The Cost of Cybercrime study combines research across 11 countries in 16 industries. Accenture Security interviewed 2,647 senior leaders from 355 companies and drew on the experience to examine the economic impact of cyberattacks. The cost of cybercrime study helps to quantify the economic cost of cyberattacks by analyzing trends in malicious activities over time.
By better understanding the impact associated with cybercrime, organizations can determine the right amount of investment in cybersecurity.
According to Top Cybercrime Predictions, Cybercriminals love to exploit seasonal opportunities, and consumers are facing a perfect storm of rising prices in the middle of the busiest shopping season of the year. Looking back at the costs of cybercrime to date is helpful—but looking forward, so that business leaders know how to best target their funds and resources, is even more beneficial.
The 2023 World Economic Forum’s (WEF) Global Risks Report put cybersecurity in the current and future top 10 risks globally.
The cost of cybercrime is projected to hit an annual $10.5 trillion by 2025, according to Cybersecurity Ventures.
Gartner analysts predict that over the next two years, 45% of global organizations will be impacted in some way by a supply chain attack.
How does users and technologies protected against cyberattacks?

In an ever-changing digital landscape, it is vital to keep pace with the trends in cyber threats (see How to Reduce the Impact of Cybercrime?). The frequency and severity of cyberattacks are ever increasing. Data breaches to steal personal information occur daily, but only the largest make the news.
In the wake of the pandemic, businesses have seen the power of tech transform industries overnight, as digitalization became the global rescue package.
But research by the World Economic Forum indicates that only 4% of organizations are confident that “users of connected devices and related technologies are protected against cyberattacks.” This vulnerability can potentially have serious consequences for businesses, often in the form of major operational, financial, legal and reputational damage.
A number of key cybersecurity recommendations emerged from Davos, but they all pointed in the same direction—collaboration, collaboration and more collaboration. Working together across international borders and throughout every part of the supply chain is crucial to tackling an issue as widespread as digital security.
Regulation and governance are essential tools, but to date, they’ve struggled to keep up with the rapid advancements being made by the tech industry.
In the EU, the Cyber Resilience Act places new requirements on manufacturers and suppliers to prioritize cybersecurity throughout the life cycle of hardware and software, as well as supporting businesses and consumers to use technology more securely.
Every international jurisdiction has tackled this issue in one guise or another, but cybercrimes are borderless, and so must be the response. International, cross-sector cooperation on this issue must be the next step.
The Cybercrime Evolution

Analytics found that cyberattacks are changing due to:
• Evolving targets: Information theft is the most expensive and fastestrising consequence of cybercrime—but data is not the only target. Core systems, such as industrial control systems, are being hacked in a powerful move to disrupt and destroy.
• Evolving impact: While data remains a target, theft is not always theoutcome. A new wave of cyberattacks sees data no longer simply being copied but being destroyed—or changed—which breeds distrust. Attacking data integrity is the next frontier.
• Evolving techniques: Cybercriminals are adapting their attackmethods. They are using the human layer—the weakest link—as a path to attacks, through increased phishing and malicious insiders. Other techniques, such as those employed by nation-state attacks to target commercial businesses, are changing the nature of recovery, with insurance companies trying to classify cyberattacks as an “act of war” issue.
Nation-state, Supply Chain and Information Threats
Organizations of all sizes, geographic locations and industries globally have been plagued by the financial, reputational and regulatory consequences of cybercrime. In the last year, we saw a significant rise in economic espionage, such as the theft of high-value intellectual property by nation-states (see 2023 Global Insurance Ranking of Cyber Insurers by Premiums).
Extended supply chain threats are also challenging organizations’ broader business ecosystem.
Cyberattackers have slowly shifted their attack patterns to exploit third- and fourth-party supply chain partner environments to gain entry to target systems—including industries with mature cybersecurity standards, frameworks, and regulations.
New regulations aim to hold organizations and their executives more accountable in the protection of information assets and IT infrastructure. The General Data Protection Regulation (GDPR) came into force on May 25, with potential fines up to US$23 million or four percent of annual global revenues. The French data regulator (CNIL) issued the largest GDPR fine so far—US$57 million (see Cyber Risk Detection, Insurance & Cyberattack Lifecycle).
New Cyber risks from innovation and growth

