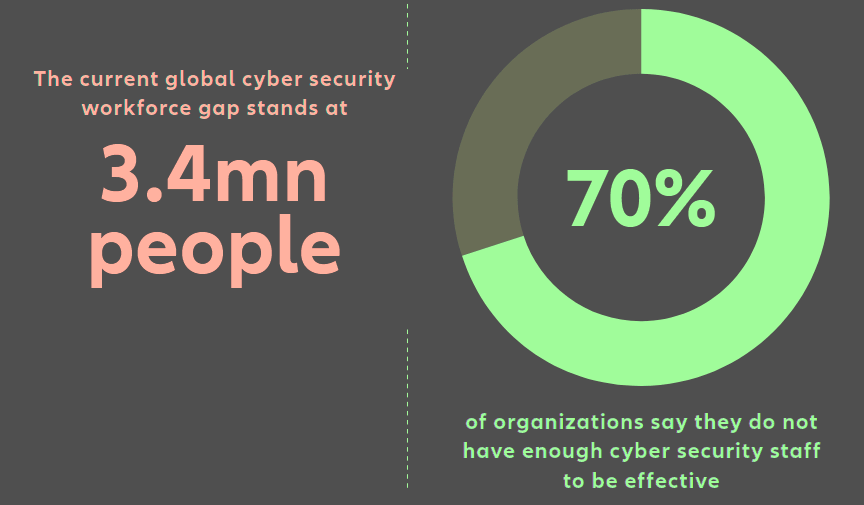
The current global cyber security workforce gap stands at 3.4 million people, according to the ISC2, non-profit member organization for cyber security professionals, with demand for cyber professionals growing twice as fast as supply.
Some 70% of organizations say they do not have enough cyber security staff to be effective. Gartner predicts that a lack of talent or human failure will be responsible for over half of significant cyber incidents by 2025.
Global cyber security workforce gap
The shortage of cyber security experts also impacts the cost of responding to a cyber incident. According to the IBM Cost of a Data Breach Report 2023, organizations with a high level of security skills shortage had a $5.36mn average data breach cost, around 20% higher than the average cost.
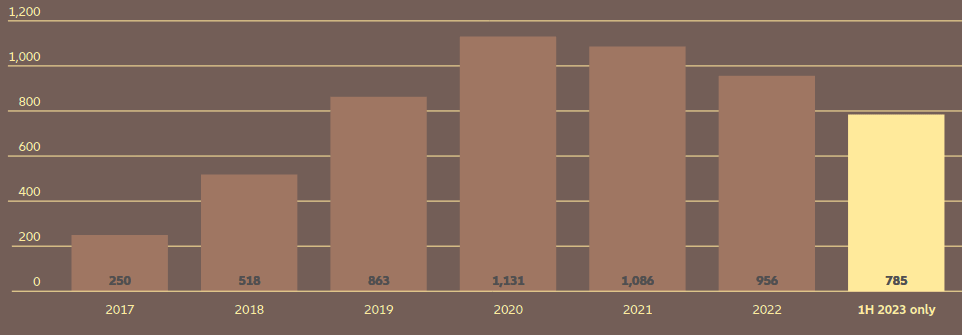
Cyber claims frequency: stabilization trend
Cyber claims frequency picked up again during the first half of 2023, although improved cyber security over the past two years has helped control first party losses and improve the overall quality of risk.
The attackers are now back, and focused again on Western economies, with more powerful tools, enhanced processes and attack mechanisms
Following a significant spike in ransomware losses in 2020 and 2021, the frequency of cyber insurance claims stabilized last year, reflecting improved cyber security and risk management actions among insured companies – such as the use of multifactor authentication or more effective backup strategies which made encryption-based ransomware less effective and reduced the business interruption impact.
At the same time, law enforcement agencies targeting ransomware gangs and the Ukraine Russia conflict are thought to have curtailed the activities of threat actors.
Ransomware groups have changed tactics, with an increase in data exfiltration, and mass cyber-attacks that have exploited weaknesses in IT supply chains.
The MOVEit mass cyber-attack, which affected over a thousand companies earlier this year, for example, contributed to the increase in the frequency of claims in 2023, affecting multiple policyholders simultaneously.