According to the Accenture report “Securing the Digital Economy,” businesses have never been more dependent on the digital economy and the Internet for growth. Fewer than one in four companies relied on the Internet for their business operations 10 years ago; now, it is 100%.
A trustworthy digital economy is critical to their organization’s future growth according to 90% of business leaders—but the drive for digital innovation is introducing new risks.
While Internet dependency and the digital economy are flourishing, 68% of business leaders said their cybersecurity risks are also increasing. Almost 80% of organizations are introducing digitally fueled innovation faster than their ability to secure it against cyberattackers.
No wonder, then, that cyberattacks and data fraud or theft are now two of the top five risks CEOs are most likely to face according to the latest World Economic Forum report on global risks.
Many employees are often the root cause of successful cyberattacks
Whether by accident or intent, many employees are often the root cause of successful cyberattacks. Executives polled in the Accenture State of Cyber Resilience survey identified the accidental publication of confidential information by employees and insider attacks as having the greatest impact, second only to hacker attacks in successfully breaching their organizations (see Cyber Insurance Risks & Cyberattacs in the Russia-Ukraine War).
Today, the security function is largely centralized and its staff are rarely included when new products, services, and processes—all of which involve some sort of cyber risk—are being developed.
Such a silo’ed approach can result in a lack of accountability across the organization and a sense that security is not everyone’s responsibility.
Only 16% of CISOs said employees in their organizations are held accountable for cybersecurity today. Providing ongoing training and skill reinforcement—for instance, with phishing tests—is essential, alongside training and education.
Employees need the tools and incentives to help them to define and address risks. New work arrangements—greater use of contractors and remote work—make the need for employee training more urgent.
Even so, training employees to think and act with security in mind is the most underfunded activity in cybersecurity budgets.
To embed cybersecurity into the fabric of the organization and be effective against any insider threats, organizations must bring together human resources, learning and development, legal and IT teams to work closely with the security office and business units.
Benchmarking Cybersecurity Investment

In the backdrop of this challenging environment, our research reveals that cybercrime is increasing in size and complexity. Based on the trends identified in previous publications, this may not come as a surprise.
However, this year our report offers an additional perspective—a forward looking projection of the economic value at risk from future cyberattacks in the next five years.
More Attacks and Higher Costs
As the number of cyberattacks increase, and take more time to resolve, the cost of cybercrime continues to rise.
In the last year, we have observed many stealthy, sophisticated and targeted cyberattacks against public and private sector organizations.
Combined with the expanding threat landscape, organizations are seeing a steady rise in the number of security breaches—from 130 to 145.
For purposes of this study, we define cyberattacks as malicious activity conducted against the organization through the IT infrastructure via the internal or external networks, or the Internet.
The Value at Risk from Cybercrime

Managing cybercrime effectively involves organizations seeking to secure more than their own four walls. As noted earlier, extended supply chains are under threat as cyberattackers shift their attack patterns to business partner environments as an entry point into target systems.
The total value at risk from cybercrime is US$5.2 trillion over the next five years.
Indirect attacks of this nature could account for 23% of the total value at risk for organizations over the next five years. Organizations need to work with partners in their supply chain to collaborate on protecting the entire business ecosystem.
Our study finds the extent of the economic value that may be at risk if security investments are not made wisely. We show that the size of opportunity varies by industry, with High tech subject to the greatest value at risk—US$753 billion—over the next five years, followed by US$642 bn for Life Sciences and US$505 bn for the Automotive industry.
Assessing Levels of Investment

There is another way to view value at risk—seeing it as a revenue-earning opportunity that is linked to improvements in cybersecurity protection. As protection improves, fewer attacks will breach defenses and the cost of cybercrime reduces.
Trust, the fuel which drives the digital economy, can also strengthen the organization’s standing and lead to new revenue-generating opportunities with customers.
Confidence in the organization is especially helpful when competitors do not inspire the same levels of trust. In an expanding threat landscape with more sophisticated attacks, the key question is: How can organizations refocus resources to make the greatest improvements in cybersecurity protection?
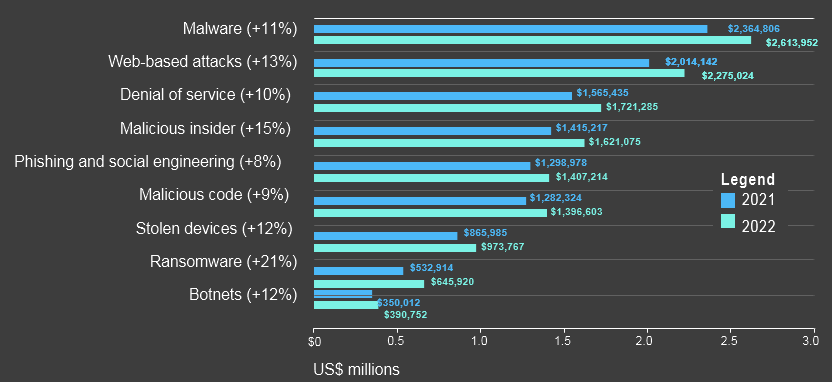
Malware is the most expensive attack type for organizations. The cost of malware attacks has increased by 11% over the year, and the cost of malicious insider attacks has increased by 15%
Our in-depth interviews enable us to not only assess the detailed business impact of each type of cybersecurity attack, but also to understand where and how enabling security technologies can make a difference.
Improving Cybersecurity Protection
Armed with this knowledge, organizations can better guide their security investments toward technologies with the largest potential cost savings. Further, they can focus those technologies on the internal activities with the greatest strategic impact on improving cybersecurity protection.
Every Type of Attack Is More Expensive
The total annual cost of all types of cyberattacks is increasing. Malware and Web-based attacks continue to be the most expensive. The cost of ransomware (21%) and malicious insider (15%) attack types have grown the fastest over the last year.
Average annual cost of cybercrime by type of attack
The Impact of Cyberattacks Is Rising
The rapid growth of information loss over the last three years is a worrying trend. New regulations, such as GDPR and CCPA, aim to hold organizations and their executives more accountable for the protection of information assets and in terms of using customer data responsibly.
Future incidents of information loss (theft) could add significantly to the financial impact of these attacks as regulators start to impose fines.
The cost of business disruption—including diminished employee productivity and business process failures that happen after a cyberattack—continues to rise at a steady rate
Malware, Web-based attacks, and denial-of-service attacks are the main contributing factors to revenue loss.
Understanding the main consequences of cybercrime is helpful, but there is insufficient detail in that finding to help target resources toward the sources of these attacks.
Business disruption continues to grow steadily and is the second largest consequence of cybercrime. Resources should be targeted on denial-of-service attacks, malicious insiders and malware attacks to reduce this cost.
Attention should also be given to the rate of growth in each type of attack. The financial consequences of ransomware have increased 21% in the last year alone. Although one of the smaller costs of cybercrime overall, organizations should not overlook this fast-growing threat.
Targeted Investments Tackle Cybercrime