Number of cyber-related claims per year
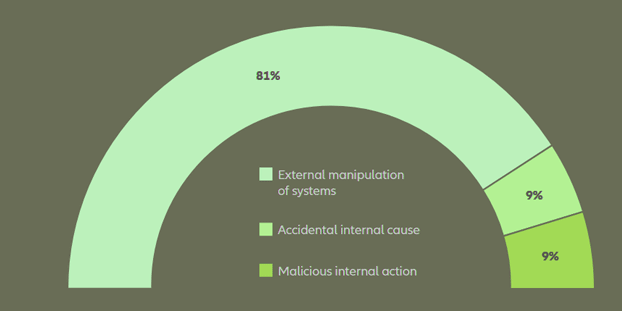
Ransomware and extortion-based attacks remain the largest source of cyber insurance claims by volume and frequency, accounting for more than 80% of claims from standalone cyber policies alone.
Cause of loss by value of cyber claims
Based on the analysis of 3,366 claims worth €612mn (including the share of other insurers)
Privacy and liability risks on watch
In addition to extortion claims, there has also been an uptick in the number of data privacy claims in the US, related to biometric information, such as voice or fingerprint data, as organizations increasingly capture this to improve online security.
Many track personal information such as location, health or behavior, as part of their product and service offering, or to aid sales and marketing.
The US does not have federal law covering data privacy, but a number of states have implemented strict laws, such as the California Privacy Rights Act and the Illinois Biometric Information Privacy Act (BIPA). Meanwhile, the number of data privacy and data breach class action lawsuits continues to rise as plaintiffs see this as a potentially lucrative and expanding area of litigation.
Data exfiltration drive up cyber insurance claims costs
More sophisticated attacks and inflation are increasing the cost of large cyber losses. The size and complexity of an organization and its IT infrastructure is a key factor contributing to the cost of large cyber claims.
Once a cyber-attack progresses past a certain point, the combination of first party restoration costs, business interruption and third-party liability easily result in a large loss.
Business interruption remains the key loss driver for ransomware attacks, as it does for many forms of cyber-attack – Allianz analysis shows that it accounts for 50% of all cyber-related losses by value.
Allianz analysis of a number of larger insurance industry cyber losses (>€1mn) between 2019 and the end of the first half of 2023 shows that the proportion of cases in which data is exfiltrated increased from 40% in 2019 to 77% in 2022, with 2023 on course to surpass this.
Along with this increase in data exfiltration, first party recovery and response expenses are increasing, while the cost of notification and third-party liability can also be significant.

The average cost of a data breach in 2023 was $4.45mn, a 15% increase over three years, according to the IBM Cost of a Data Breach 2023 report.
Allianz analysis of claims notifications shows that breaches that were not detected and contained early, and therefore ultimately involve data exfiltration, can be as much as, or even more than, 1,000 times more expensive than those that were.
Exfiltration incidents carry a higher reputational risk and are a bigger drain on the resources of the company and leadership, making effective data breach response critical.
Allianz analysis of a number of larger insurance industry cyber losses (>€1mn) between 2019 and the end of the first half of 2023 shows that the proportion of cases becoming public increases from year to year. In 2019 this totaled 60%, rising to 85% in 2022, with 2023’s total on course to surpass this.
Early detection is key to combating emerging cyber threat

The vast majority of cyber-attacks are contained quickly and, if insured, often fall within policy deductible levels, or are not even notified.
According to Allianz analysis, just 2% of claims drive the overall loss amount, and in almost all cases these would have benefited from early detection.
Good data management is essential to mitigating the impact of data exfiltration attacks, as are a growing number of specialist services.
Prevention drives frequency, while detection determines severity. Some 90% ofincidents are contained early, and most cases stay within policy retention levels. However, if the attack is not stopped in the early stages, we rarely see them being caught during the next stages. Once the attacker has exfiltrated and encrypted it is too late and becomes very expensive.
The key to avoiding damaging cyber-attacks and mitigating losses is to detect an attack in its early stages, according to Daum. “With growing reliance on outsourcing and data flows between companies, and with the potential use of artificial intelligence by threat actors, protecting the perimeter of an organization will no longer suffice.
Companies cannot prevent. They can only reduce the number of attacks that surpass the first line of defense. There needs to be detection and response because it’s no longer possible to prevent every attack, no matter how much you invest in IT security. Companies need to catch these attacks before the next stage and prevent the most severe incidents that might bring their business to a halt and damage their reputation.