Armed with an understanding of the main consequences of each type of cyberattack, organizations may want to consider how they can improve cybersecurity protection against these threats.
We have already illustrated the underlying types of attack where organizations need to focus. Enabling security technologies also have an important role to play in supporting internal cybersecurity efforts.
We asked organizations to report the amount they spend to discover, investigate, contain and recover from cyberattacks.
Also included in the calculation are the expenditures that result in after-the-fact activities and efforts to reduce business disruption and the loss of customers.
The expenditure does not include outlays and investments made to sustain an organization’s security posture or compliance with standards, policies and regulations.
Investigation expenditures have decreased in three of the four years of analysis. The decreases in spend are due to improvements in forensic analysis capabilities and threat hunting tools.
Another factor that is influencing the reduction in spend is the expanded use of cloud services, which make the investigation of cyber threats more efficient. Spend on containment has steadily increased over the period. The rise in spend is mainly due to the increasing complexity and sophistication of attacks, which makes the containment of the cyberattack more difficult and time consuming.
Security Technologies Can Make a Difference
To better understand the effectiveness of investment decisions, we analyzed nine enabling security technologies to assess current levels of investment and adoption, as well as understand their value in terms of cost savings to the business.
Net technology savings
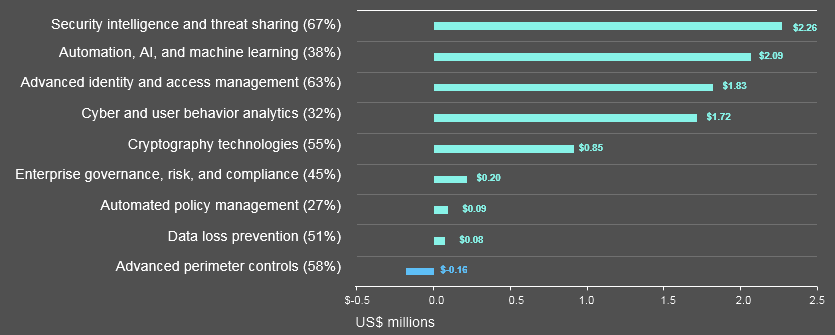
Advanced identity and access management is already widely adopted by 63% of organizations and provides a substantial net cost saving —US$1.83 million—after deducting the amount of money invested in the technology.
All organizations could benefit from the reduction in cybercrime cost enabled by further investment in advanced identity and access management.
Security intelligence and threat sharing is widely deployed by 67% of companies and provides the greatest cost savings when compared with levels of spend (US$2.26 million). It is not only an important enabling technology for both discovery and investigation activities, but also it is an important source of information to understand threats and better target resources against anticipated attacks.
Forensic cyber and user behavior analytics also present an opportunity for cost savings—US$1.72 million—with discovery and investigation activities.
The main driver for the rise in containment costs of cyberattacks
The main driver for the rise in containment costs is the increasing complexity and sophistication of cyberattacks.
Another factor is the expansion of compliance and regulatory requirements. Enterprise governance, risk and compliance technology and automated policy management all have a marginal impact on lowering the cost of cybercrime, so careful management and appropriate levels of investment may be required to improve the efficiency and cost of regulatory compliance.
Automation, including artificial intelligence and machine learning, already account for some of the downward trend in spend on recovery activities.
Automation offers the second highest net savings of US$2.09 million, once investment costs are considered. Levels of adoption are still relatively low and more organizations could benefit from the savings generated. These technologies could begin to address the shortage in skilled security staff by supplementing existing skills and capabilities.
The costs associated with information loss is rising faster than any other consequence of cybercrime. The extensive use of cryptography technologies provides a healthy net saving of US$0.85 million. Although the return is lower, organizations should also consider the use of data loss prevention technologies where appropriate.
The situation with advanced perimeter controls deserves further discussion.
The average level of investment in this enabling technology is US$1.4 million —the highest level of investment of all the technologies in our analysis.
Advanced perimeter controls also return a healthy cost saving of US$1.2 million. With the exponential growth of the Internet of Things (IoT), and the movement of more processing power to “the edge”, organizations must be careful to maintain their advance perimeter controls in line with their risk of attack.
Unlocking Cybersecurity Value

Security should to be a core competency across the organization and embedded in all that a business is and does. From people to data to technologies, every aspect of a business invites risk. Despite their investments, business leaders still need to improve the economic value from their cybersecurity strategies.
3 Steps to Unlock Cybersecurity Value
- Prioritize protecting people-based attacks: Counteracting internalthreats is still one of the biggest challenges facing business leaders today. Increases in phishing, ransomware and malicious insider attacks mean that greater emphasis needs to be on nurturing a security-first culture. Accountability is key. Training and education are essential to reinforce safe behaviors, both for people within the organization and across the entire business ecosystem. Partners, third parties and relationships are growing as a result of conducting business electronically. Organizations should work with these ecosystem partners to jointly protect and defend their operations. The people involved are not always the people within an organization.
- Invest to limit information loss and business disruption: Information is the lifeblood of any organization—whether related to customers, employees, products, business processes or services. As new privacy regulations, such as GDPR and CCPA, extend considerable fines for non-compliance, the onus is on organizations to take a responsible attitude to their critical information. Information protection is at the heart of trustworthy business practices, and it is essential to defend against business disruption. Taking a data-centric approach to security, adopting data loss prevention technologies and using cryptographic technology extensively can all help to reduce the cost of cybercrime. Enhancing security measures around the handling, maintenance and sharing of information can shift an organization’s approach to information loss from damage limitation to robust proprietary practices.
- Target technologies that reduce rising costs: Organizations shouldmanage the largest component of spend, the cost of discovering an attack. Unsurprisingly, as the number of cyberattacks grows, so discovery costs are rising—and breakthrough technologies could be the answer to finding and reversing this increasing expense. Investments in enabling security technologies, such as security intelligence and threat sharing, can help to reduce the cost of cybercrime. Cloud services can make the investigation of cyber threats more efficient. Automation and advanced analytics can be used to investigate cybercrime and enhance recovery efforts, as well as being applied to supplement the work of scarce specialist security personnel.
……………..
AUTHORS: Kelly Bissell – Global Managing Director Accenture Security, Ryan LaSalle – North America Lead for Accenture Security, Paolo Dal Cin – Accenture Security Global Lead