Human oversight and triage is also required to manage the flood of alerts, typically conducted in a SOC.
Time is key, when it comes to mitigating the impact of a ransomware incident, as business interruption and recovery costs quickly rack up once hackers have encrypted or stolen data.
The lion’s share of IT security budgets is currently spent on prevention, with around 35% of the budget directed to detection and response. However, the effectiveness of detection and response capabilities drives the size of loss.
Early detection technology is readily available and effective. Detection systems are constantly improving and can save lots of pain, decreasing detection and response times. This is something we look for in our cyber risk assessments and underwriting.
Companies should direct additional cyber security spend on detection and response, rather then add more layers to prevention.
We would not recommend that companies reduce budgets on prevention, rather they should just give IT security a budget to build up detection to the same level, if not more.
It should be an automatic end-to end mechanism that starts with prevention, then follows through with early detection and response.
Only one-third of companies discover a data breach through their own security teams, highlighting a need for better threat detection, according to IBM. Yet when attackers disclose a breach, it costs organizations an average of nearly $1mn more compared to internal detection.
Preparing for the worst

With increasing levels of data privacy regulation worldwide, good data management is also essential to mitigating the impact of data exfiltration attacks.
The costs of legal and specialist IT and breach response services are also on the rise, with increased rates and the challenge of having to deal with more complex attacks.
For example, with data exfiltration attacks it typically takes longer for vendors to figure out exactly what data has been stolen, which can be a very expensive process.
The cost of external experts is rising, which makes the cost of a claim more expensive. In the US, for example, a lawyer might have charged €1,000 per hour a few years back, and today they would charge €1,500 for a similar case.
And asthe complexity of claims increases, external experts spend more time resolving issues, so we see not only higher rates, but more people working on these more complex claims for longer.
With specialist data breach services in high demand, and the rise in data exfiltration attacks, organizations need to secure the services of vendors in advance. One recent supply chain attack claim for a European manufacturer in the US resulted in total extortion demands in the double-digit millions. And in that case, the insured was not sure which data had been compromised, requiring very expensive e-discovery costs.
Vendor services that come with most cyber insurance policies can help manage data exfiltration attacks and mitigate the financial and regulatory impact.
For example, breach coaches, which are popular in the US, can help mitigate the costs of a data breach, with more informed decisions around when to notify and who will need to
be notified. In the heat of a ransomware event with data exfiltration, breach coaches can help with specialist legal advice that can avoid unnecessary expenses and avoid non-compliance with privacy laws.
Reliance on outsourcing puts small and mid-sized firms at risk
Small to mid-sized companies may be more at risk of cyber-attack due to their reliance on outsourcing for services, including managed IT and cyber security providers.
As large companies have hardened their cyber security, cyber criminals are increasingly targeting smaller companies, which often have less financial resource to invest in prevention and response capabilities.
According to Mastercard’s RiskRecon, data breaches at small businesses globally jumped 152% during 2021, while during the same time period breaches at larger organizations rose 75%. More than half (54%) of SMEs in the UK had experienced some form of cyber-attack in 2022, up from 39% in 2020, according to Vodafone.
If a small company with poor controls or inadequate risk management processes suffers a significant cyber incident, the reality is there is a chance it might not survive in the long run.
In recent years, progress has been made, and there has been good collaboration between insurers, brokers and clients, but ultimately more awareness of, and risk management education about, cyber risk is still needed, and the insurance industry has a responsibility to help smaller companies with this process.
Mid-sized businesses can take a proactive approach to tackle cyber threats by first ensuring that their cyber security strategy effectively identifies their most crucial information system assets.
Then, they should proceed to deploy appropriate detection tools and techniques tailored to uncover and nullify potential threats attempting to gain network access. These measures encompass the use of detection and monitoring software both at the network perimeter and on endpoints, often involving collaboration with cyber security service partners.
…………….
AUTHORS: Michael Daum – Global Head of Cyber Claims at Allianz Commercial, Rishi Baviskar – Global Head of Cyber Risk Consulting, Allianz Commercial, Tresa Stephens – Head of Cyber, Tech & Media – North America at Allianz Commercial, Marisa Anthony – Senior Complex Claims Handler, Cyber, Allianz Commercial, Jens Krickhahn – Regional Practice Leader, Cyber Insurance, at Allianz Commercial








